Q1. What are Safe Attachments in Microsoft 365?
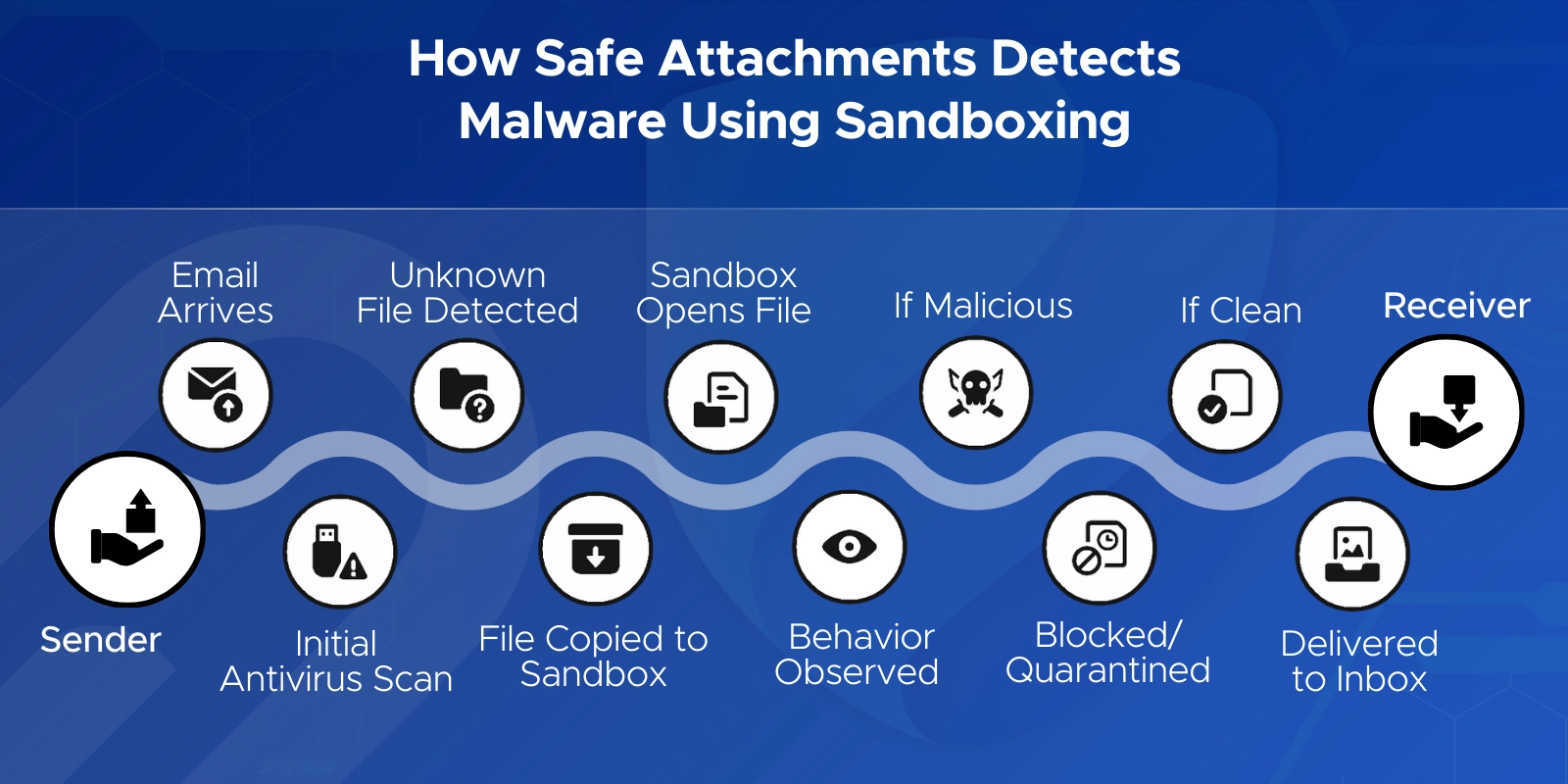
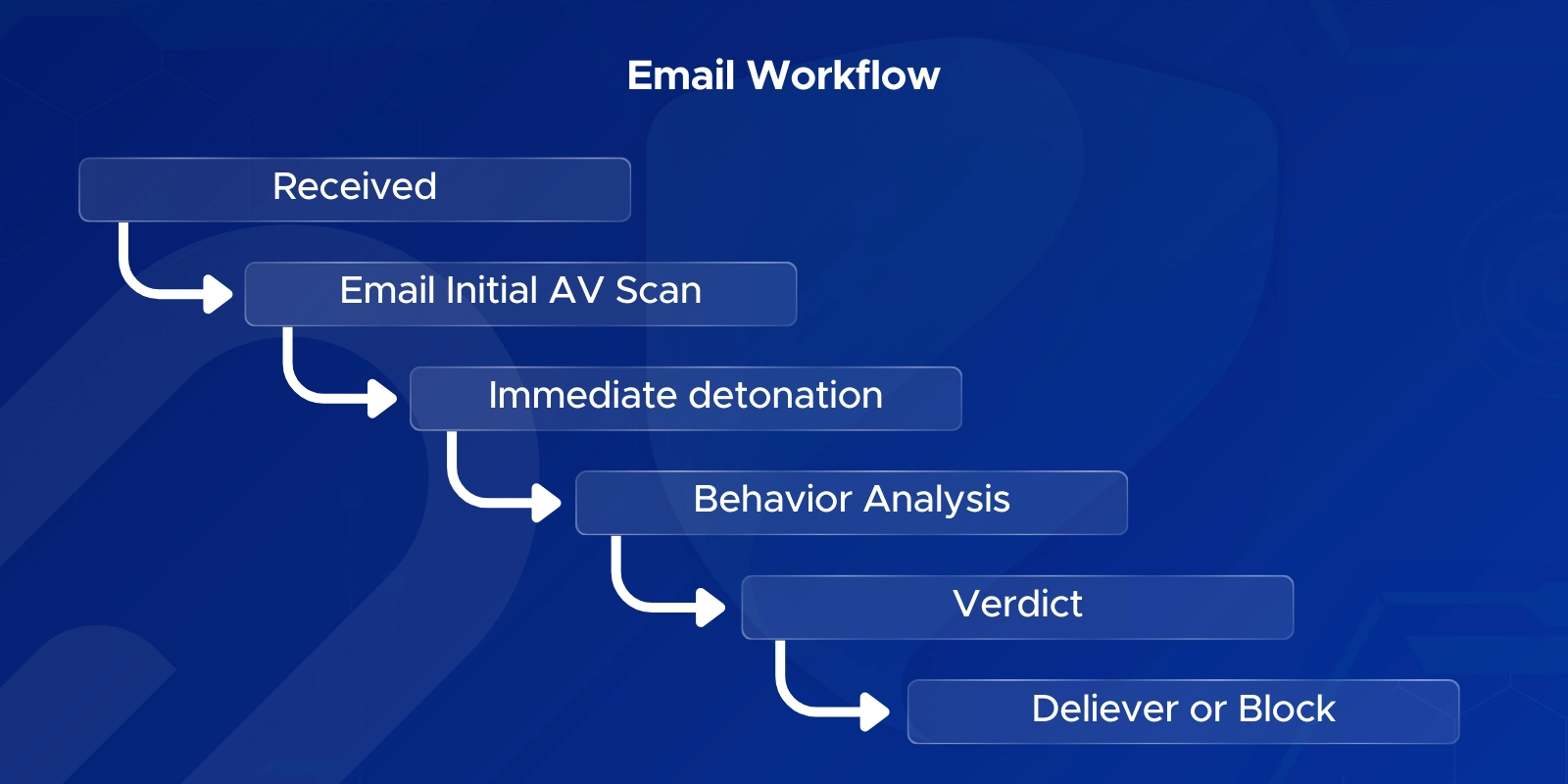
Safe Attachments is a Microsoft Defender for Office 365 feature that opens files in a virtual sandbox to check for harmful behavior. Unlike regular antivirus, which checks signatures, Safe Attachments detects unknown malware, zero-day attacks, and hidden scripts by detonating the file before it reaches users.
Q2. How does sandboxing (detonation) work in Safe Attachments?
Safe Attachments copies the file to a secure virtual environment, opens it, and observes its behavior. If the attachment tries to run scripts, download malware, or modify system areas, it’s blocked. Most Safe Attachments sandbox scans finish in 2–15 minutes.
Q3. Will Safe Attachments delay my emails?
There may be a short delay, but using Dynamic Delivery ensures the email body arrives instantly while the attachment is scanned. The attachment appears when cleared by the sandbox. This keeps the workflow smooth without sacrificing security.
Q4. Why enable Safe Attachments for SharePoint, OneDrive, and Teams?
