Q1. How do I enable and configure idle session sign-out in Microsoft 365?
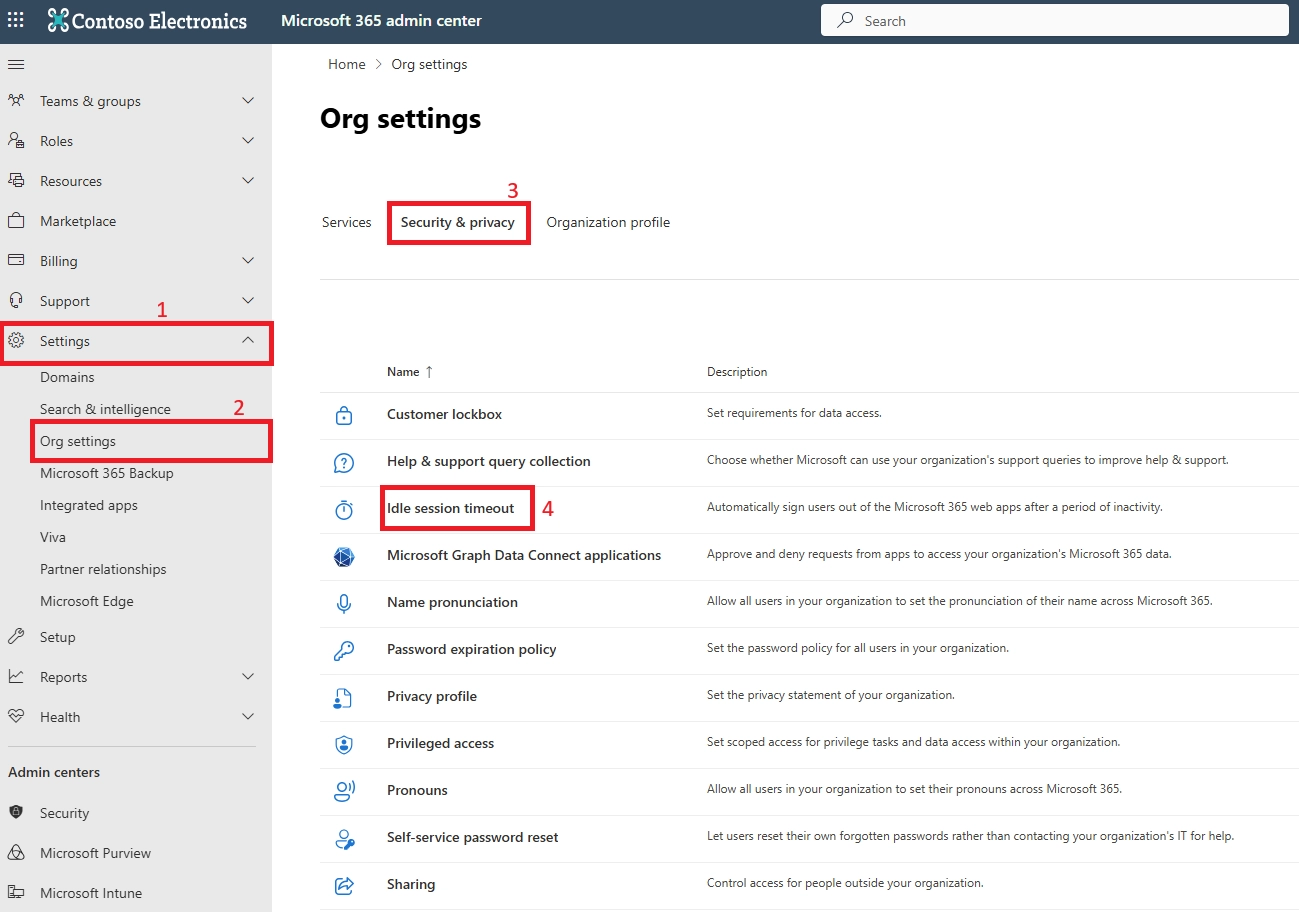
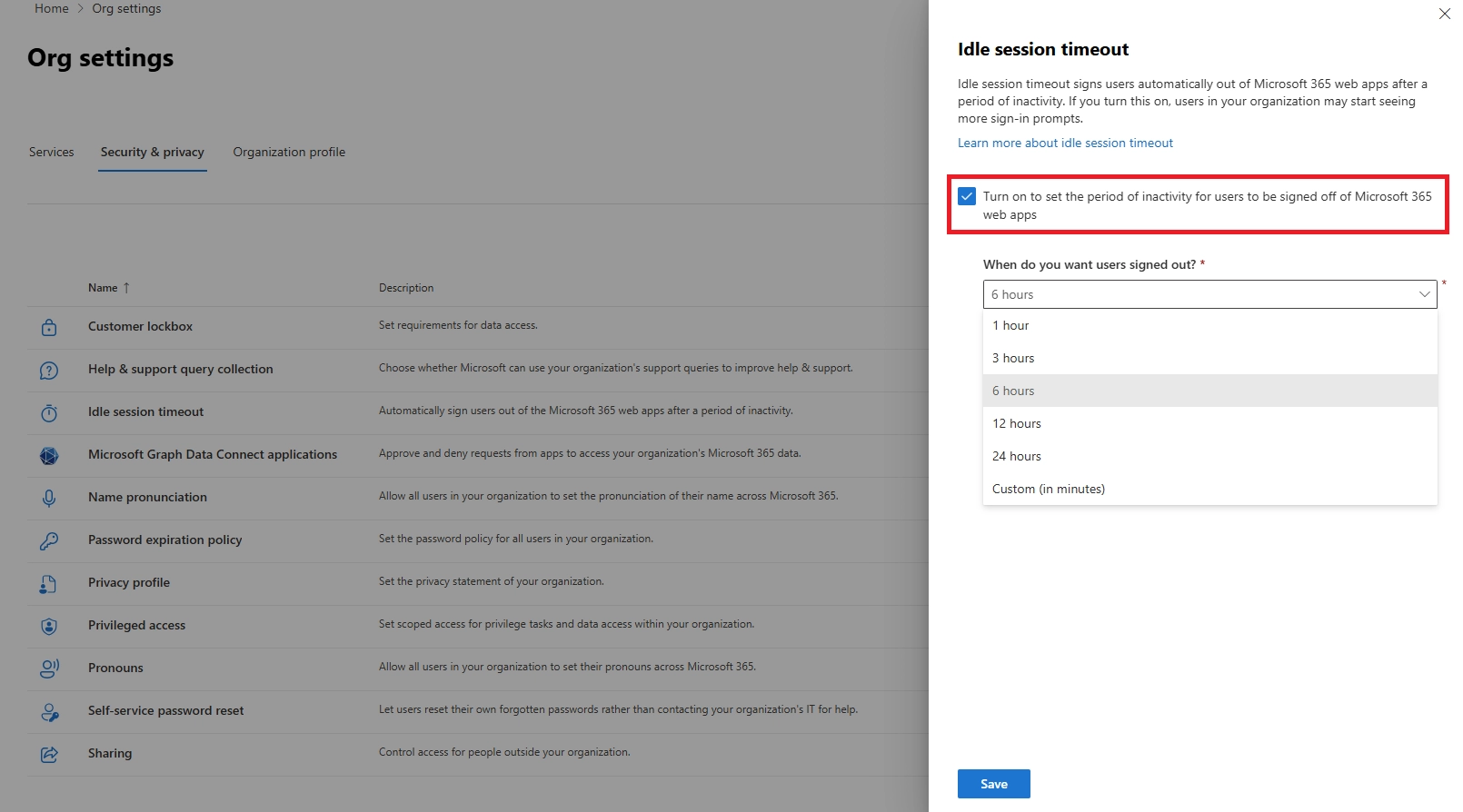
You can configure this in the Microsoft 365 Admin Center under Settings > Org Settings > Security & Privacy > Idle Session Timeout. From there, you set how long users can remain inactive before being signed out automatically.
Q2. Which Microsoft 365 administrator roles can configure session timeout policies?
Typically, roles like Global Admin, Security Admin, Application Admin, or Cloud Application Admin have permissions to manage these settings.
Q3. What idle timeout durations can I set in Microsoft 365?
You can set a timeout duration anywhere between 5 minutes to 1440 minutes (24 hours), depending on your organization’s security needs.
