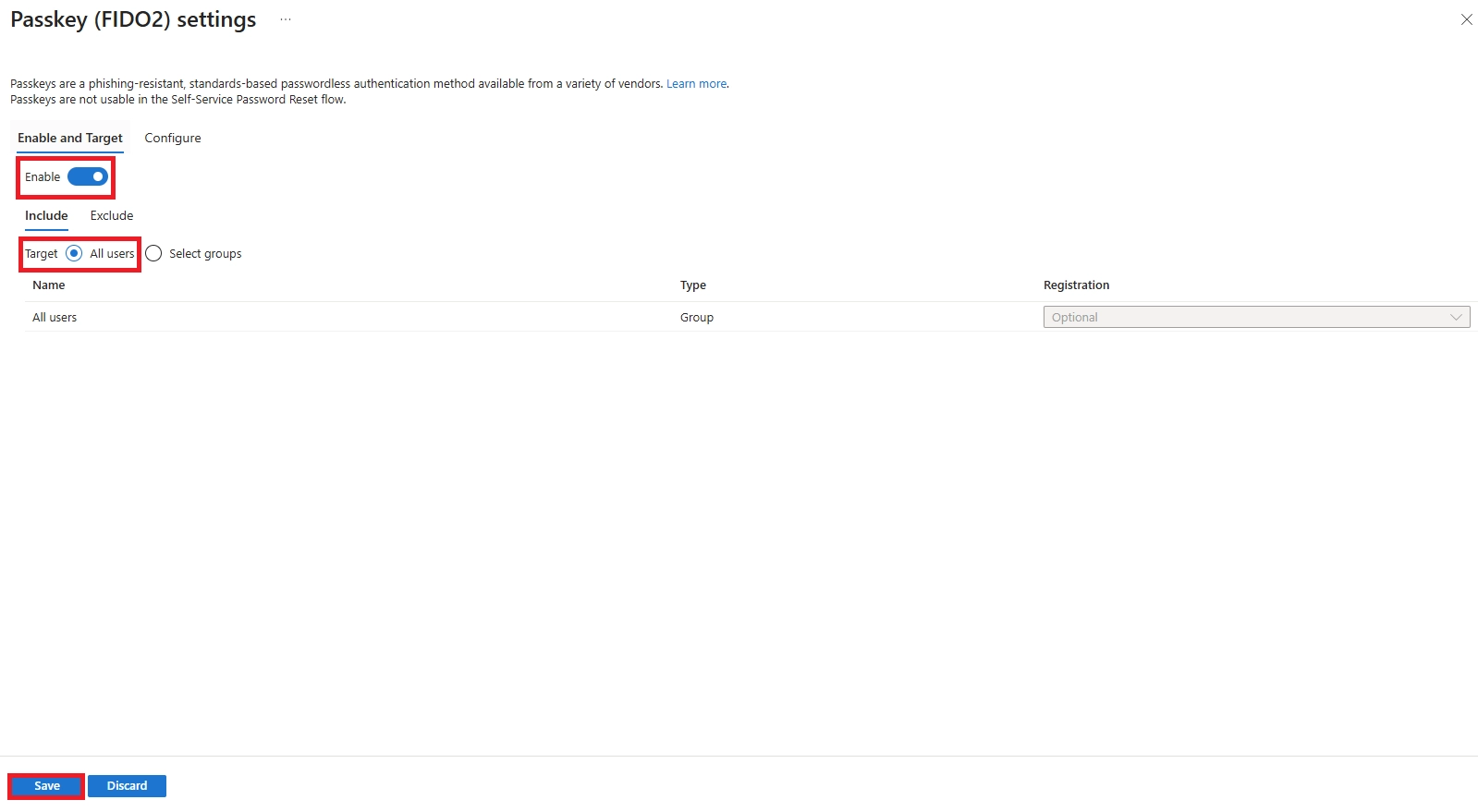
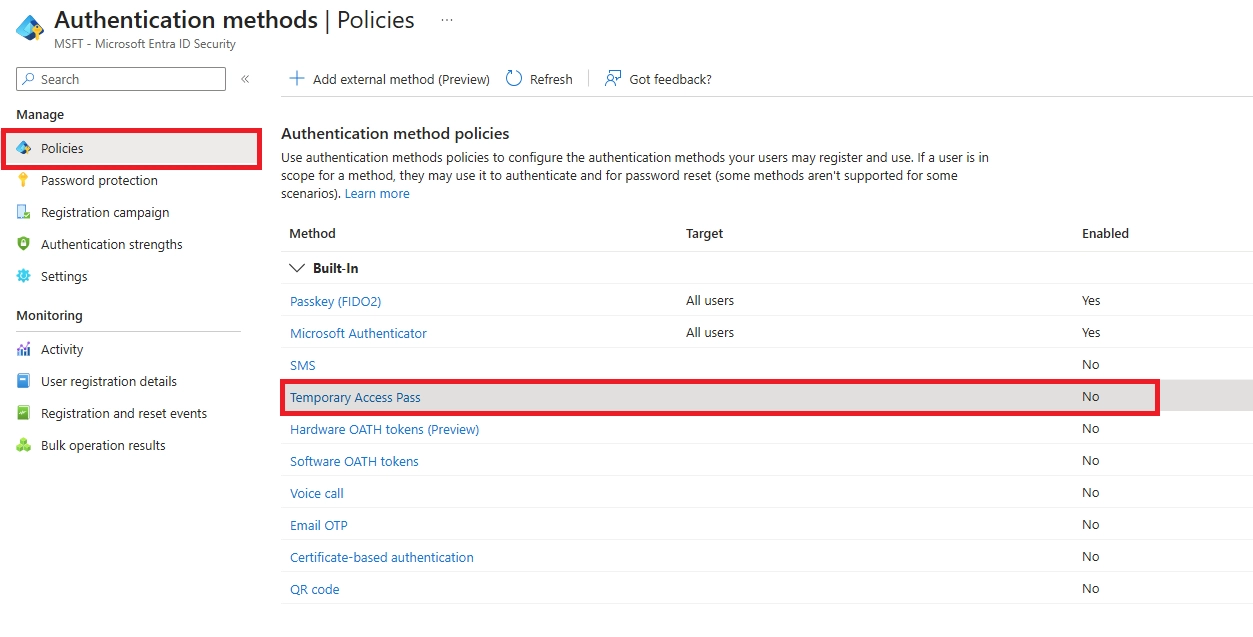
