Q1. Why can’t I see Microsoft 365 Attack Simulation Training in my portal?
You need Microsoft Defender for Office 365 Plan 2. Also ensure you have the Attack Simulation Administrator or Security Administrator role.
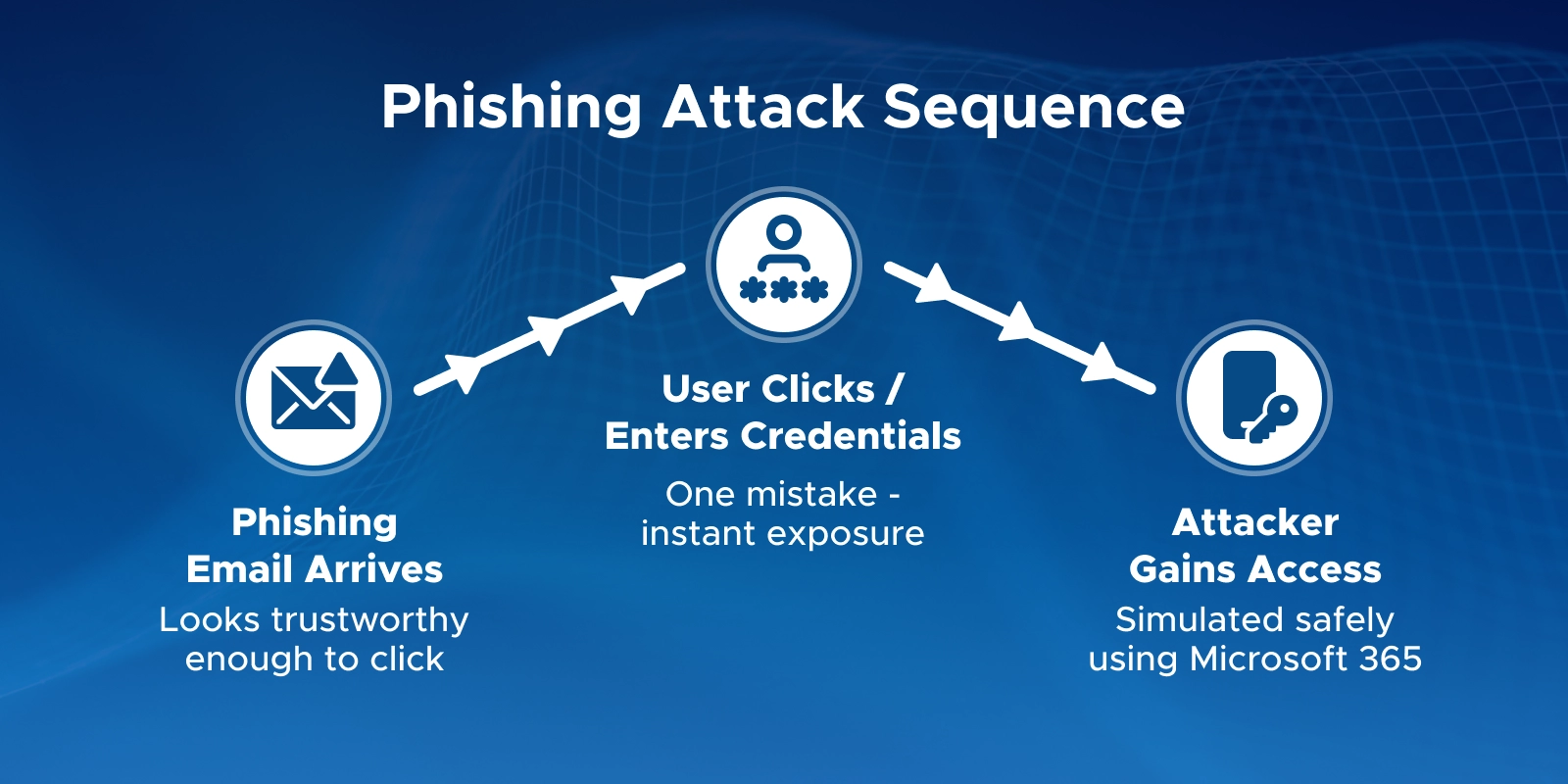
Q2. Why are users not receiving my Microsoft 365 phishing simulation emails?
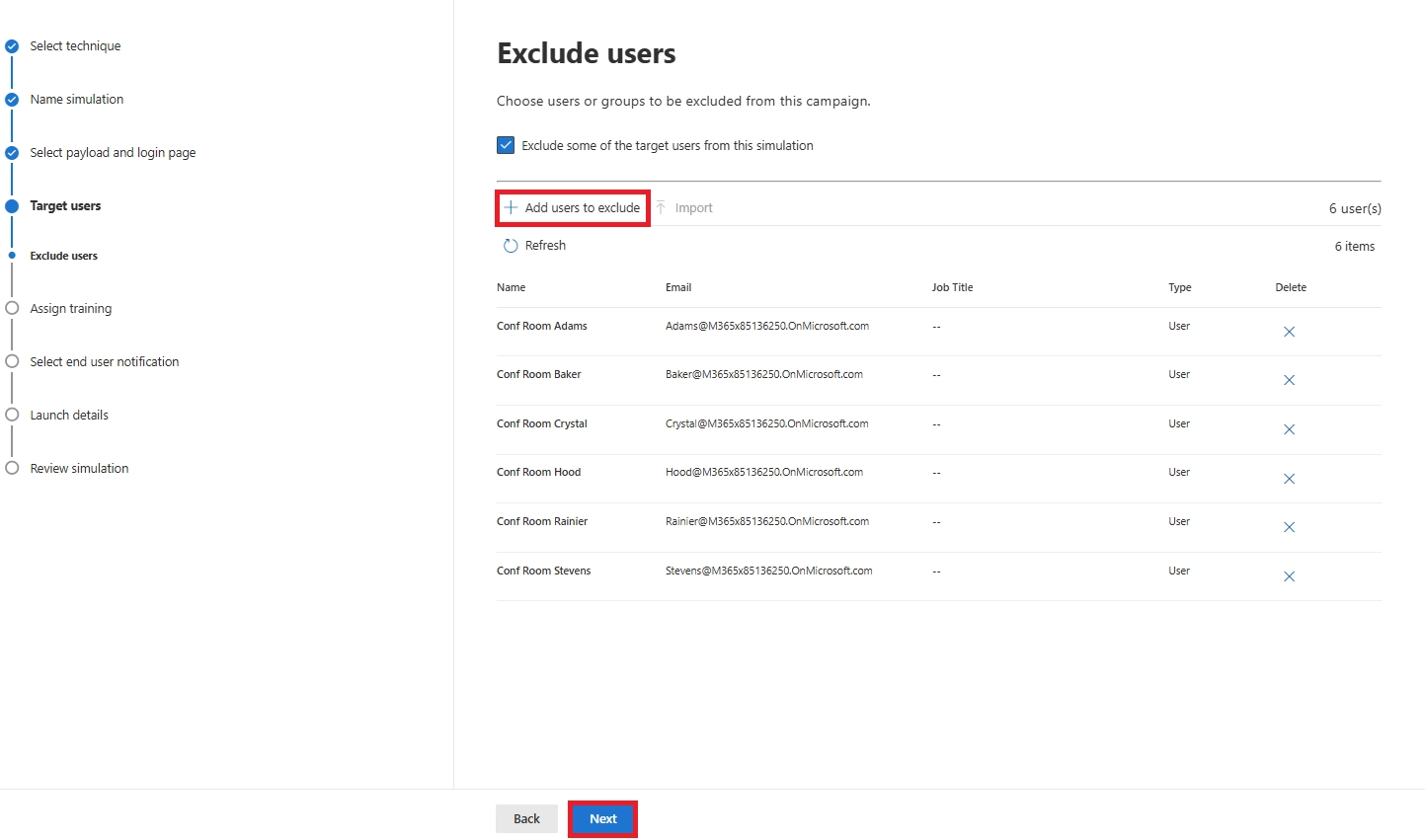
Check delivery status. Filters may block attack simulation domains, or targets may lack Plan 2 licenses. Guest or non-mailbox users are automatically excluded.
Q3. Why did the phishing simulation email go to Junk or appear as External?
Exchange Online flagged it. Add approved attack simulation domains to the allow list or use a Tenant notification internal sender.
Q4. Why do users see browser warnings when clicking the phishing link?
Browsers like Chrome may block simulation URLs. The click still appears in the Microsoft 365 attack simulation report, but the landing page may not load.
Q5. Why does the report show a user was targeted but they never saw the email?
Check Junk, Focused Inbox, and the campaign’s delivery log. This can occur in large Microsoft 365 simulated attack campaigns.
Q6. Why do reports show instant clicks that users deny?
Automated scanners or secure gateways often click URLs before users do. The IP in logs will reveal this.
Q7. Why didn’t some users get training after failing a phishing simulation?