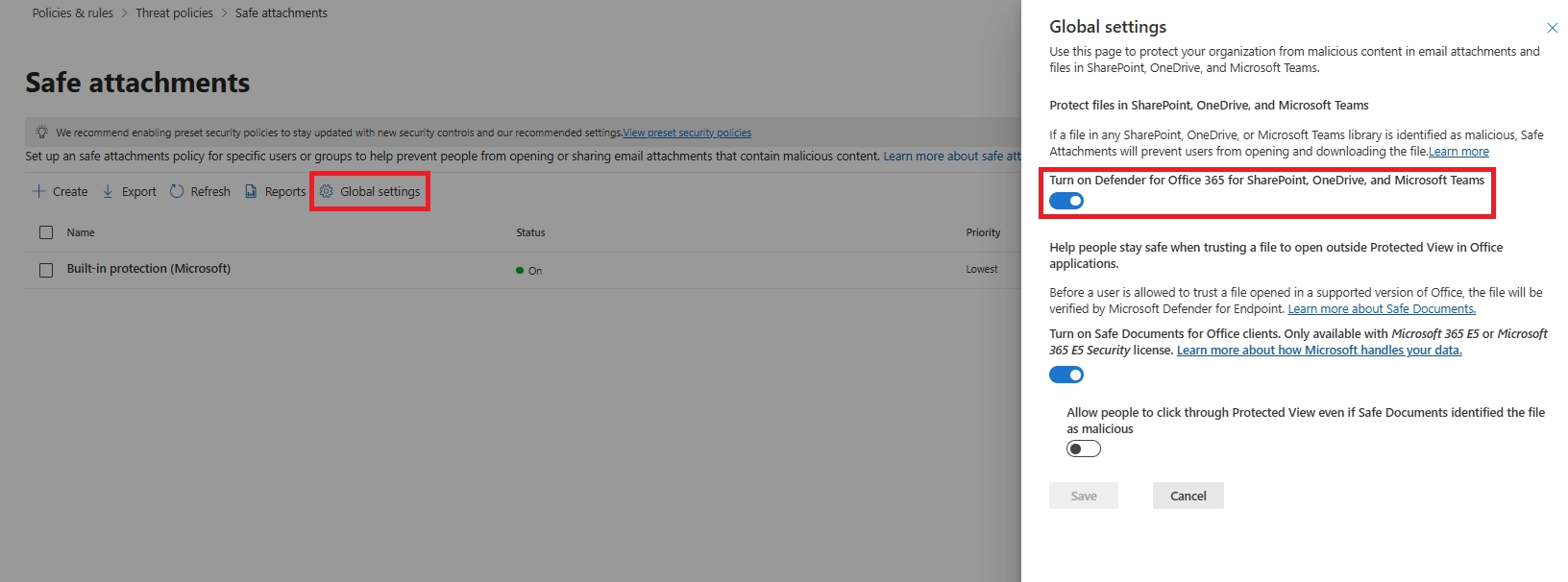
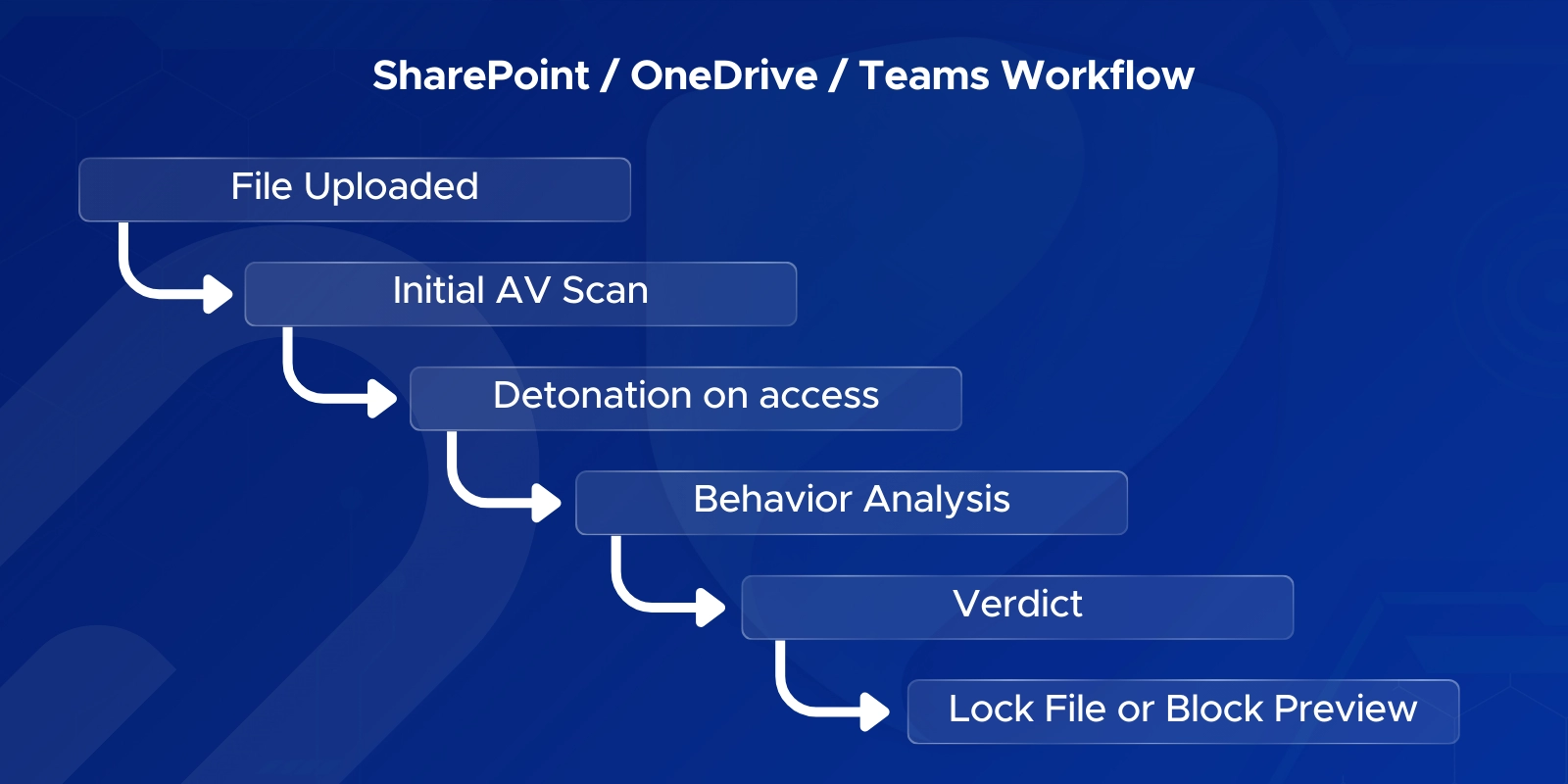
Safe Attachments protection for SharePoint, OneDrive, and Teams prevents malicious files uploaded or shared in cloud libraries from spreading internally. It scans files asynchronously when someone opens, previews, or shares them—blocking unsafe content before others access it.