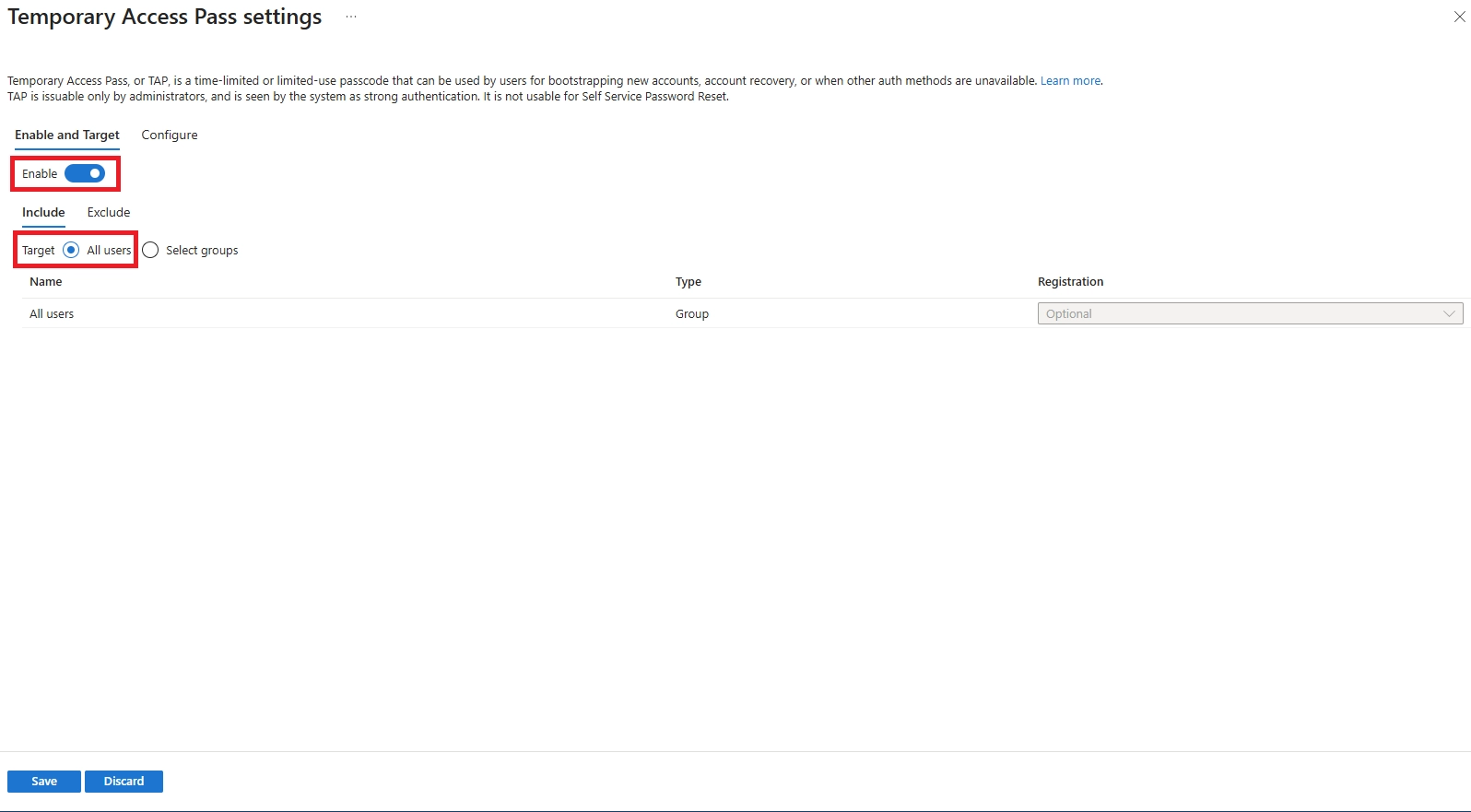
Q: What if a user loses their phone or security key?