If you selected No Training or the user completed that module recently, training may not trigger. Check Training Campaigns status.
Q8. Do replies or forwards count as failing the Microsoft 365 attack simulation?
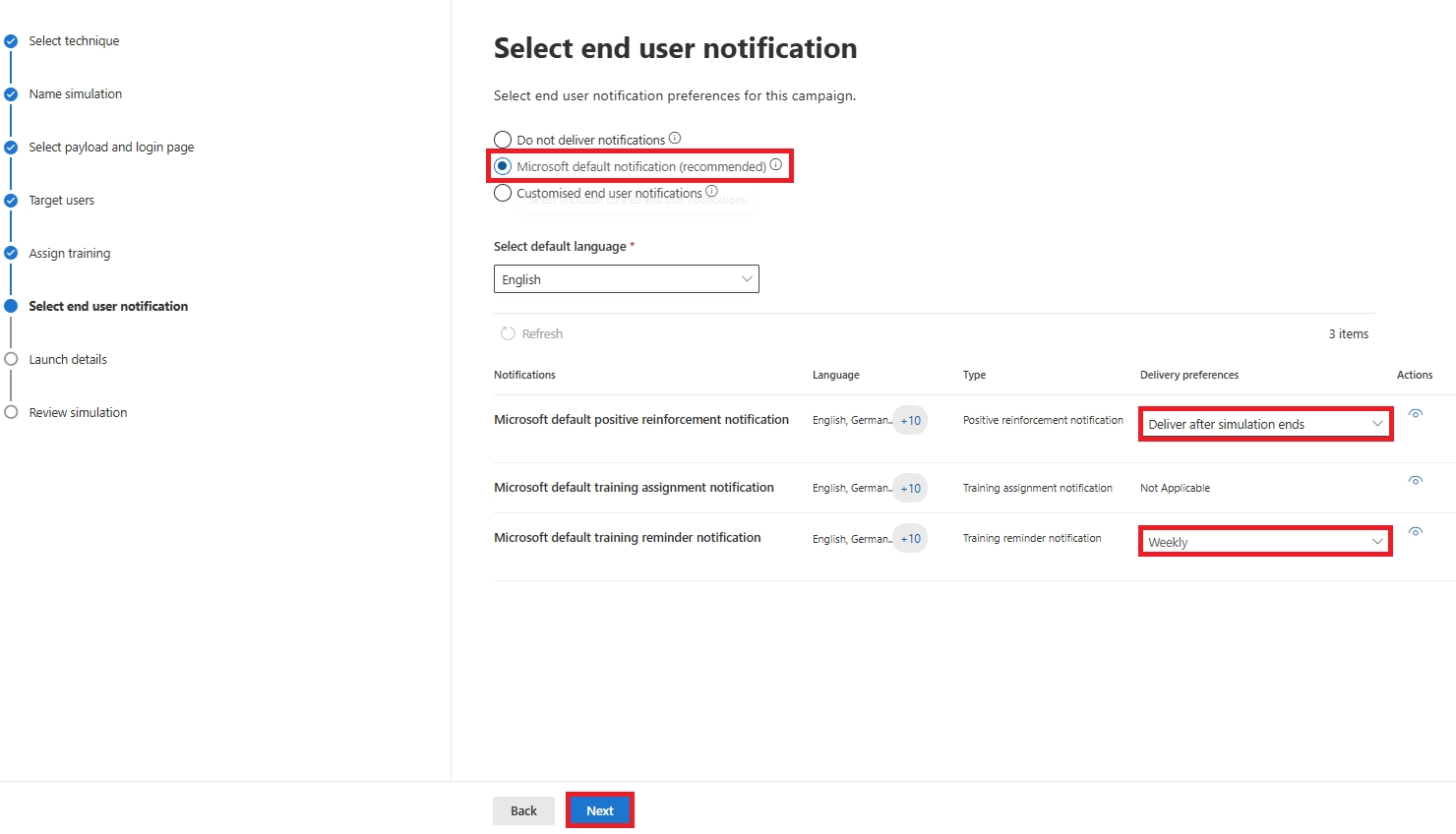
No. Only clicks, credential submissions, or opening malicious attachments count in Microsoft 365 phishing simulation setup.
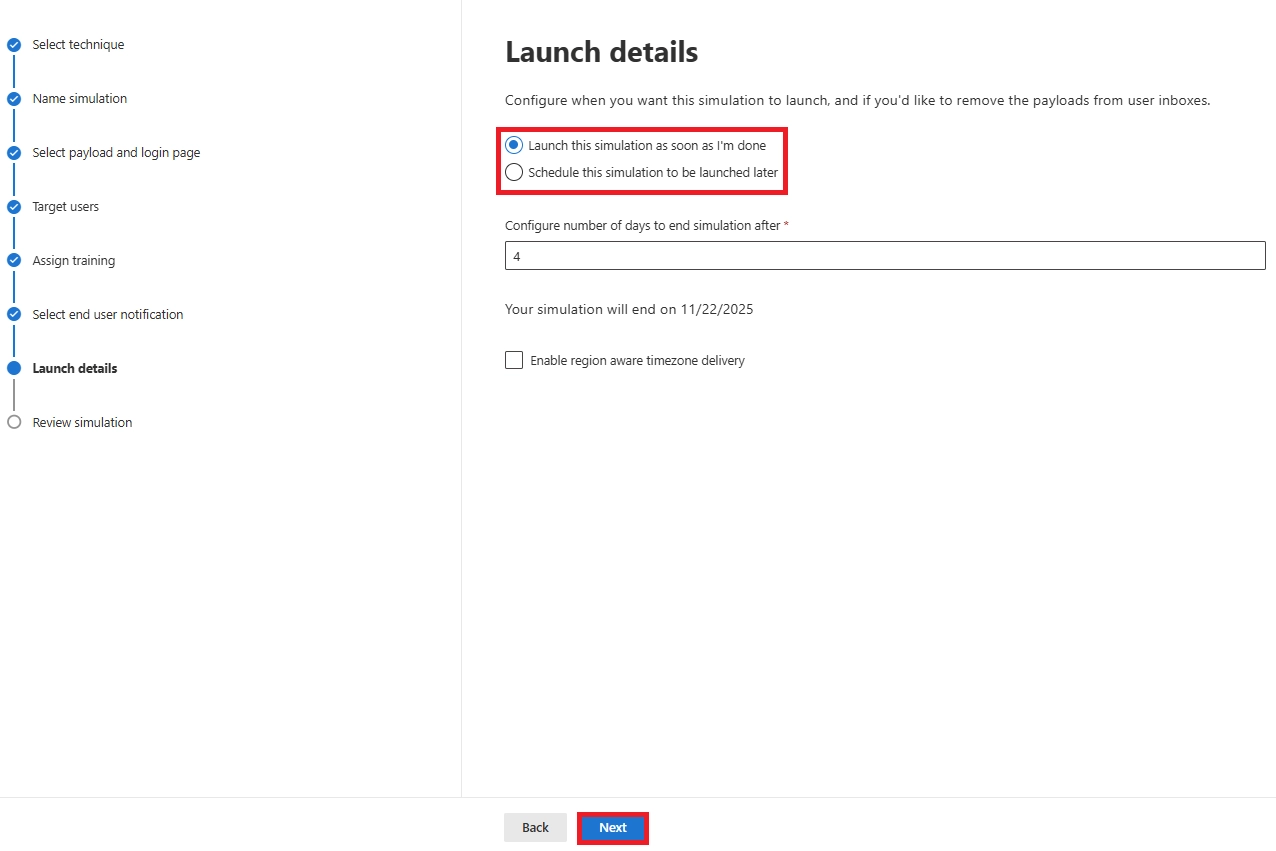
Q9. How often should we run Microsoft 365 phishing simulations?
