Q: What is the difference between a role and a role assignment?
A: A role defines a set of permissions (what you can do). A role assignment links a user or group to that role, granting them those permissions.
Q: What are the three types of RBAC controls in Azure?
A: Azure uses Role Assignments, Role Definitions, and Scopes.
- Role Assignment: Gives a user/group a role at a specific scope.
- Role Definition: The actual set of permissions (e.g., Reader, Contributor).
- Scope: Where the permissions apply (subscription, resource group, or resource).
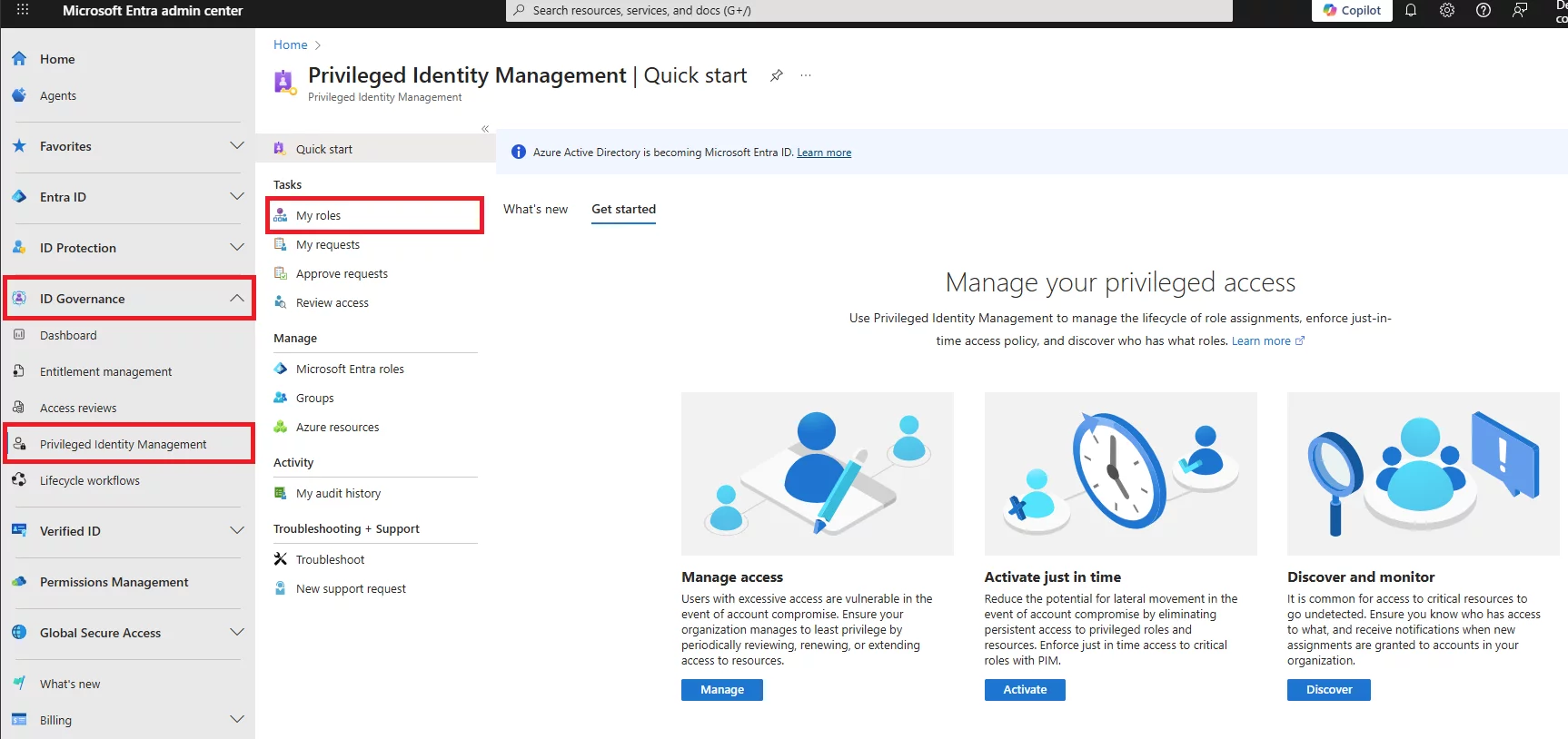
Q: What is the difference between IAM and PIM?
A: IAM (Identity and Access Management) is the broad system that handles who can access what. PIM (Privileged Identity Management) is a layer on top of IAM that manages privileged roles, providing just-in-time access, approvals, and audit logs.