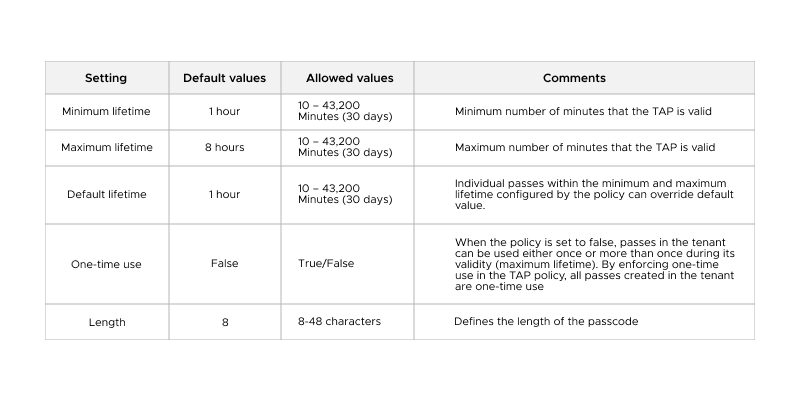
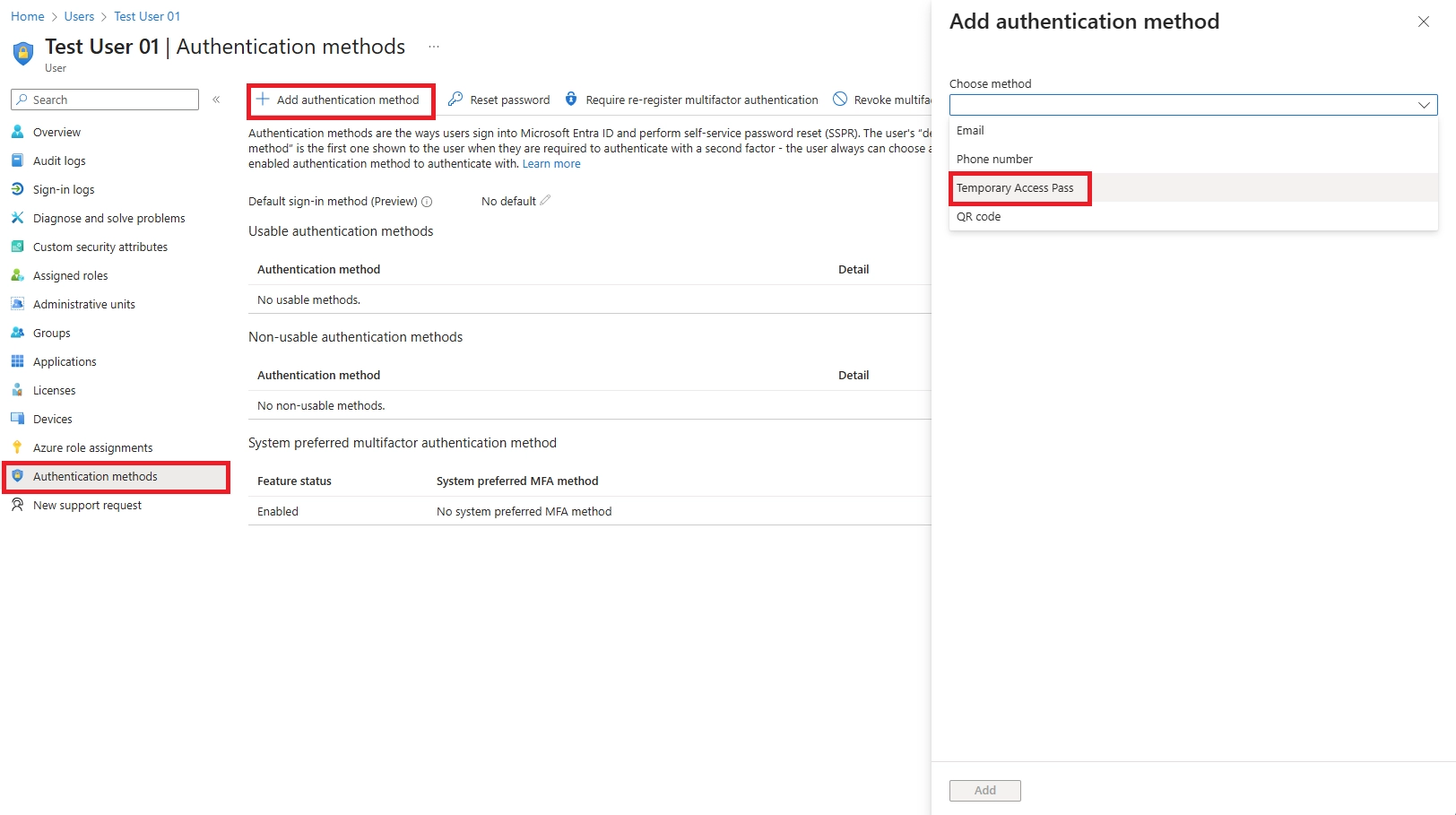
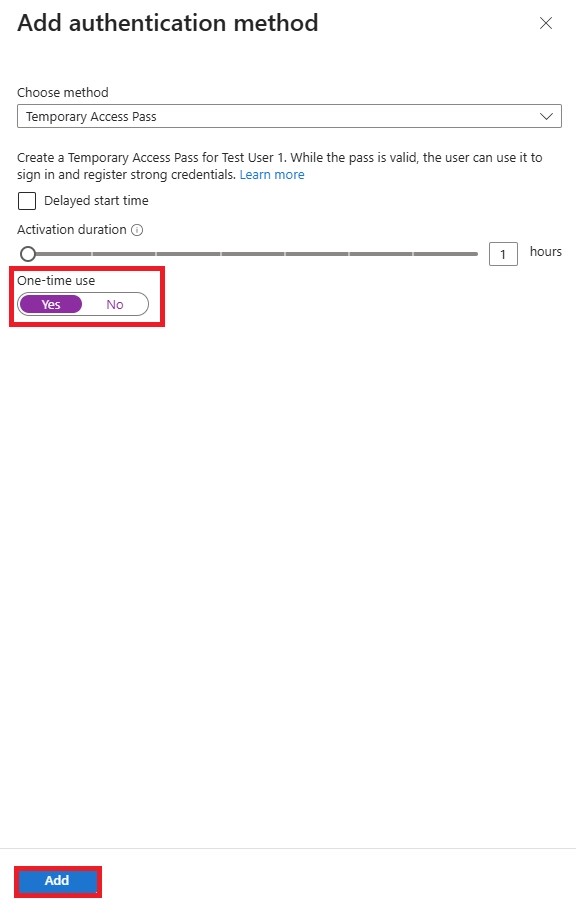
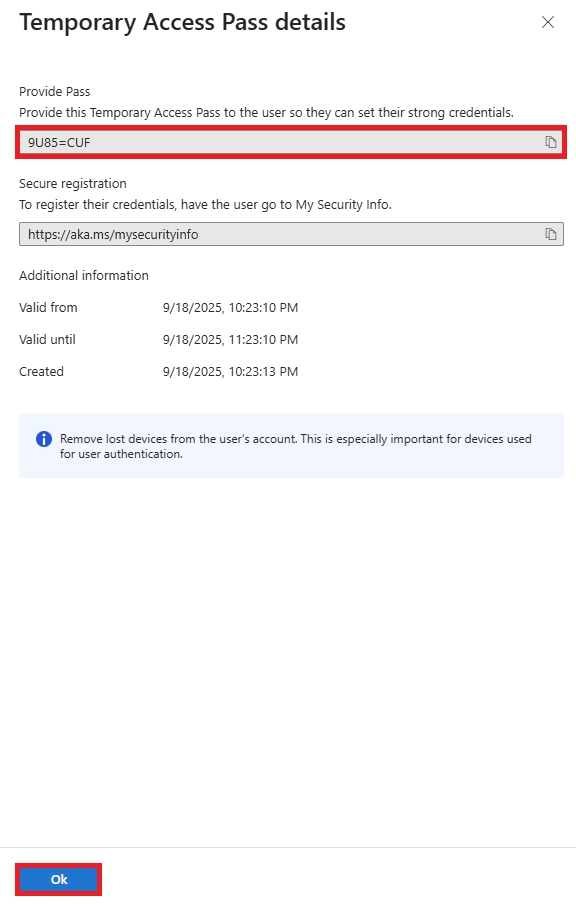
Use their backup method (FIDO2 key, Windows Hello, or second device). Admin can issue Temporary Access Pass for re-registration. Immediately revoke lost keys in Azure AD.
Q: Can we truly remove passwords entirely?
Yes for daily use. Policies can block password logins completely. Password fields still exist in Azure AD but become unused random values.
Q: How does this affect older applications?
Legacy apps get blocked when you disable basic authentication. Update apps, use break-glass accounts, or implement certificate-based auth for necessary legacy systems.
Q: Do passwordless methods work offline?
Windows Hello works offline for device login. FIDO2 keys work locally. But cloud apps always need internet, same as with passwords.
Q: How secure is my biometric data in Windows Hello?