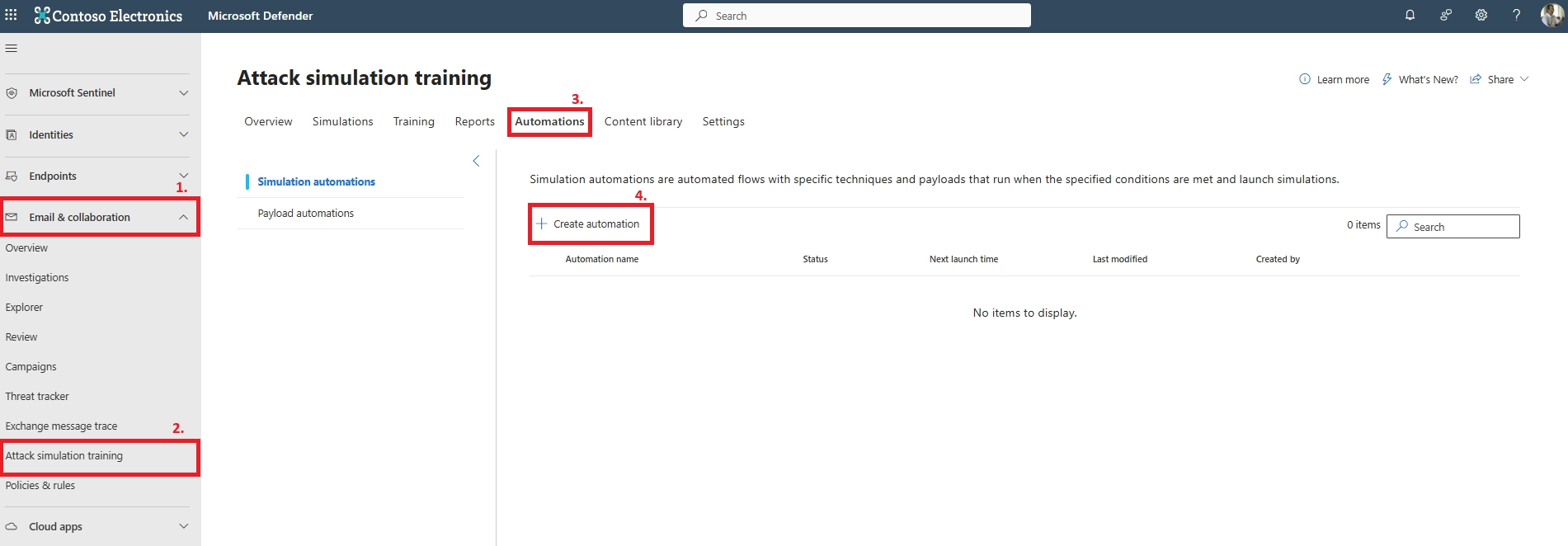
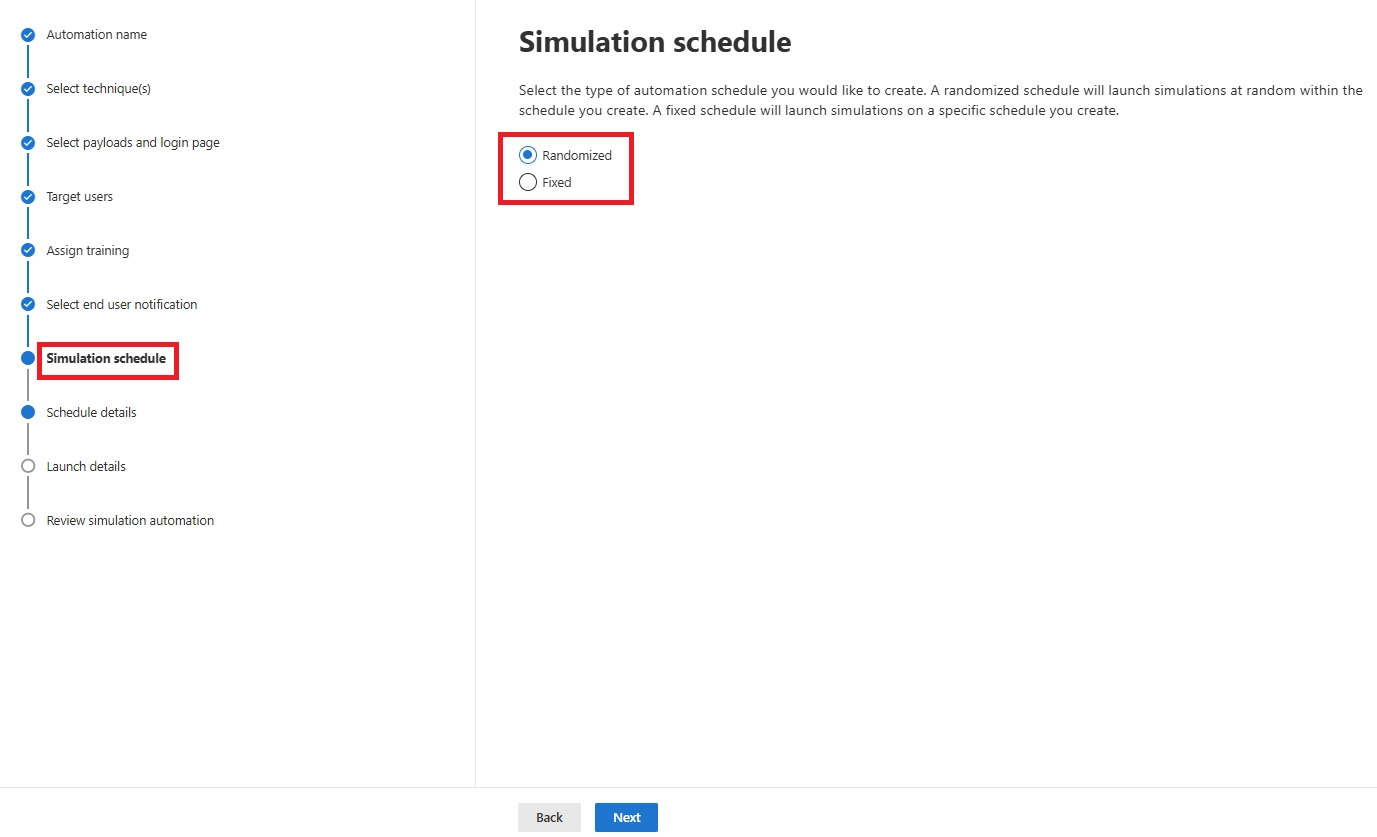
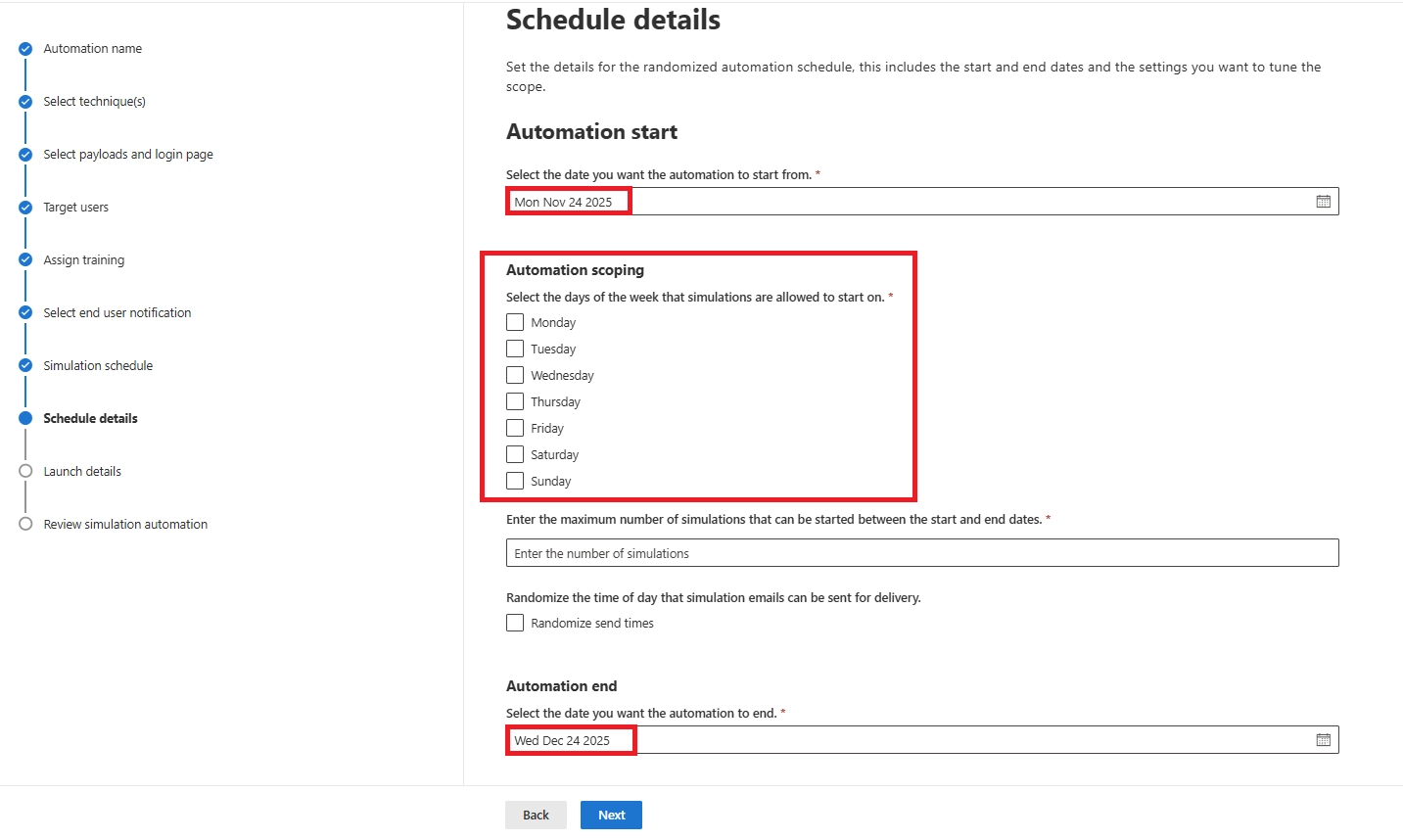
Minimum: twice a year. Recommended: quarterly. For strong programs, use Simulation Automations to run monthly.