Q5. How does Safe Attachments for SharePoint, OneDrive, and Teams work?
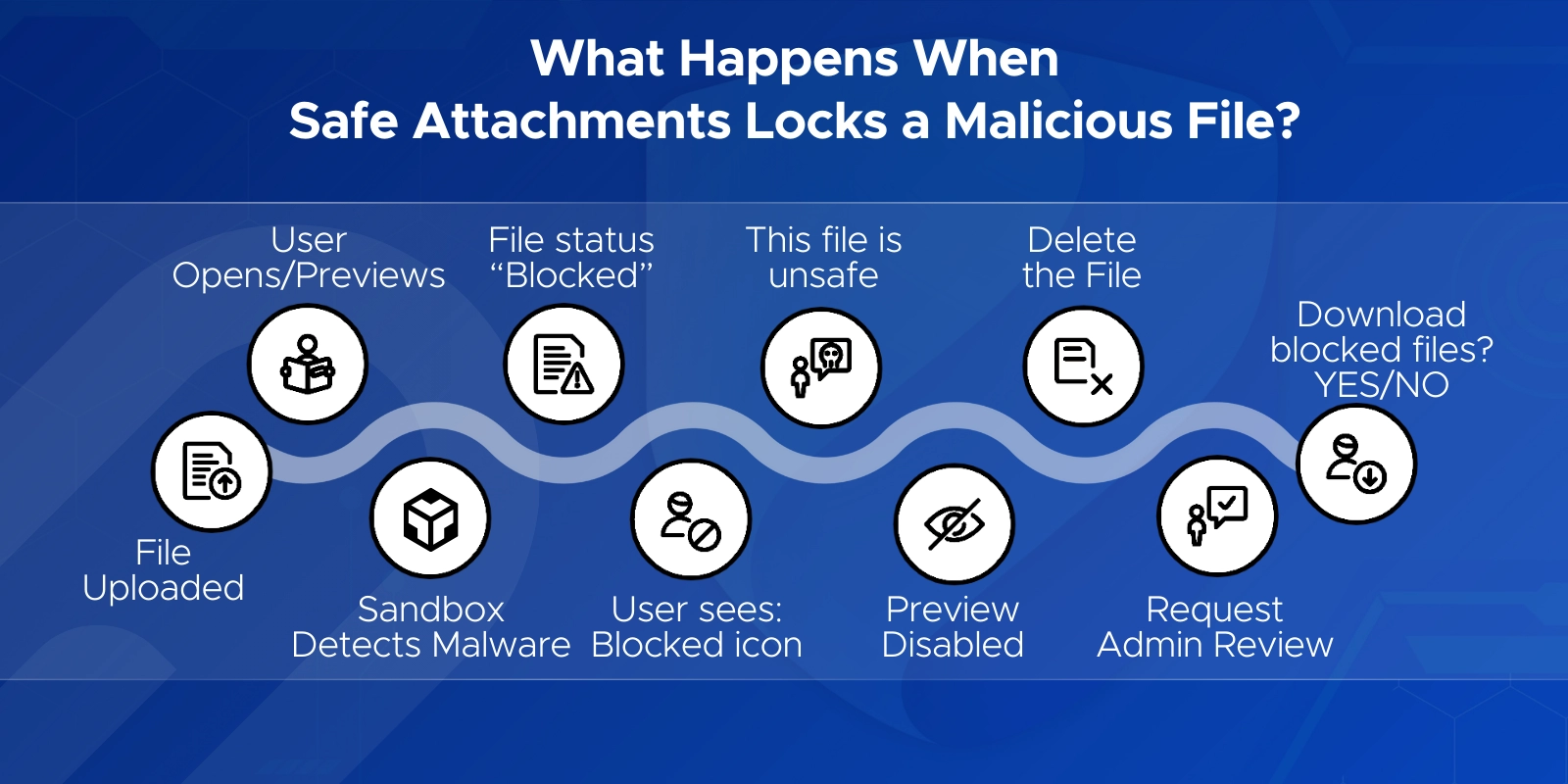
Files first pass a basic malware scan. When a user interacts with the file, Safe Attachments detonates it in a sandbox. If it’s malicious, the file becomes “locked,” can’t be opened or shared, and shows a blocked icon in modern SharePoint or Teams.