Fingerprints never leave your device. Data stays encrypted in the TPM chip locally. Microsoft only receives cryptographic proof.
Q: What is passwordless sign-in on Microsoft?
Logging into Microsoft 365 without typing passwords. Use fingerprints, phone approval, or security keys instead.
Q: What's the difference between passwordless and MFA?
Passwordless replaces passwords entirely. Traditional MFA adds a second factor to passwords. Passwordless methods are inherently multi-factor.
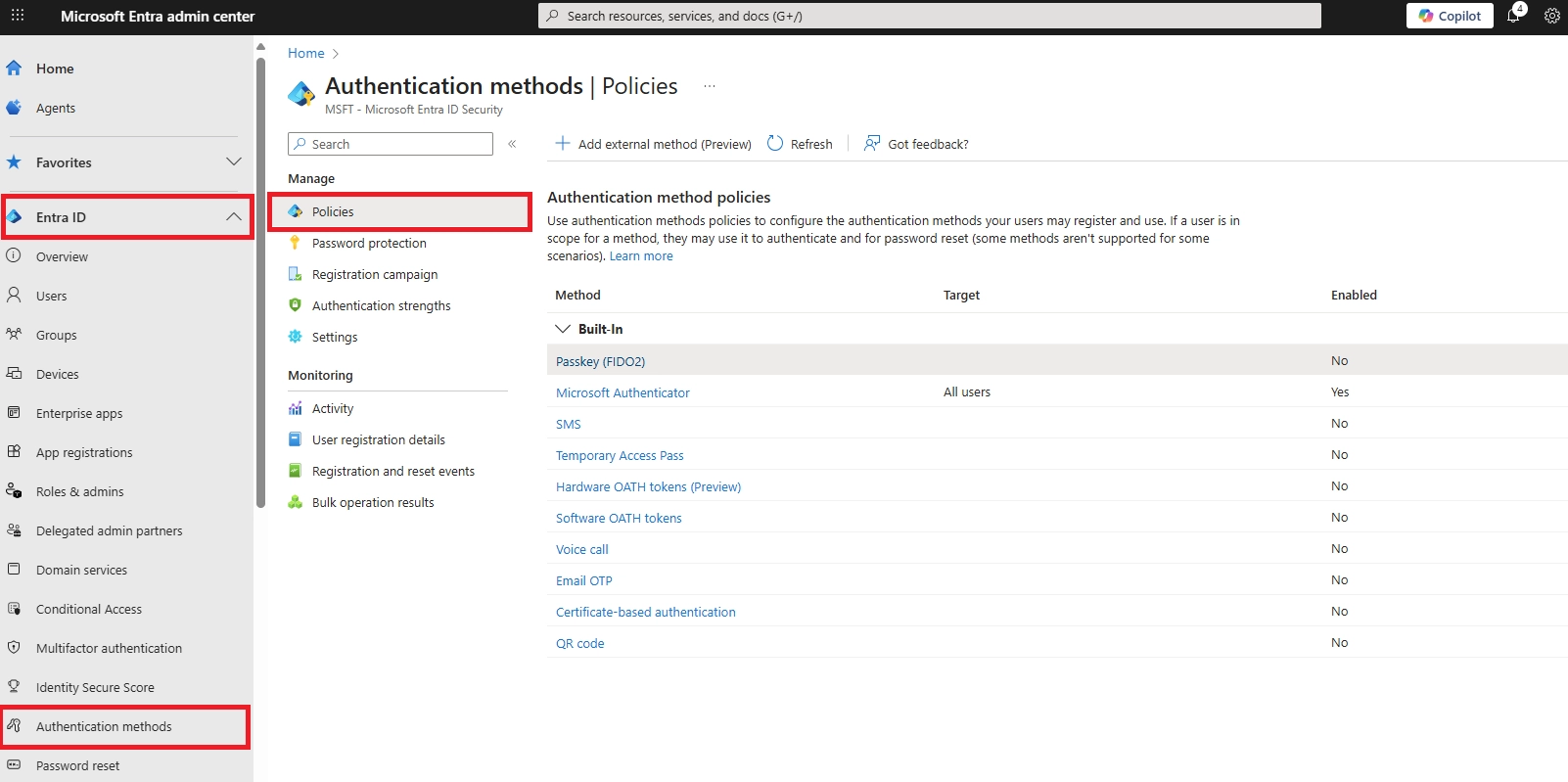
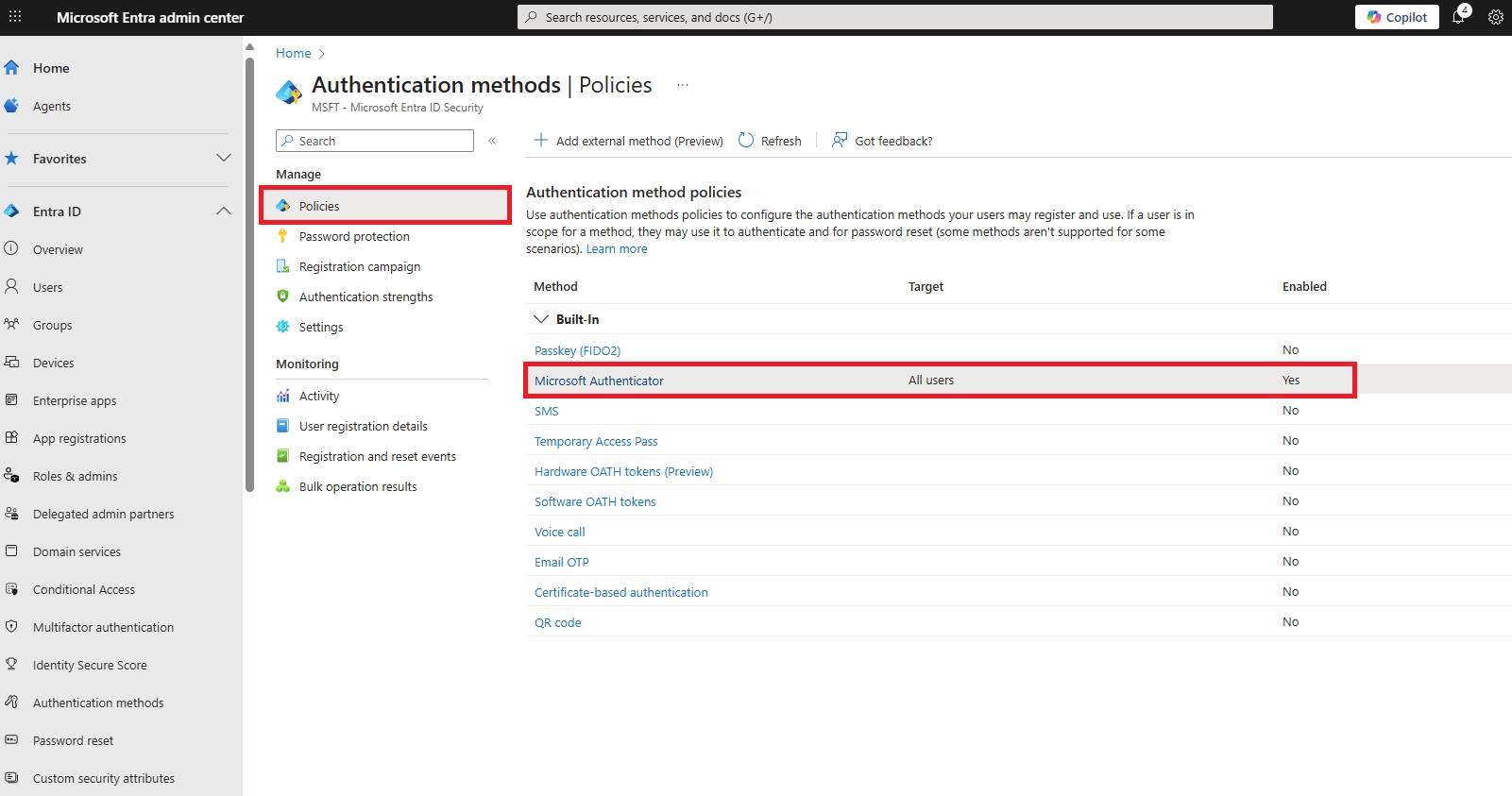
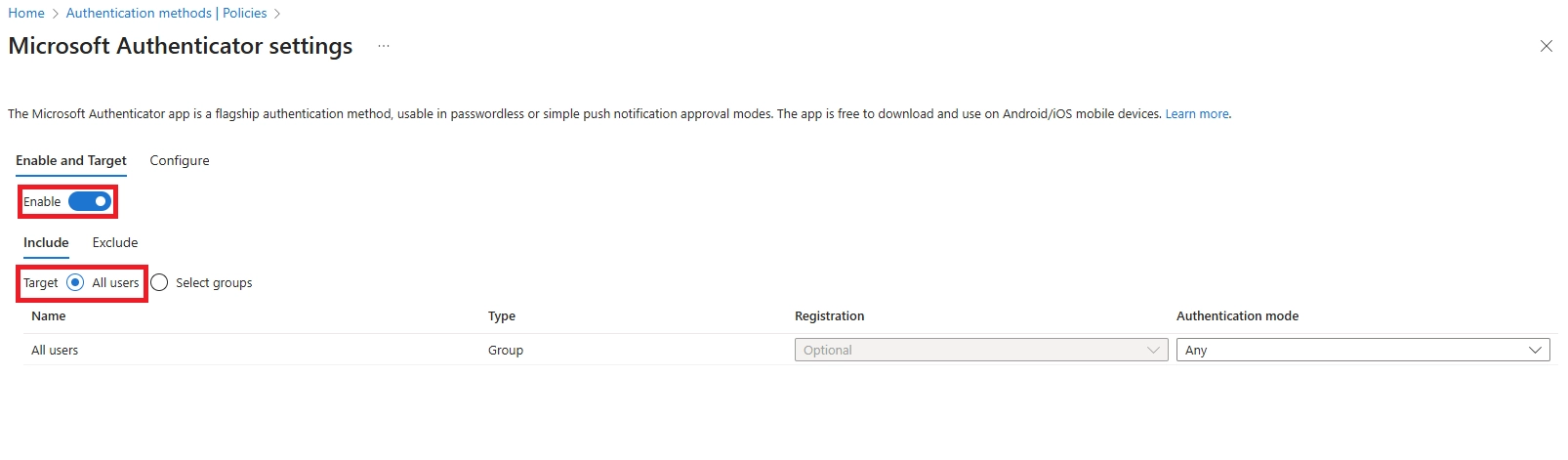
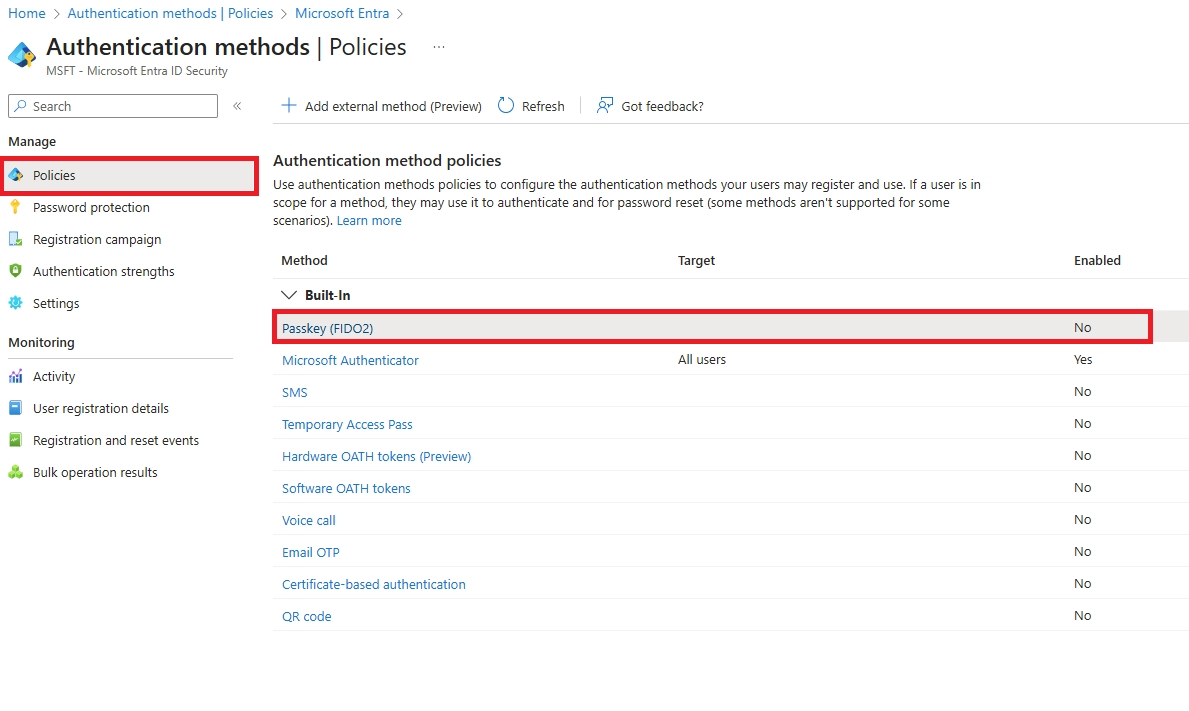
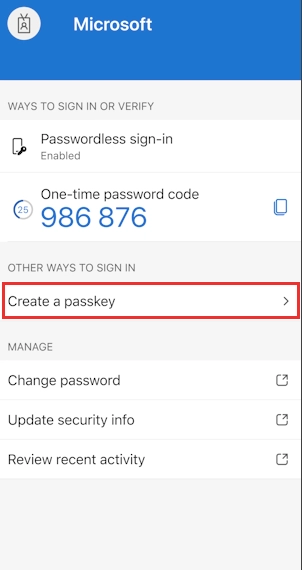
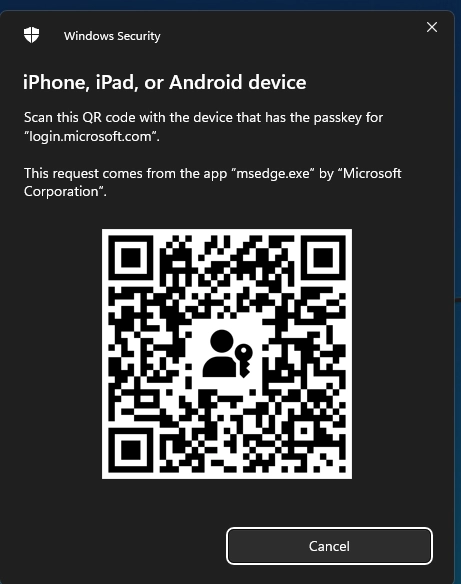
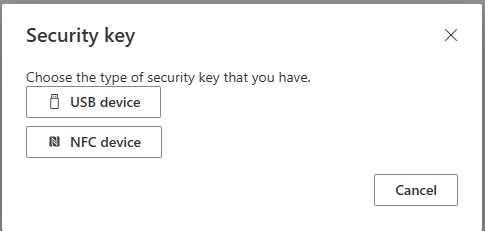