Q10. How do we handle repeat offenders in Microsoft 365 Attack Simulation Training?
Use the repeat offender threshold, assign deeper training, or provide one-on-one coaching.
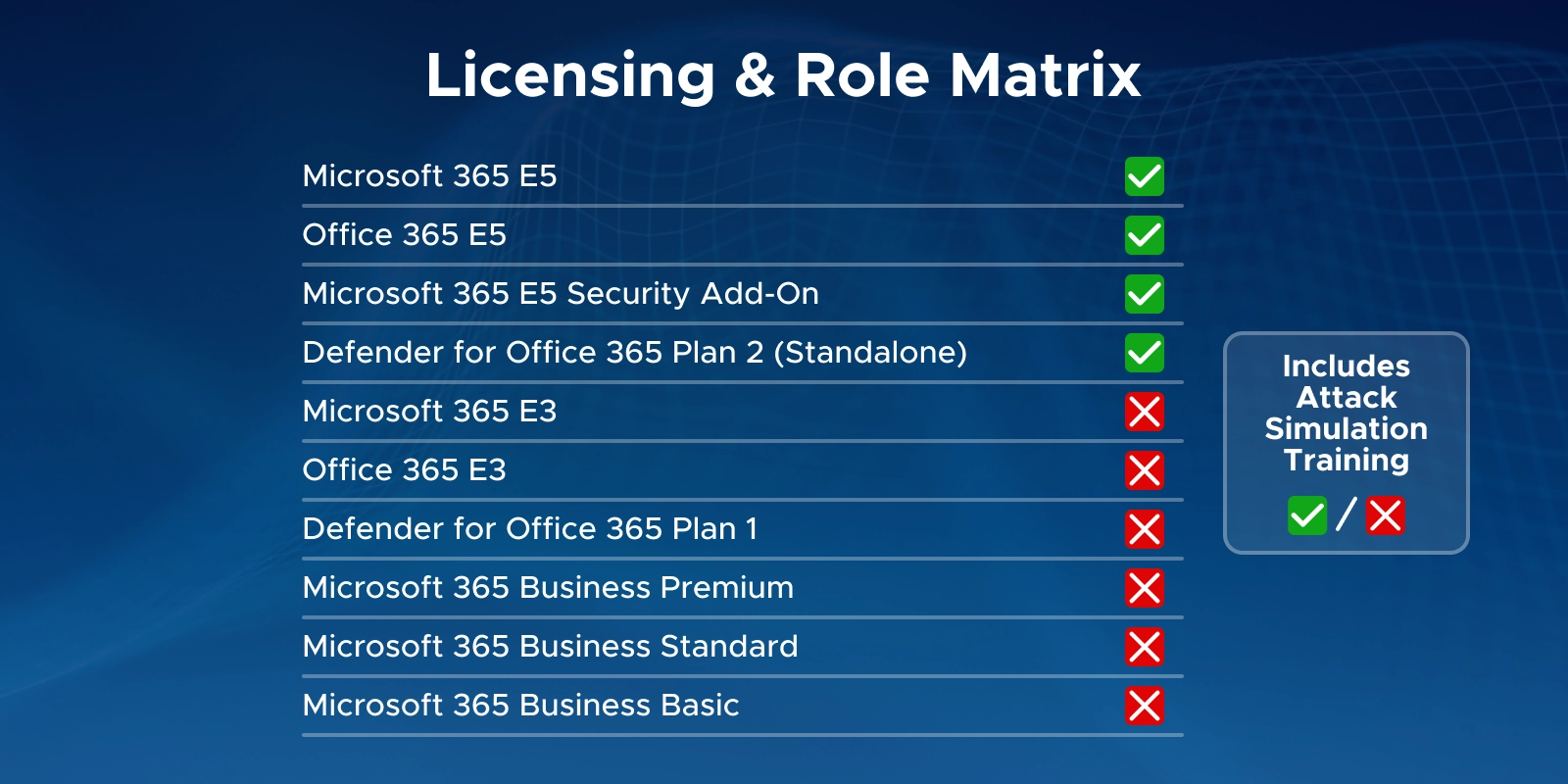
Q11. Which license is needed for Microsoft 365 Attack Simulation Training?
Defender for Office 365 Plan 2 or any E5 SKU. E3 users can add Plan 2 or activate a 90-day trial.
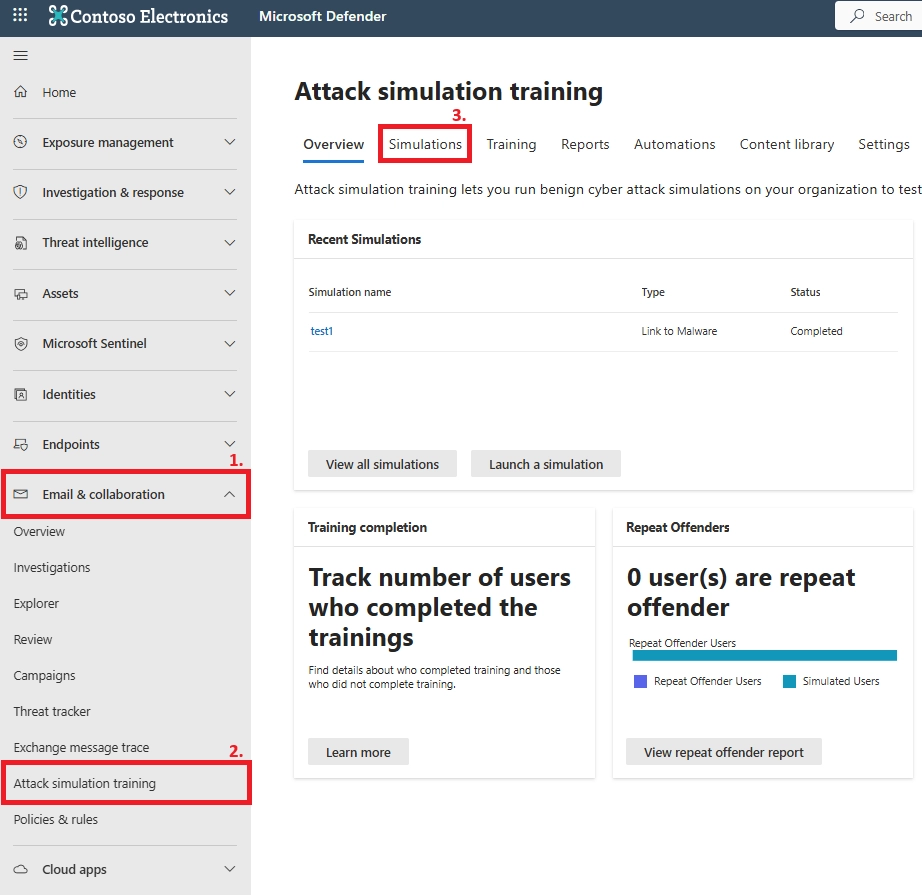
Q12. What is Microsoft Attack Simulation Training?
A built-in Microsoft 365 security simulation tool for phishing, malware, and social engineering testing, paired with awareness training.
Q13. Is notification@attacksimulationtraining.com a legit Microsoft sender?
Yes. It is used for official Microsoft 365 attack simulation email notifications.
Q14. Which Microsoft 365 workloads support phishing simulation?
Exchange Online, Defender for Office 365, Entra ID groups, and Microsoft security training modules.
Q15. Does Microsoft offer phishing training?
Yes - through Microsoft Defender Attack Simulation Training with built-in phishing awareness courses.