Q6. Why can users still download malicious files in SharePoint/OneDrive even with Safe Attachments enabled?
Because downloads are allowed by default. To block downloads of infected files, run:
Set-SPOTenant -DisallowInfectedFileDownload $true
This closes a common loophole many admins miss.
Q7. Which Microsoft 365 license includes Safe Attachments?
Safe Attachments is included in Microsoft Defender for Office 365 Plan 1 and Plan 2. M365 E5 and O365 E5 include P2 automatically, while E3 plans can add P1/P2. Plan 1 gives core Safe Attachments protection; Plan 2 adds automation, enhanced reporting, and preset security policies.
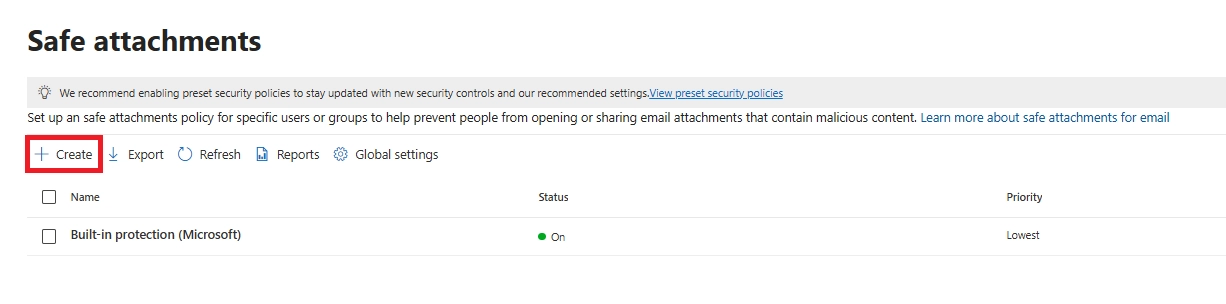
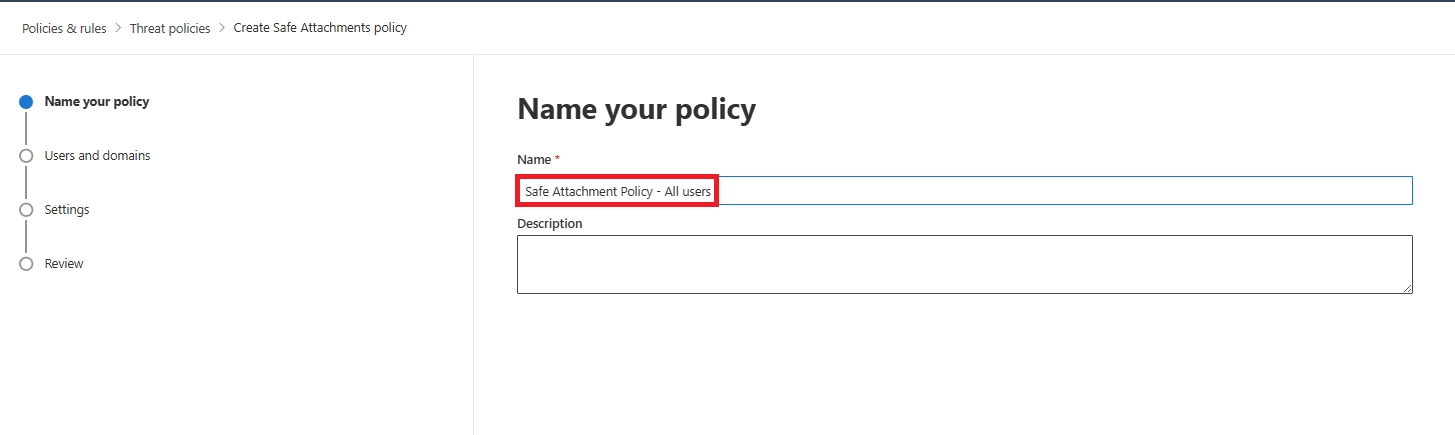
Q8. How do I set up a Safe Attachments policy in Office 365 quickly?