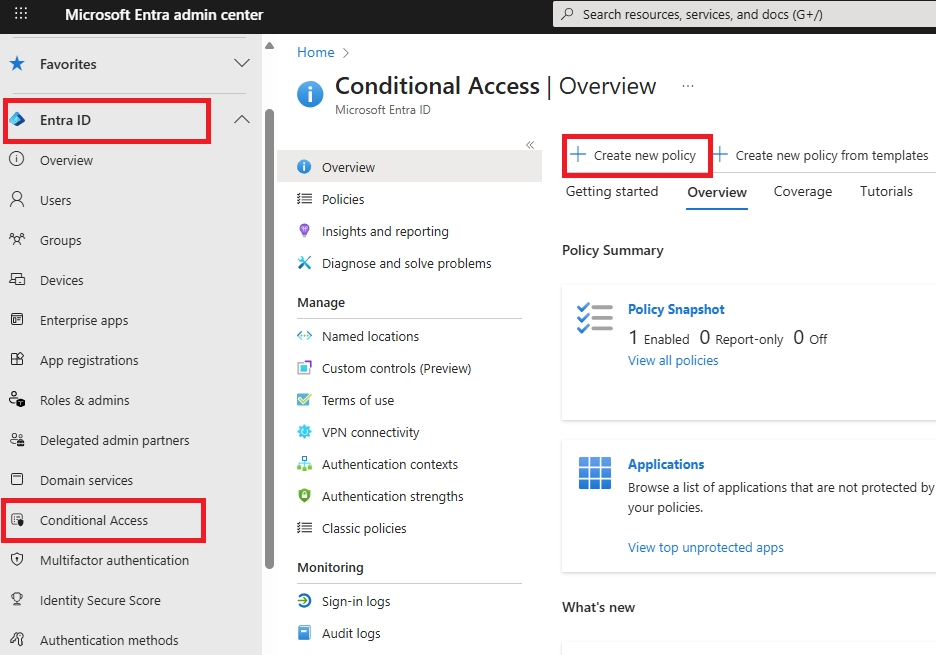
Q: How to do passwordless sign-in?
Register methods at aka.ms/setupsecurityinfo. Set up Authenticator phone sign-in, FIDO2 keys, or Windows Hello. Follow our implementation guide above.
Q: How do I turn off passwordless sign-in Windows 10?
Settings > Accounts > Sign-in options > disable Windows Hello PIN/biometrics. Or use Group Policy to disable Windows Hello for Business.
Q: Why use passwordless login?
99.2% fewer account compromises. No password resets. Faster logins. Phishing protection. Better user experience.
Q: How do I remove authentication from my Microsoft account?
You can't remove all authentication. You can disable specific methods in Security settings, but you need at least one way to sign in.