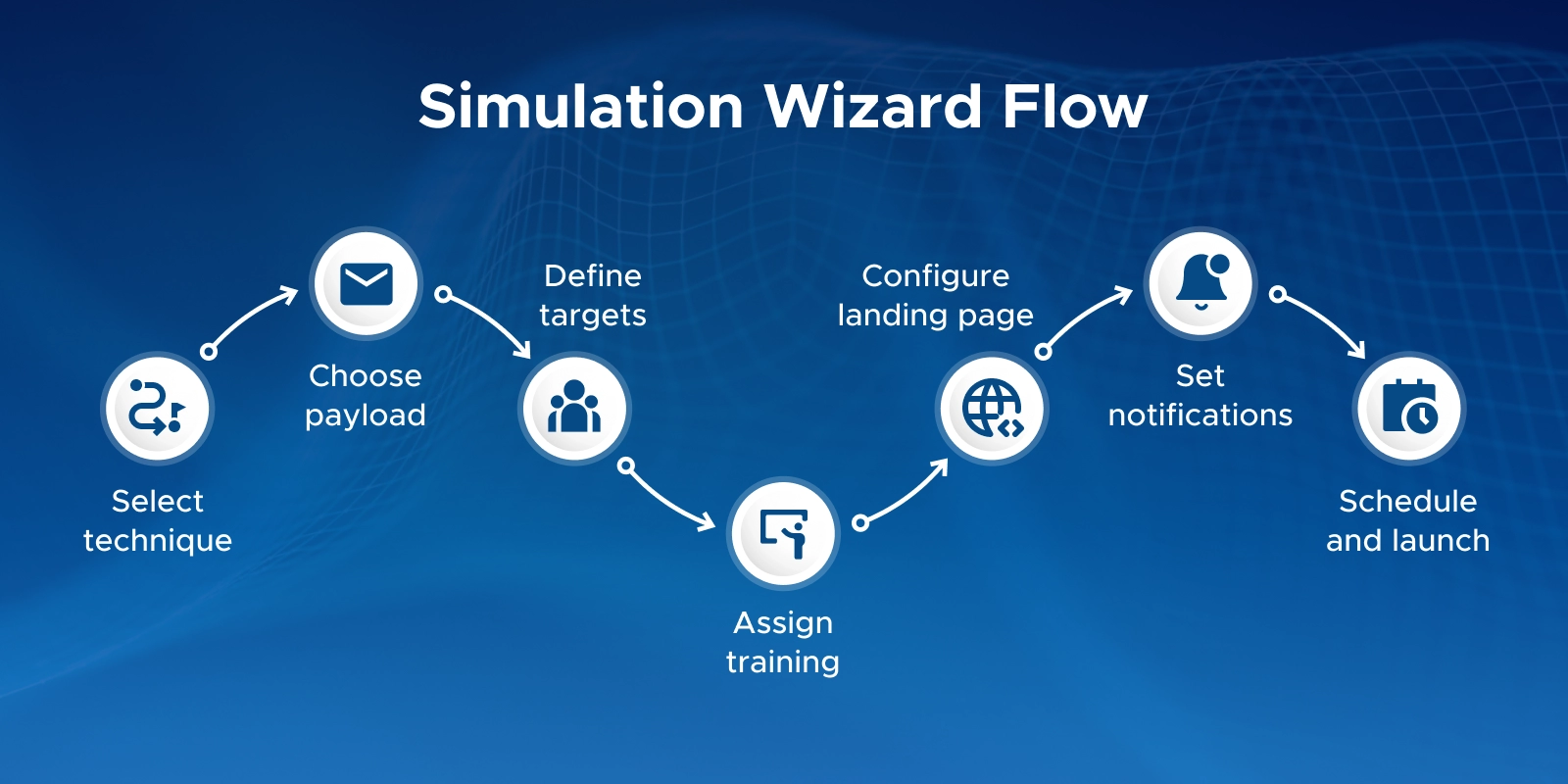
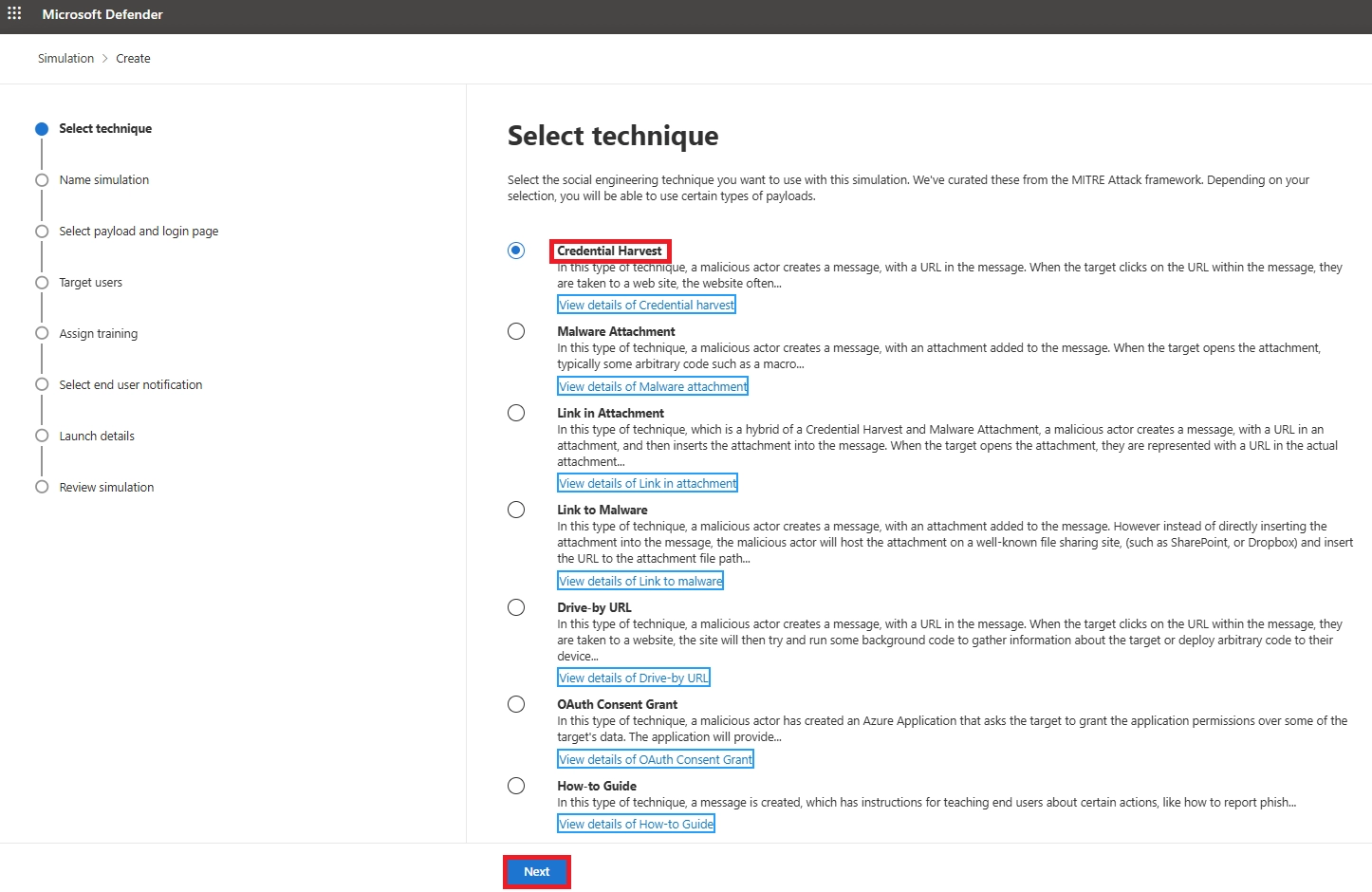
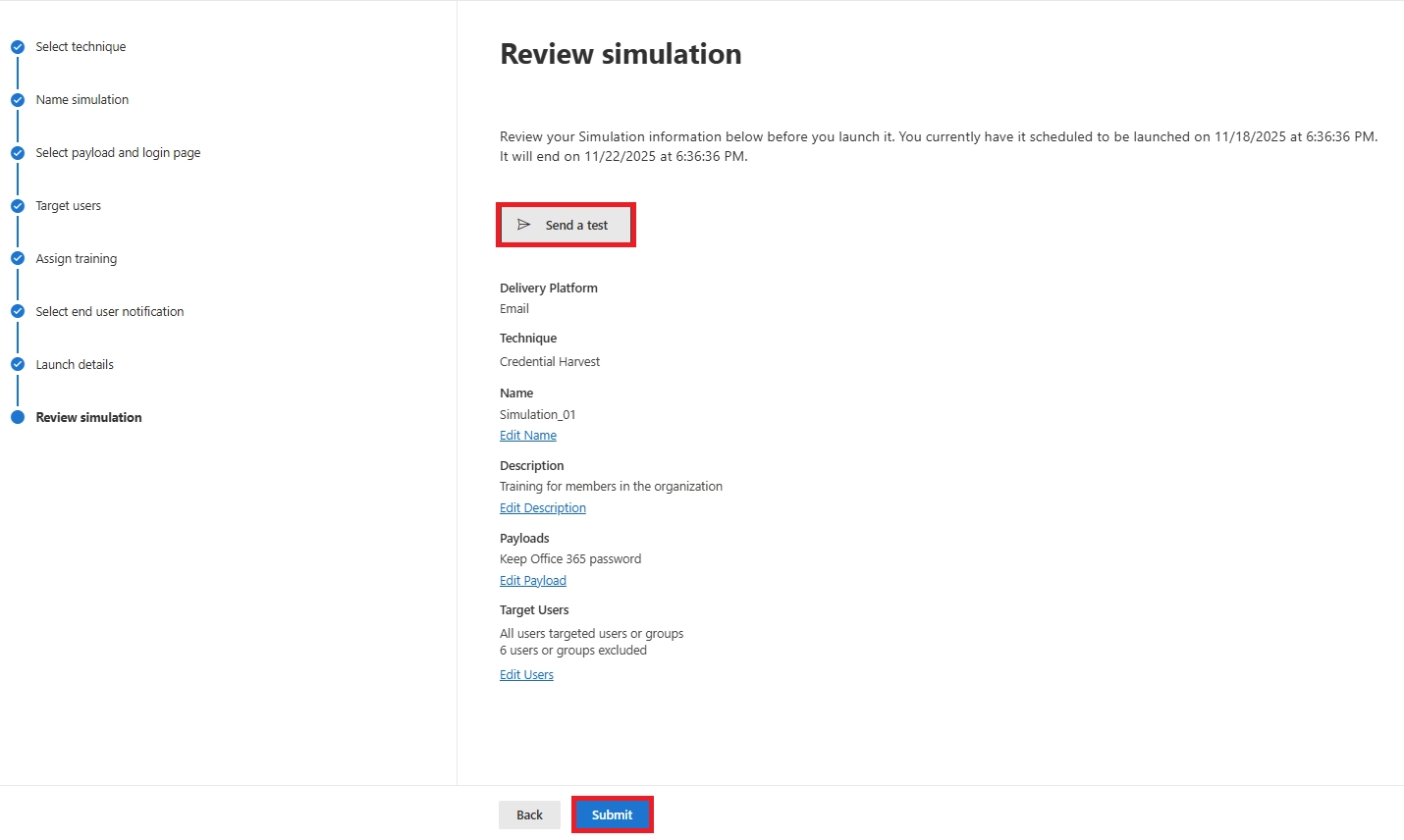
Q16. What attack types can I use in Microsoft 365 Attack Simulation?
