- How are controls scored?
- What does [Not Scored] mean?
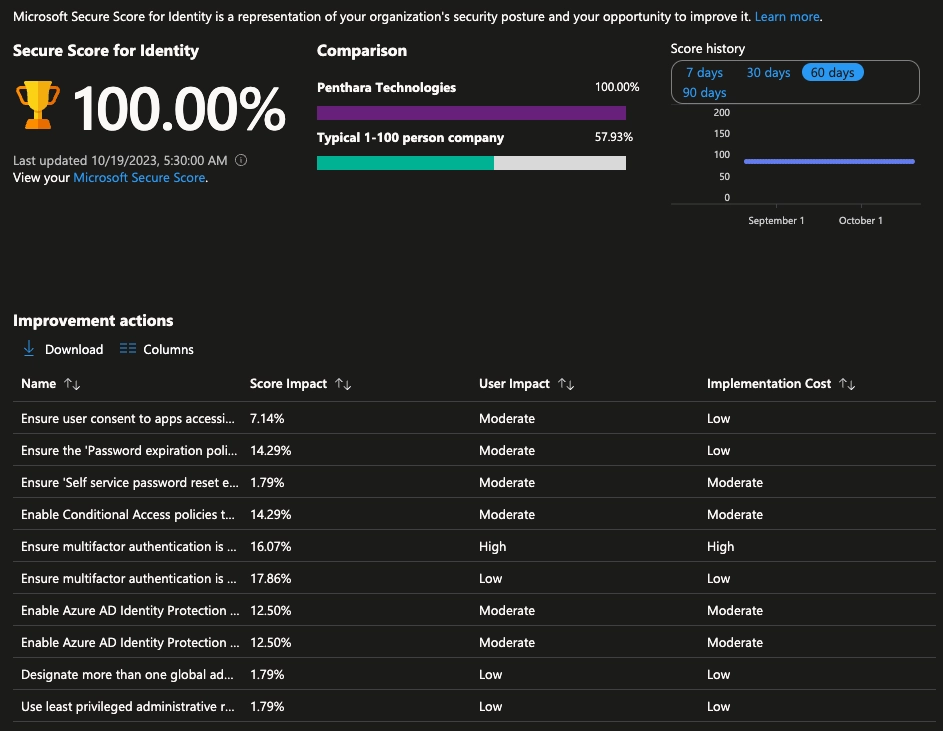
- How often is my score updated?
- How does the identity secure score relate to the Microsoft 365 secure score?
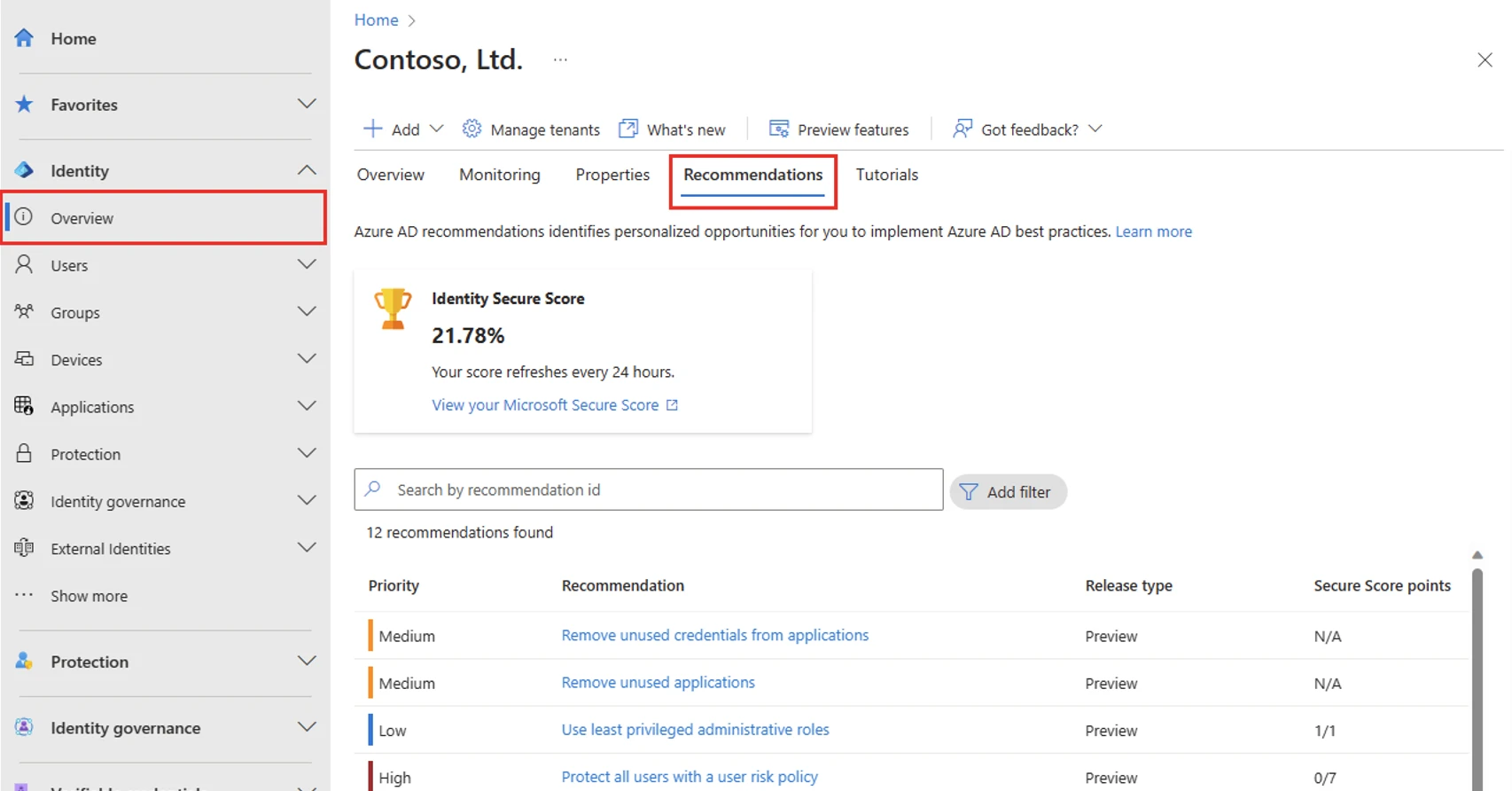
- How are controls scored?