Q: Is passwordless sign-in safer?
Yes. It's phishing-resistant and eliminates password attacks. Biometrics and hardware keys can't be stolen like passwords.
Q: How to stop Microsoft asking to sign in Windows 11?
This is usually for security. You can extend sign-in timeout in Settings > Accounts > Sign-in options, but some prompts are required.
Q: How to sign in to Windows without a password?
Set up Windows Hello PIN, fingerprint, or face recognition. Or use a security key. These replace password entry.
Q: What are disadvantages of passwordless authentication?
Device dependency (lose phone/key = temporary lockout). Initial setup complexity. Some legacy apps don't support it. Requires backup methods.
Q: Which Microsoft solution provides passwordless authentication?
Microsoft Entra ID (formerly Azure AD) with Windows Hello, Authenticator app, and FIDO2 security keys.
Q: Which technology is commonly used in passwordless?
FIDO2/WebAuthn standards, biometrics (fingerprint/face), hardware security keys, and platform authenticators like TPM chips.
Q: What does FIDO2 stand for?
Fast Identity Online version 2. It's the standard for phishing-resistant authentication using hardware keys.
Q: Which three methods support passwordless authentication?
Windows Hello for Business, Microsoft Authenticator phone sign-in, and FIDO2 security keys.
Q: Is passwordless considered MFA?
Yes. These methods combine something you have (device/key) with something you are (biometric) or know (PIN). It's inherently multi-factor.