Credential Harvest, Malware Attachment, Link in Attachment, Drive-by URL, OAuth Consent Grant, and training-only “How-to Guide” scenarios.
Q17. What is the best phishing simulation type for beginners?
Credential Harvest - a classic, high-impact phishing test used in most Microsoft 365 attack simulation setup guides.
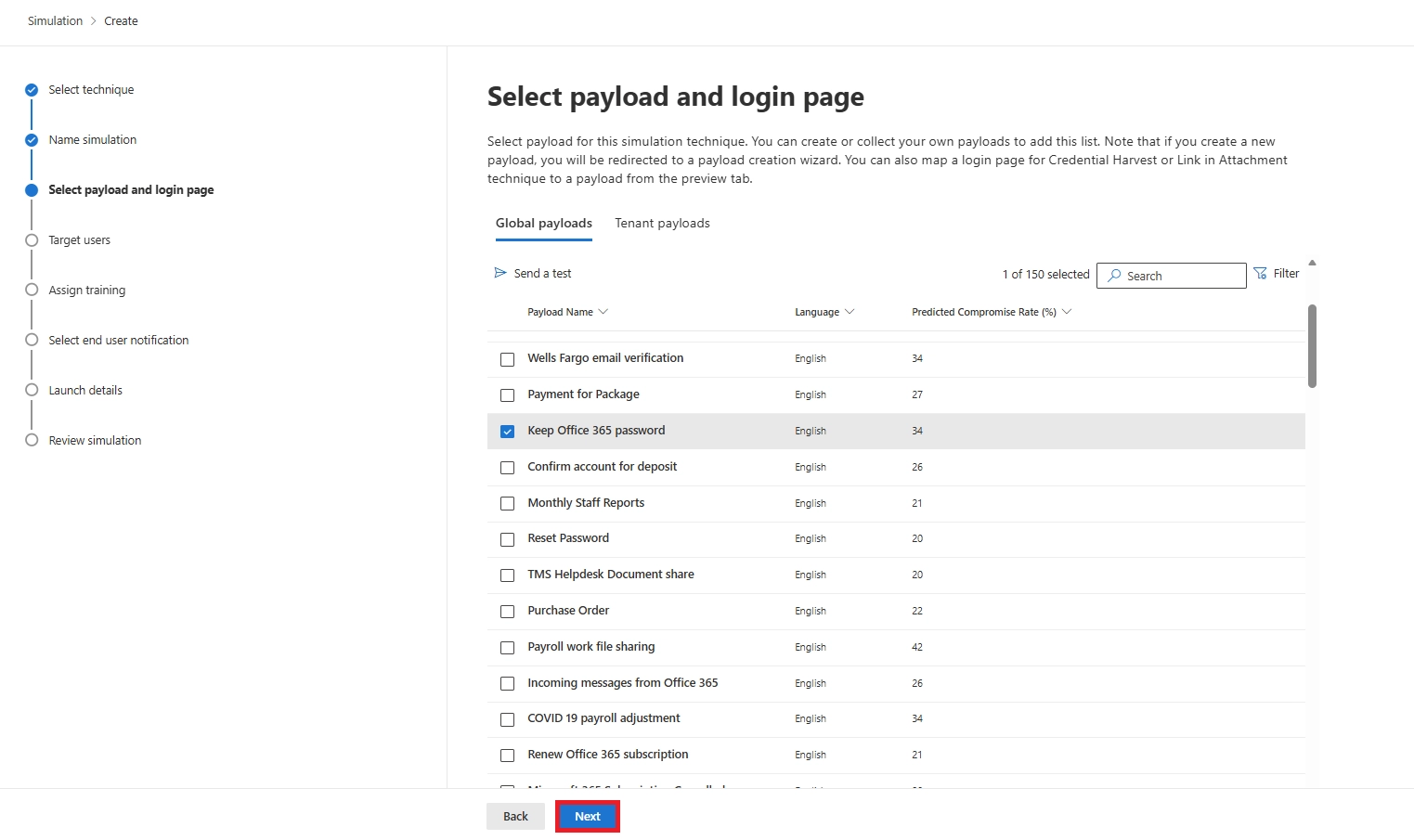
Q18. Can I customize the phishing payload in Microsoft 365 Attack Simulation?
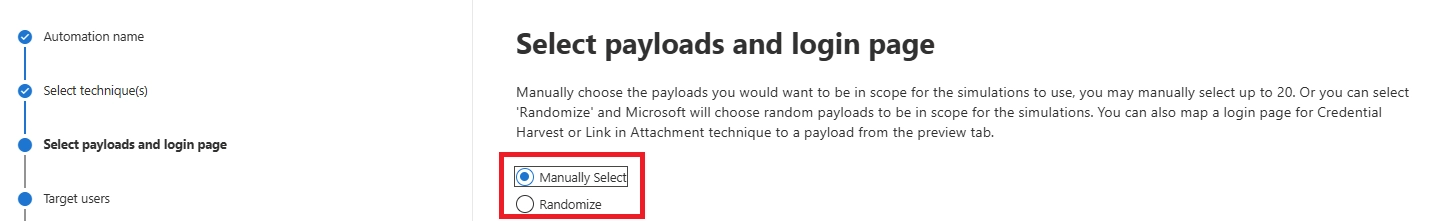
Yes. You can create custom payloads and login pages to match internal workflows, brands, or departments.