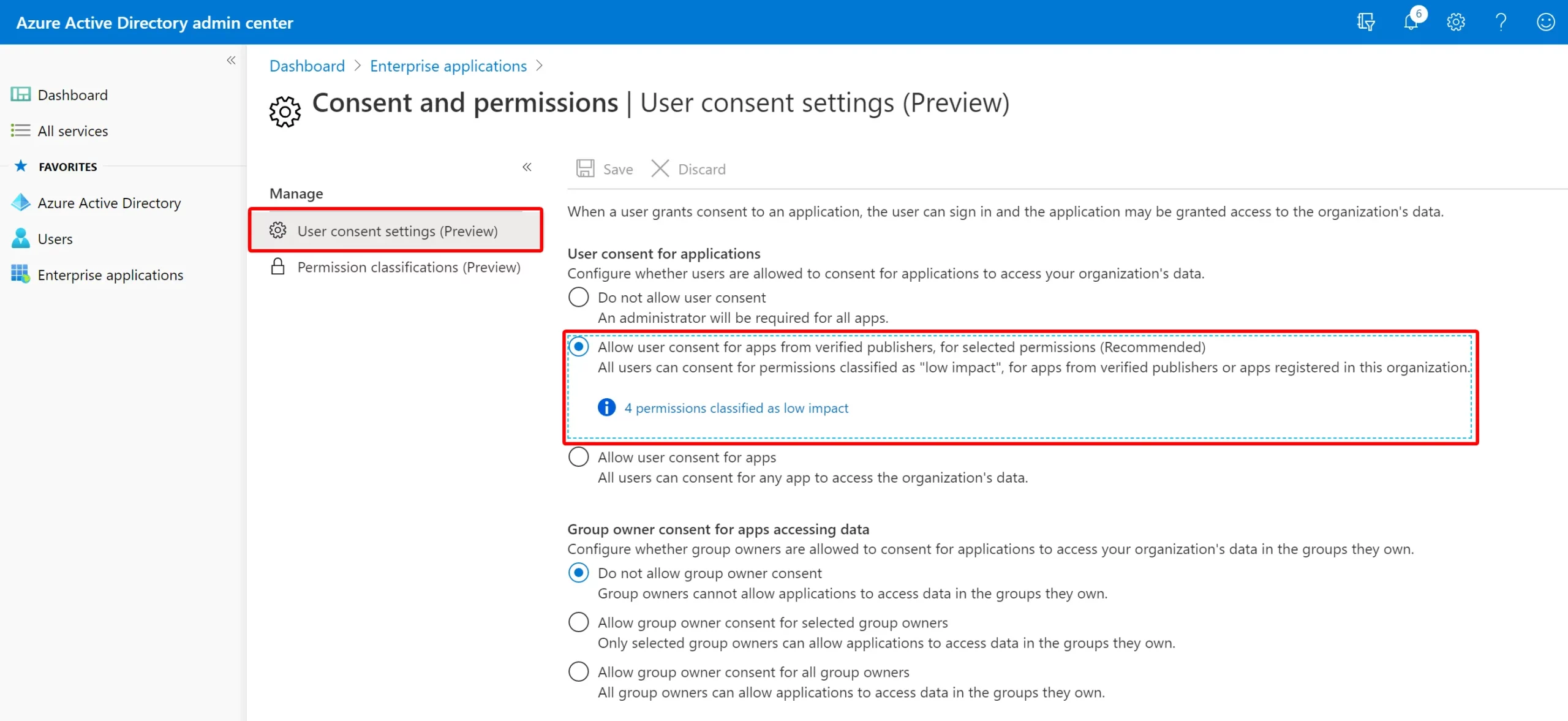
There can be two ways for controls scored. One involves binary fashion - you get 100% of the score if you have the feature or setting configured based on our recommendation.
The second involves the calculation as a percentage of the total configuration - if the improvement recommendation states there's a maximum of 10.71% increase if you protect all your users with MFA and you have 5 of 100 total users protected, you're given a partial score around 0.53% (5 protected / 100 total * 10.71% maximum = 0.53% partial score).
- What does [Not Scored] mean?
There will be some actions labeled as [Not Scored] that you can still perform to improve your security but won’t gain any score.
- How often is my score updated?
The score is calculated once per day (around 1:00 AM PST).
If you make any changes, the score will automatically update the next day. It may take up to 48 hours for a change to be reflected in your score. Also, don’t be alarmed if your score fluctuates sometimes, our years of experience tells us that this happens very rarely when buggy code gets to production and Microsoft has to fix it – during this time we see scores fluctuating even though nothing changed in your tenant.
- How does the identity secure score relate to the Microsoft 365 secure score?
The Microsoft secure score contains five distinct control and score categories:
- Identity
- Data
- Devices
- Infrastructure
- Apps
The identity secure score represents the identity part of the Microsoft secure score. This overlap means that your recommendations for the identity secure score and the identity score in Microsoft are the same.