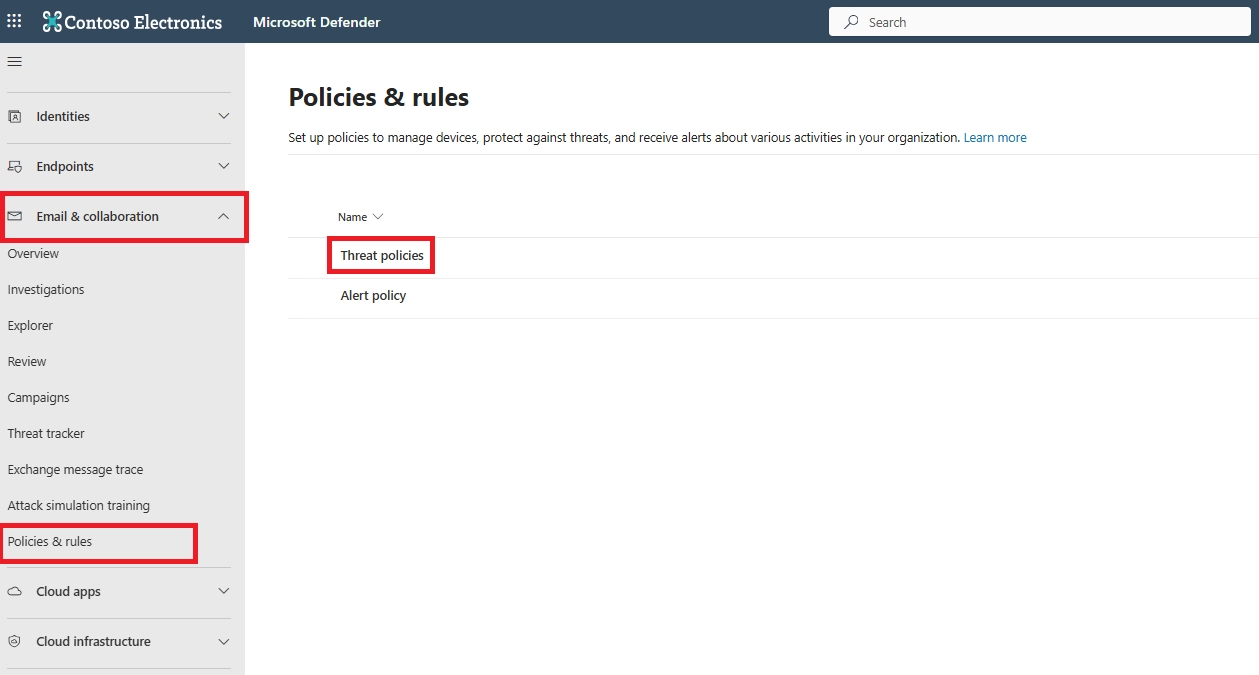
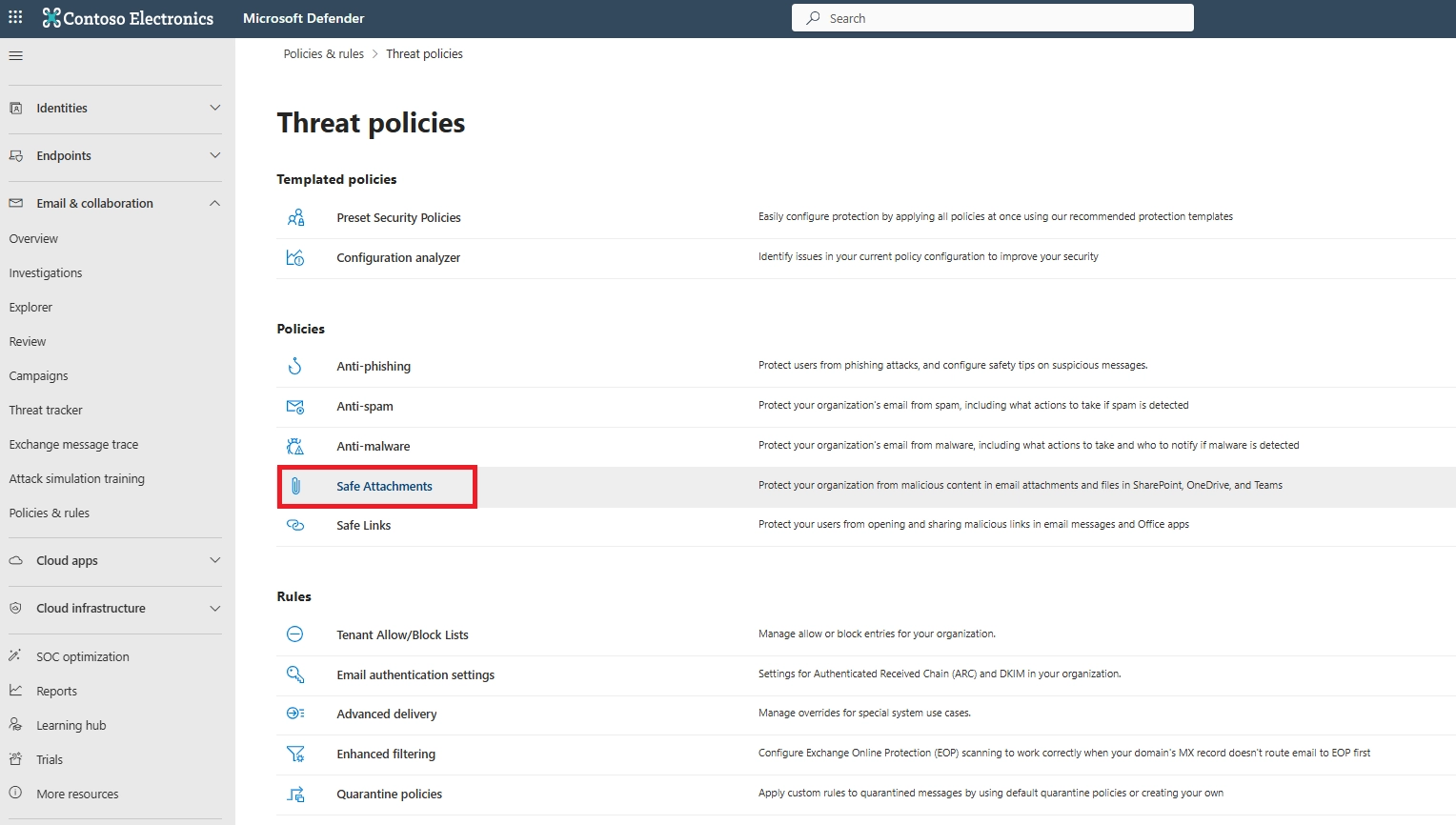
Go to the Microsoft 365 Defender portal → Email & Collaboration → Policies & Rules → Threat Policies → Safe Attachments → Create Policy. Add recipients, choose the action (Dynamic Delivery or Block), and save. This creates a tenant-specific Safe Attachments policy for email.
Q9. What is the best Safe Attachments policy mode to use?
Most organizations prefer Dynamic Delivery because it delivers emails instantly while scanning attachments in the background. “Block” offers maximum security but delays the entire email until the scan completes.
Q10. Why is my Safe Attachments policy not applying to some users?
Check:
- Policy scope (are the users included?)
- Priority order (a different policy may override)
- Licensing (users must have Defender for Office 365)
- Microsoft preset policies (Standard/Strict may take precedence)
- Propagation time (wait 30–60 minutes for new policies)
Q11. How do I know if an attachment is safe in Office 365?
Safe Attachments scans the file in a sandbox. If it’s safe, it’s delivered or re-attached (Dynamic Delivery). You can also check Quarantine, Threat Explorer, or the Safe Attachments report in the Defender portal to verify actions taken.