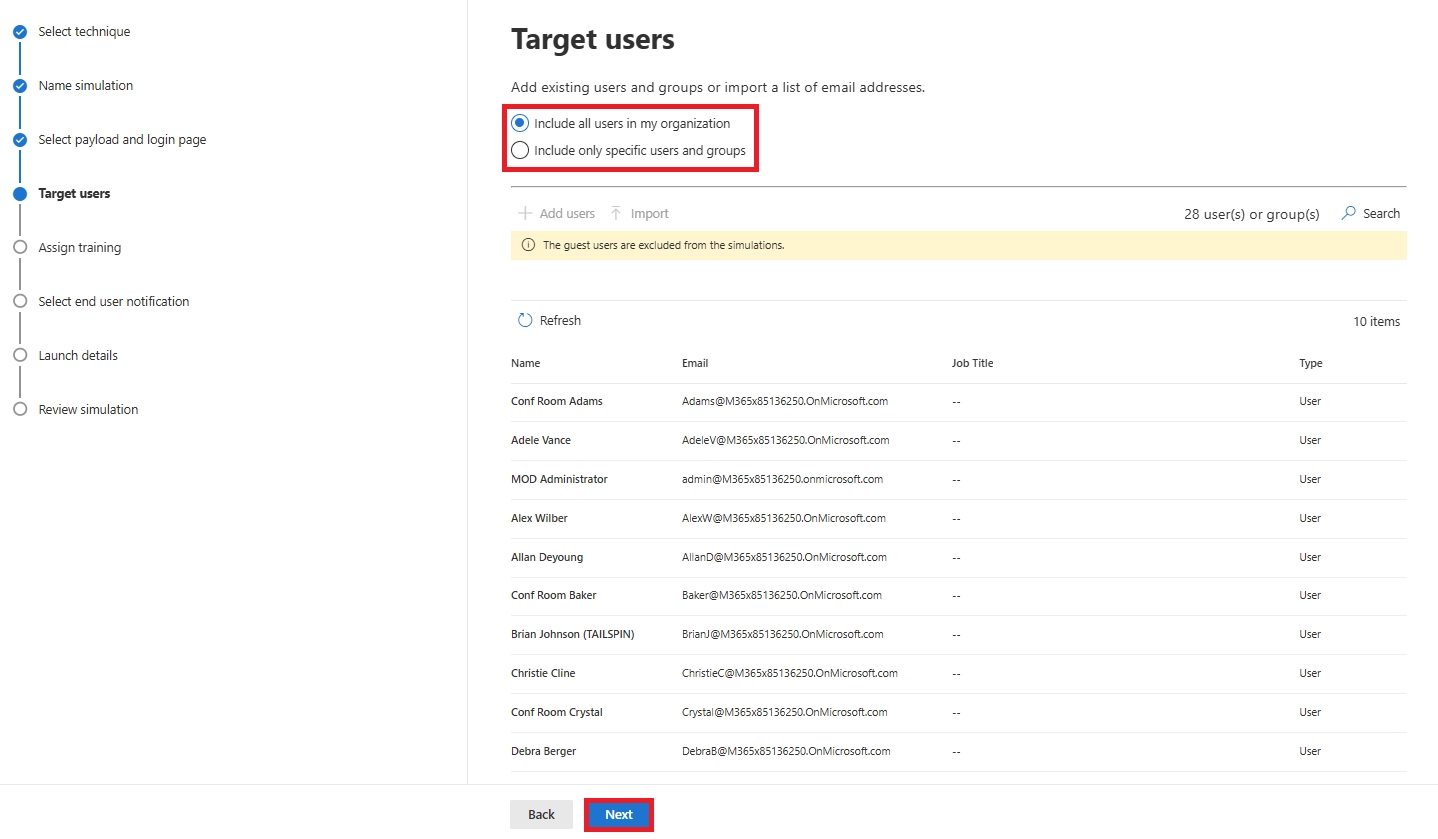
Q19. Can I target only specific departments or groups?
Yes. You can use Entra ID groups, Microsoft 365 groups, or dynamic groups for advanced targeting.
Q20. Does Attack Simulation Training support automated recurring campaigns?
Yes - through Simulation Automations, allowing monthly or randomized phishing tests.
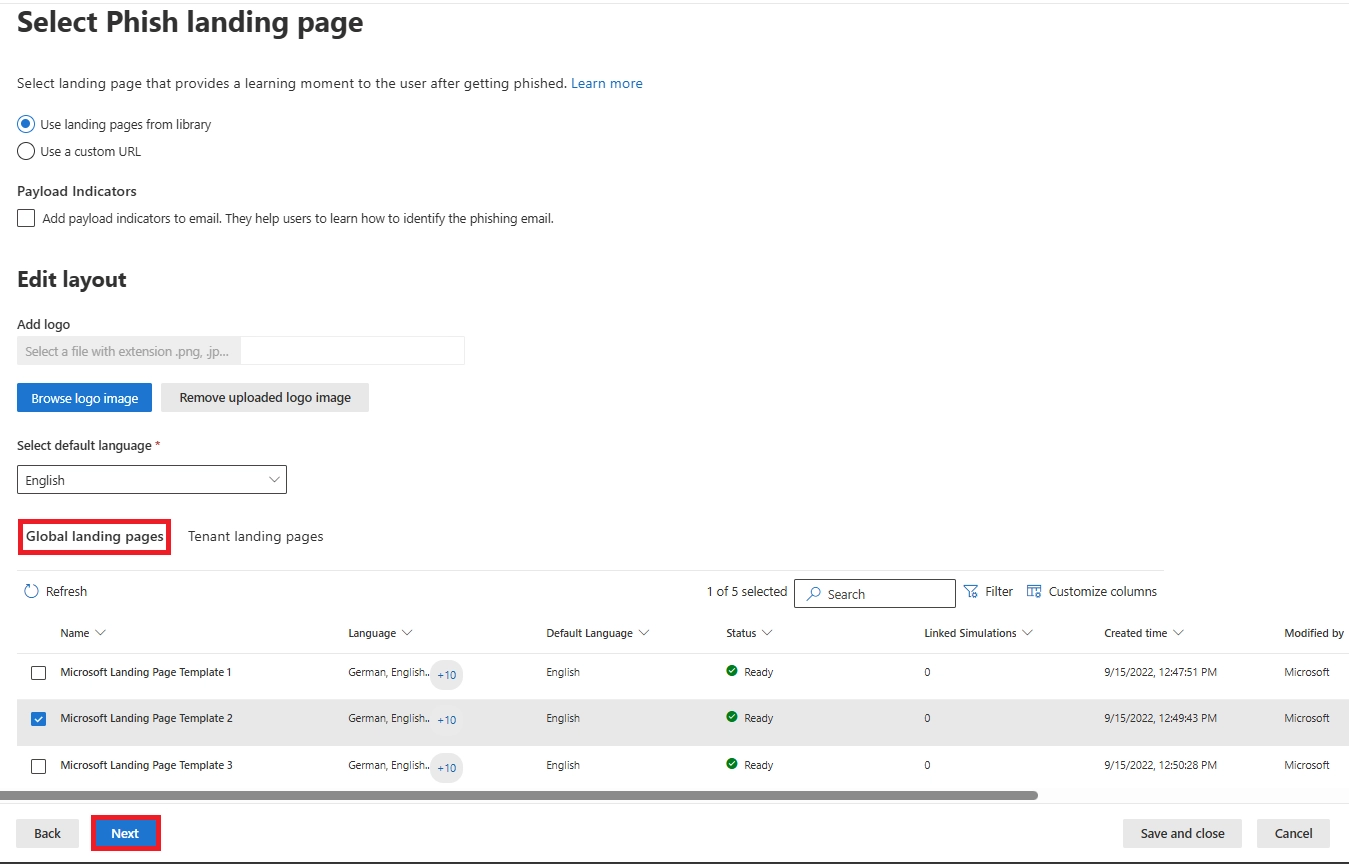
Q21. Can I customize the landing page shown to users who click?
Yes. Use the default Microsoft landing page or upload your own branded phish landing page.
Q22. Can Safe Links or Safe Attachments interfere with simulations?
Sometimes. Safe Links rewriting or external proxies may trigger false clicks. Whitelisting simulation URLs helps.
Q23. Do simulations store real passwords when users enter credentials?
No. Microsoft never stores or uses real passwords - only the action is logged.