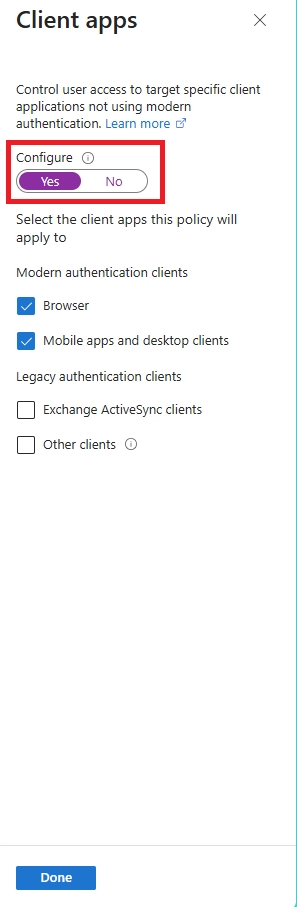
Q4. Which Microsoft 365 web apps and devices does the idle session timeout apply to?
It only affects browser-based apps such as:
- Outlook Web App (OWA)
- SharePoint Online
- OneDrive for Business
- Office.com
- Word, Excel, and PowerPoint on the web
- Microsoft 365 Admin Center
Desktop and mobile apps are not affected.
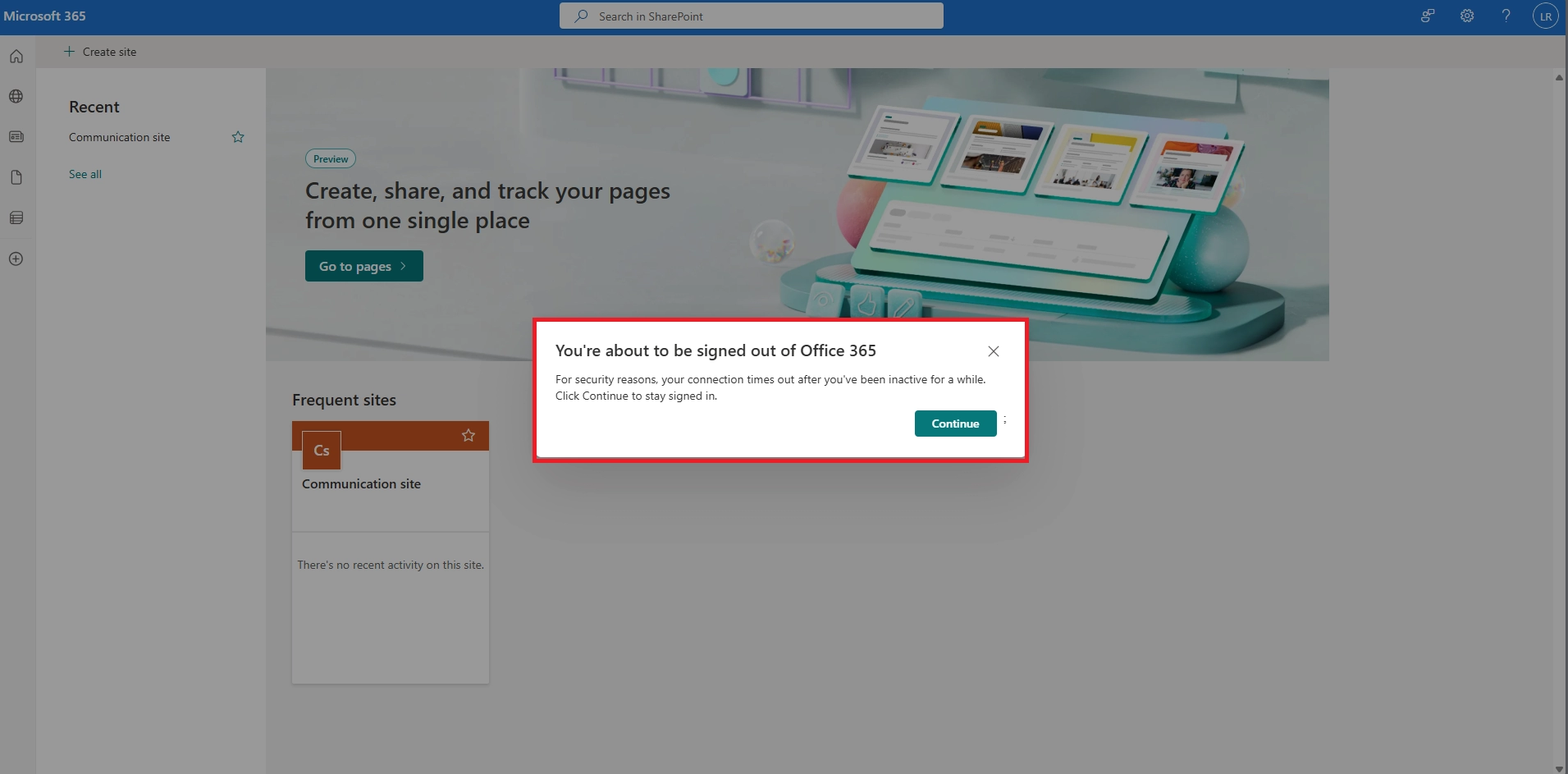
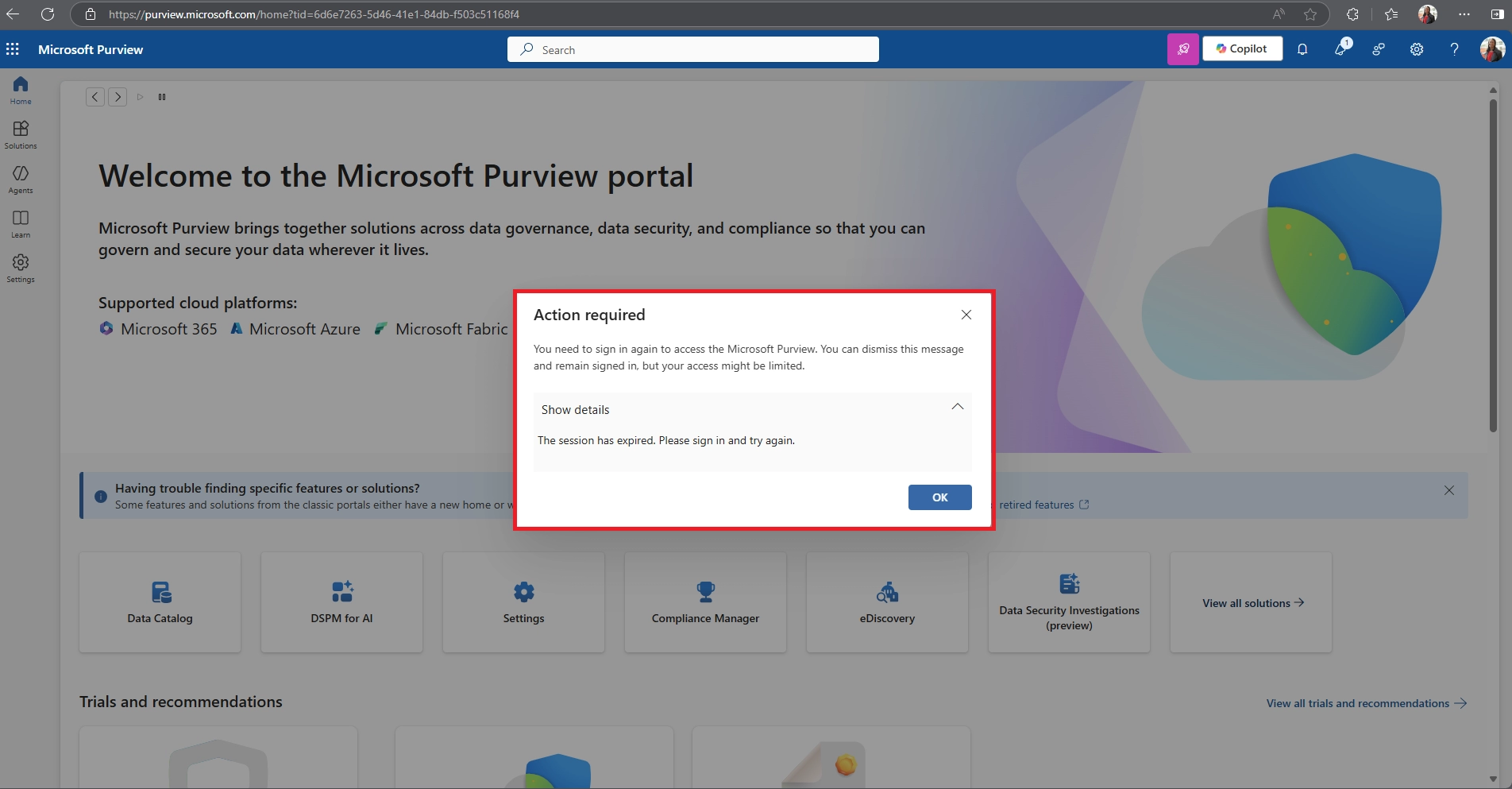
Q5. Why am I being signed out of Microsoft 365 apps unexpectedly or too often?