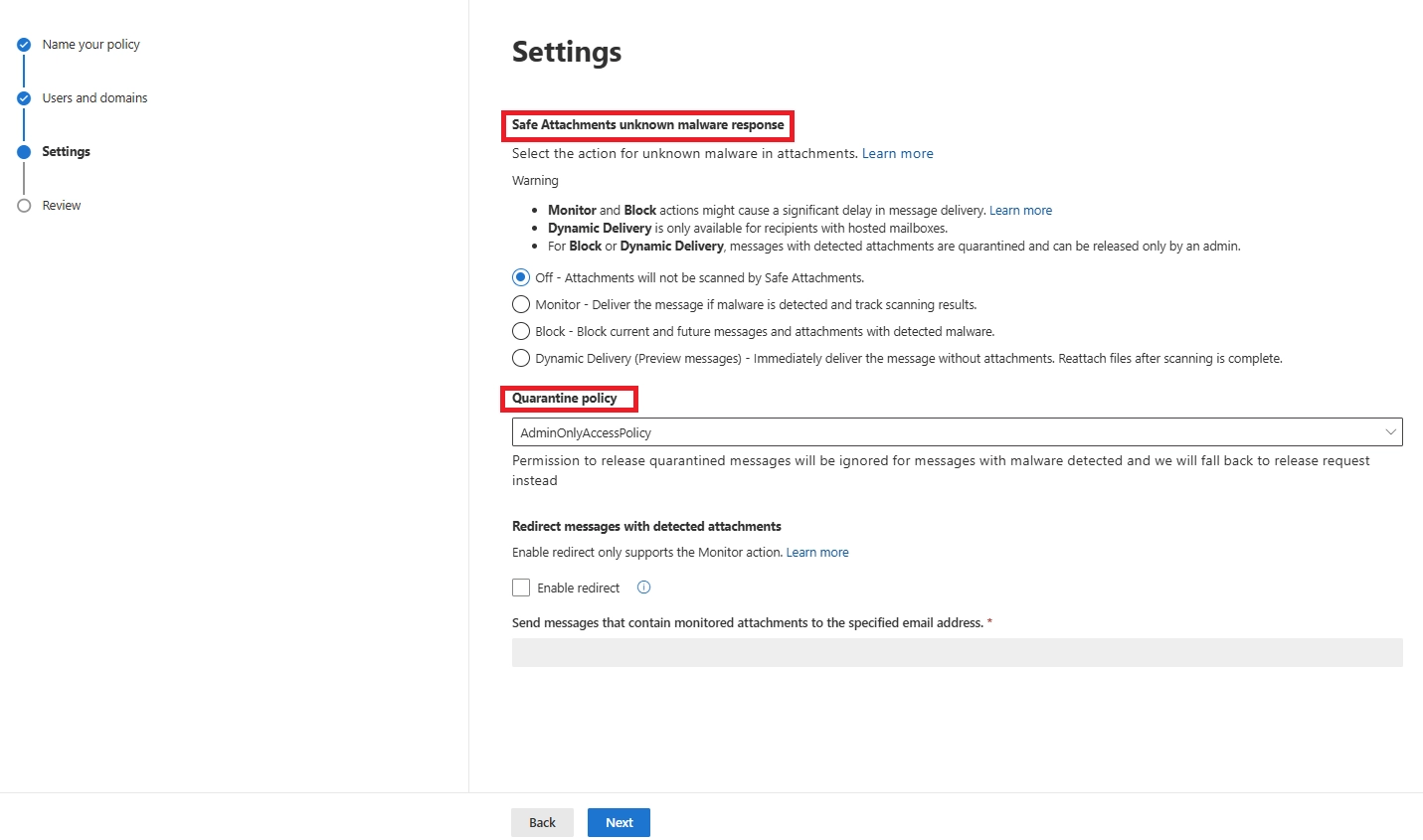
Q12. What is Safe Attachments Unknown Malware Response?
This setting decides what happens when a file is being scanned. “Dynamic Delivery” replaces the attachment with a placeholder until it’s verified. “Block” holds the entire message. It’s a key configuration step in Safe Attachments policy setup.
Q13. What is SafeDocs (Safe Documents) in Microsoft 365?
Safe Documents is an E5 feature that opens Office files in protected mode until Microsoft finishes scanning them. It works alongside Safe Attachments to add an extra layer for Office files opened directly in desktop apps.
Q14. Does Safe Attachments work for Microsoft Teams files?
Yes. Files shared in Teams are stored in SharePoint and processed by Safe Attachments the same way as SharePoint/OneDrive files. If malicious, Teams will show an error or block preview.
Q15. How do I test if Safe Attachments is working?
Send an EICAR test file to a mailbox protected by Safe Attachments—it should be quarantined.
Upload EICAR (inside a ZIP) to SharePoint/OneDrive—the file should get flagged and locked shortly after.
Q16. What should I do if Safe Attachments detects malware?
Do not release the file immediately. Review Quarantine details, inform the user, and investigate the sender. If it’s a false positive, you can submit the file to Microsoft. If it’s real malware, block the sender, check for similar emails, and review user activity.
Q17. What is the difference between Safe Attachments and Safe Links?
Safe Attachments scans files in a sandbox.
Safe Links scans URLs and detonates malicious websites or linked files.
Together, they provide file-level and link-level protection across Microsoft 365.
Q18. What is Office 365 Safe Mode for attachments (Outlook attachment security)?
Outlook’s “Protective View” or “blocked attachment types” is client-side protection.
Safe Attachments is server-side protection.
Safe Attachments stops threats before they ever reach Outlook.
Q19. How do Safe Attachments policies relate to Preset Security Policies?
If Standard/Strict presets are enabled, they may override or apply before your custom Safe Attachments policies. Check policy priority and scope to avoid unexpected behavior.
Q20. What file types can Safe Attachments scan?
Most common file types are analyzed. Encrypted or password-protected archives may not fully detonate, so use mail flow rules or additional checks for those cases.