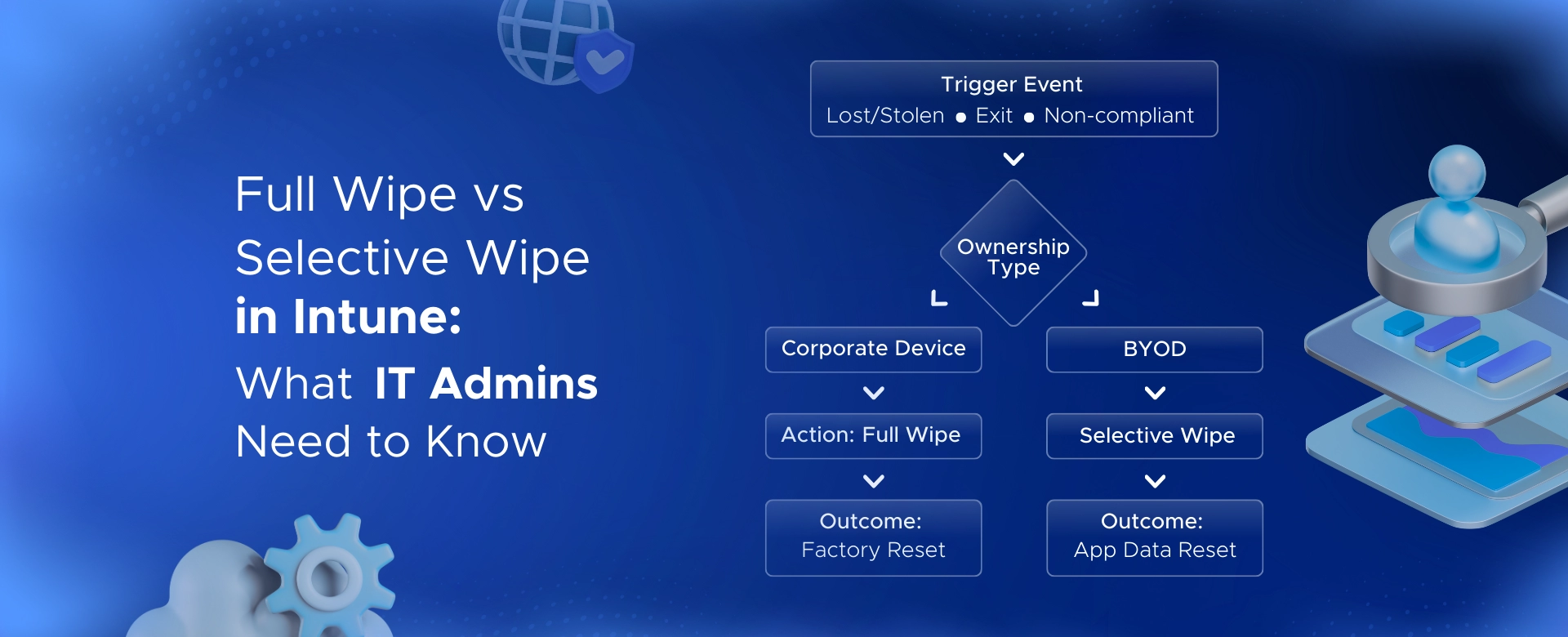
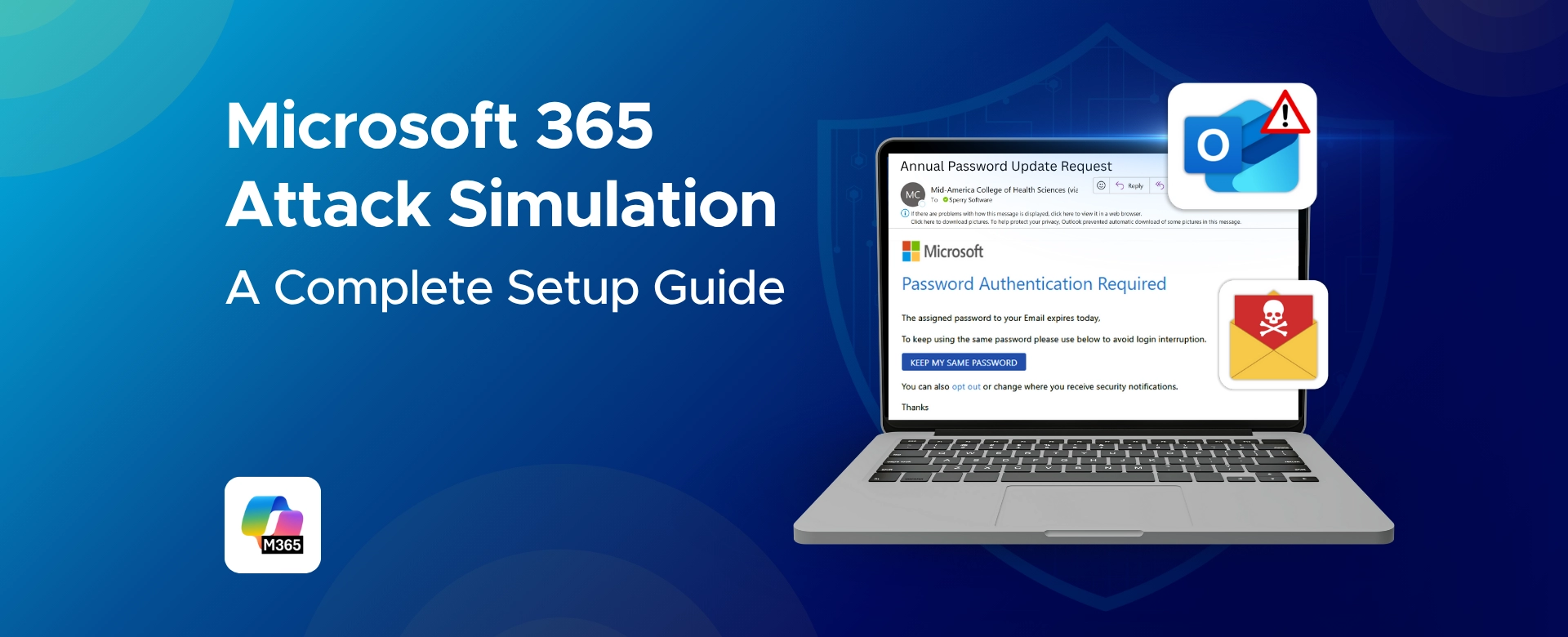
Learn how Intune full wipe and selective wipe work, when to use them, and best practices for secure device management in BYOD and corporate environments.
Main Menu
Cloud Services
Collaboration and Communication
Security and Compliance
Automation and Development
Digital Workspace
Artificial Intelligence
Overall Microsoft 365 Services
Main Menu
Starfleet Stash App
Asset & Inventory Management App
Penthara Org Chart
- Cloud Services
- Collaboration and Communication
- Security and Compliance
- Automation and Development
- Digital Workspace
- Artificial Intelligence
- Overall Microsoft 365 Services
- Starfleet Stash App
- Asset & Inventory Management App
- Penthara Org Chart