This could be due to:
- Browser cookies being blocked or cleared too frequently.
- Aggressive timeout settings from your organization.
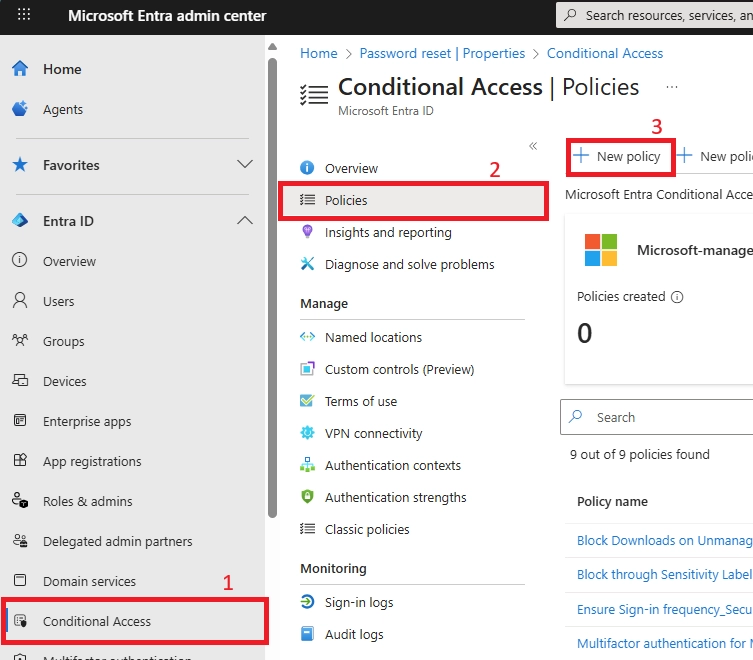
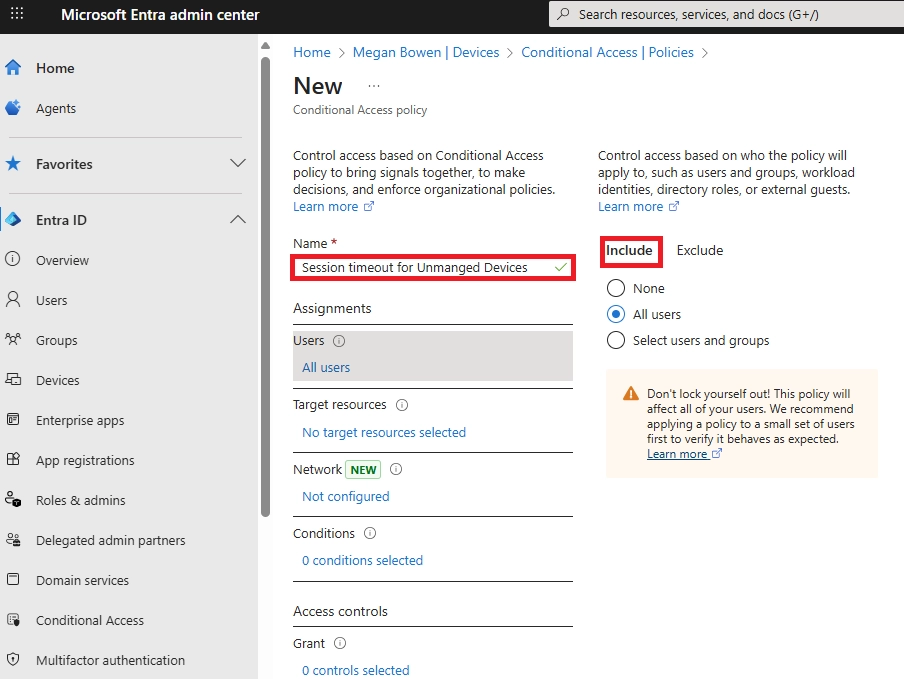
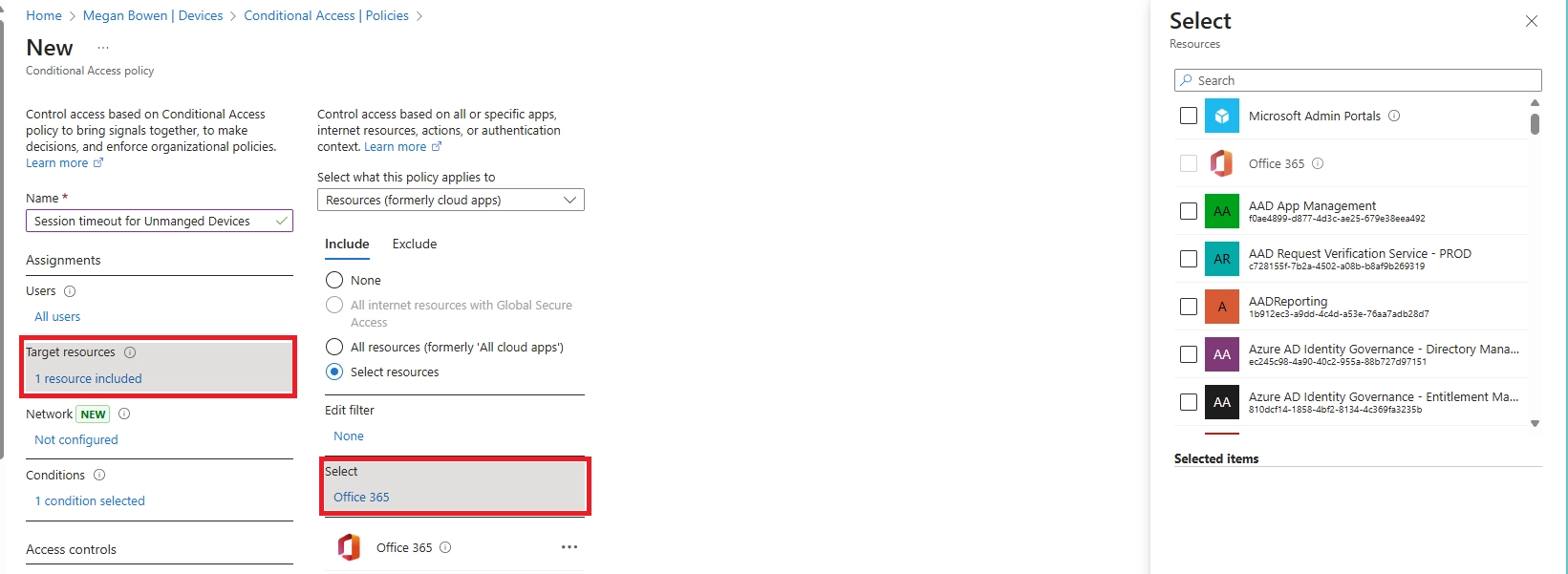
- Conditional Access policies targeting unmanaged devices.
Q6. How can I prevent being signed out of Microsoft 365 web apps while I’m actively using them?
Stay active within the session by interacting with the app. Microsoft 365 typically warns you before signing you out, giving you a chance to extend your session.
Q7. Will closing my browser or restarting my device sign me out of Microsoft 365?
It depends on your browser and your organization's policies. Some policies enforce sign-out when the browser is closed; others allow sessions to persist until the timeout period ends.
Q8. How does selecting “Stay signed in” affect my Microsoft 365 session duration?
Choosing “Stay signed in” helps maintain your session across browser restarts but doesn’t override idle timeout policies set by your organization.
Q9. Does the Microsoft 365 idle timeout apply to desktop or mobile apps, or only to web browsers?
These policies apply only to web browsers. Desktop and mobile apps like Outlook, Teams, or OneDrive are managed differently through token lifetimes, not browser session policies.
Q10. Why do organizations enforce automatic idle sign-out in Microsoft 365?
To protect sensitive information from being exposed on shared or unmanaged devices. It minimizes risk if a user forgets to sign out and leaves their device unattended.
Q11. On a public or shared computer, do I need to manually sign out, or will Microsoft 365 log me out?
Timeout policies help, but it’s still best practice to manually sign out on shared devices to ensure your account is secure.
Q12. What happens to unsaved work if my session times out due to inactivity?
You may lose unsaved changes. Always save your work regularly, especially in web apps where session timeouts could sign you out unexpectedly.