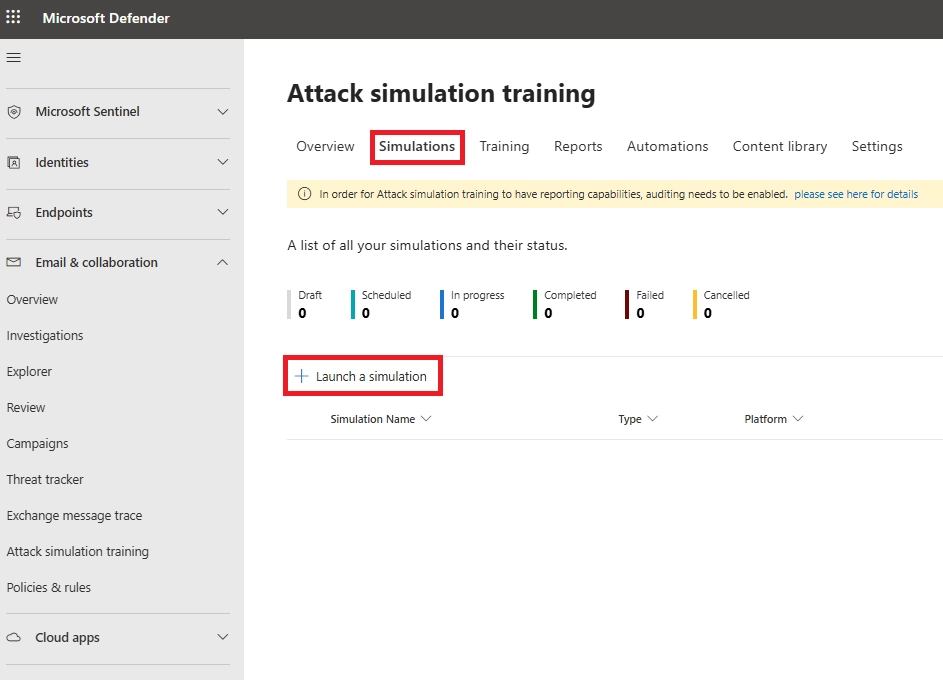
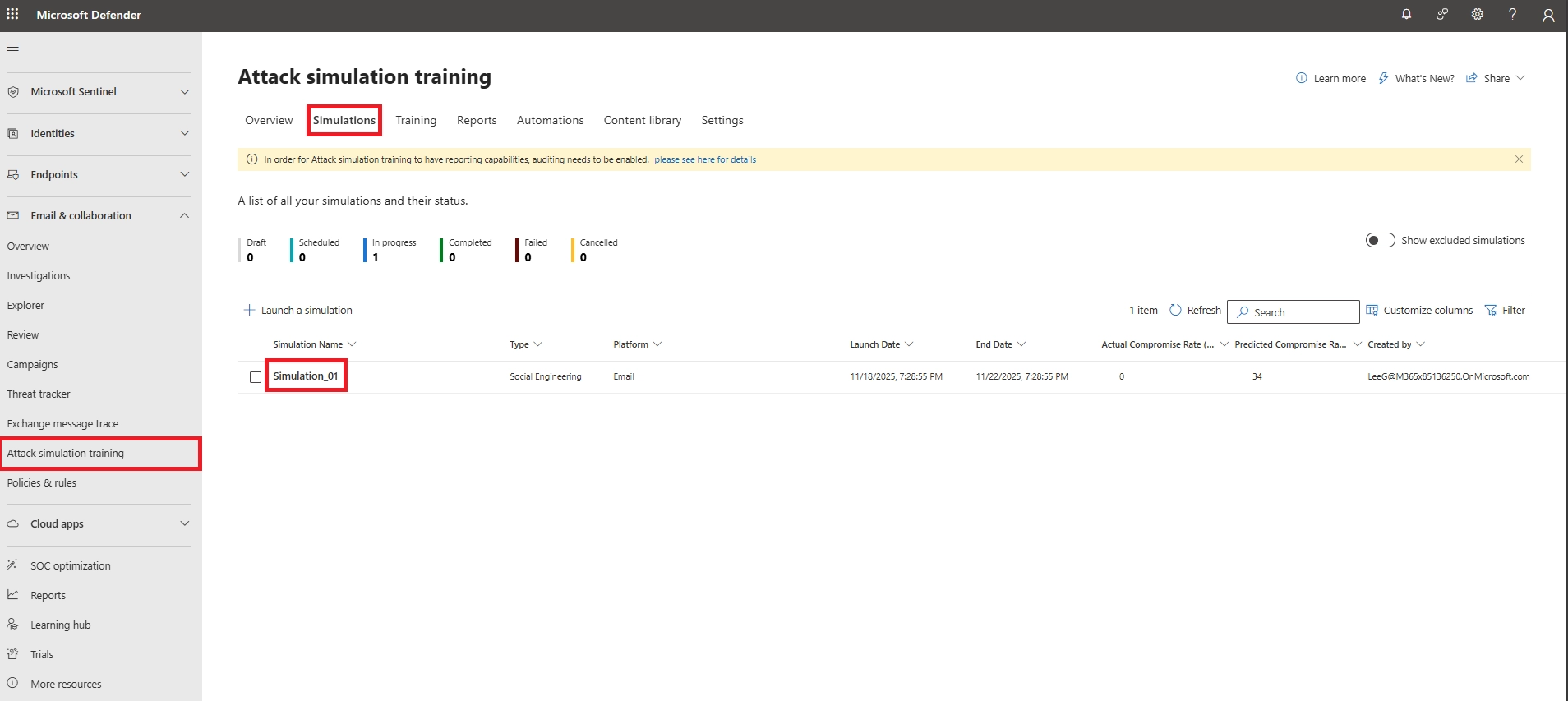
Q24. Can I download detailed Microsoft 365 attack simulation reports?
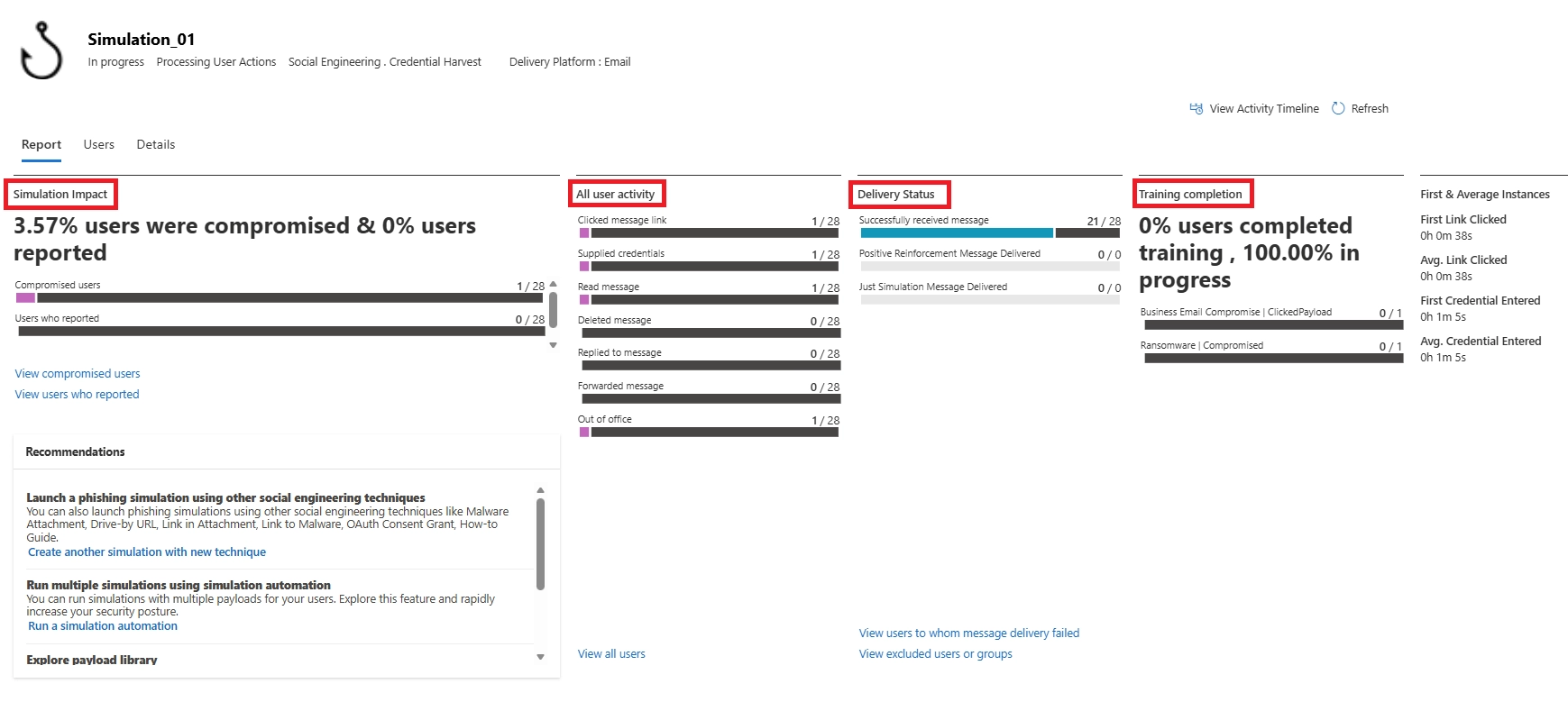
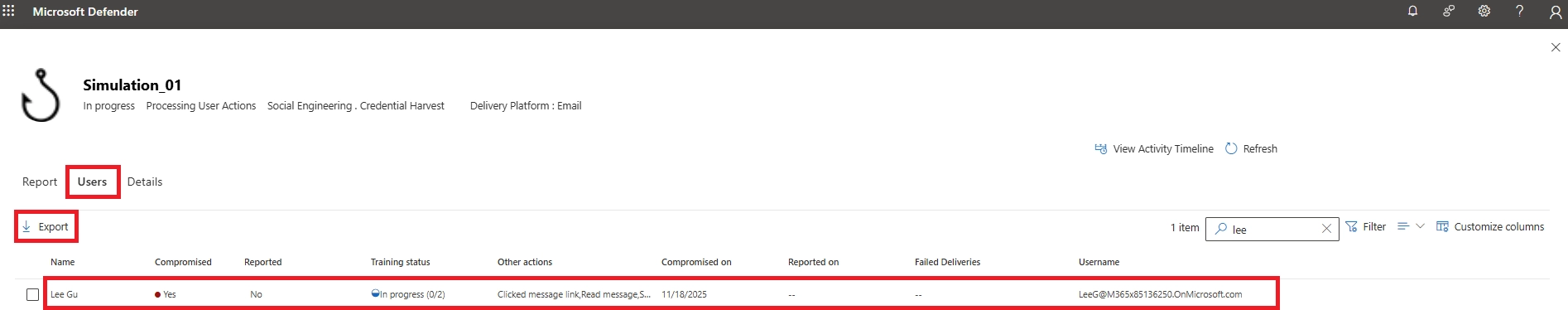
Yes. You can export detailed user actions, click rates, and compromise rates as CSV.
Q25. How do I improve low report rates in phishing simulations?
Enable “Report Phishing” add-ins, run awareness sessions, and reward users who report - key steps in Microsoft Defender attack simulation training best practices.