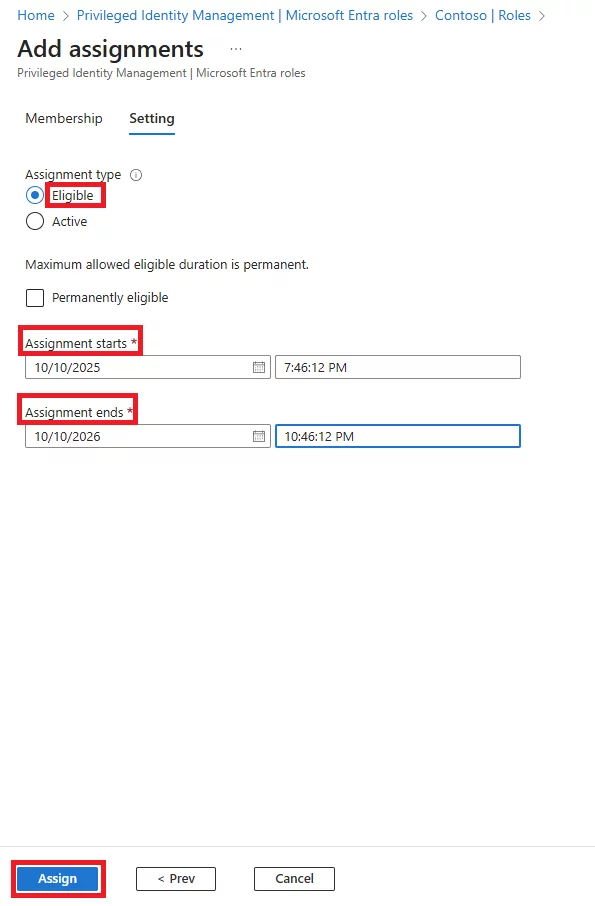
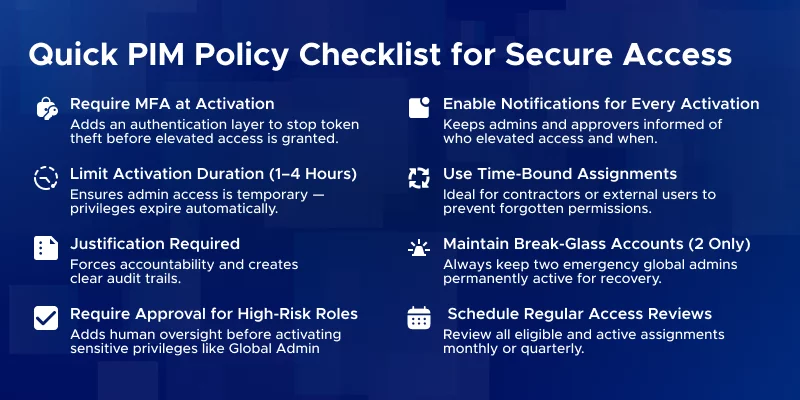
Q: What is the difference between eligible and active PIM roles?
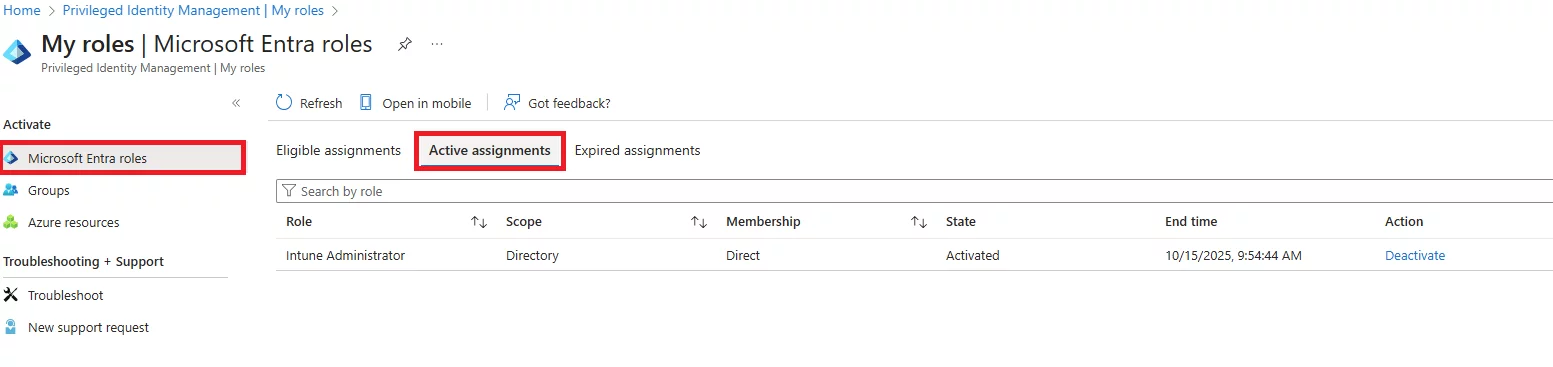
A: Eligible roles must be activated each time you need them – temporary, just-in-time access. Active roles are always on – the user has admin permissions at all times. Eligible = “on demand,” Active = “standing access.”
Q: When should I use an eligible role vs an active role in PIM?
A: Use eligible roles by default for day-to-day administration. Use active roles only for exceptions like break-glass accounts or service accounts that cannot use JIT activation. Eligible roles reduce risk by limiting exposure.
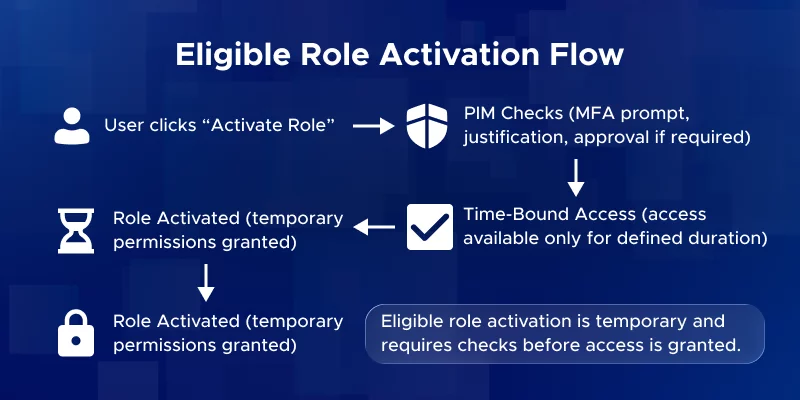
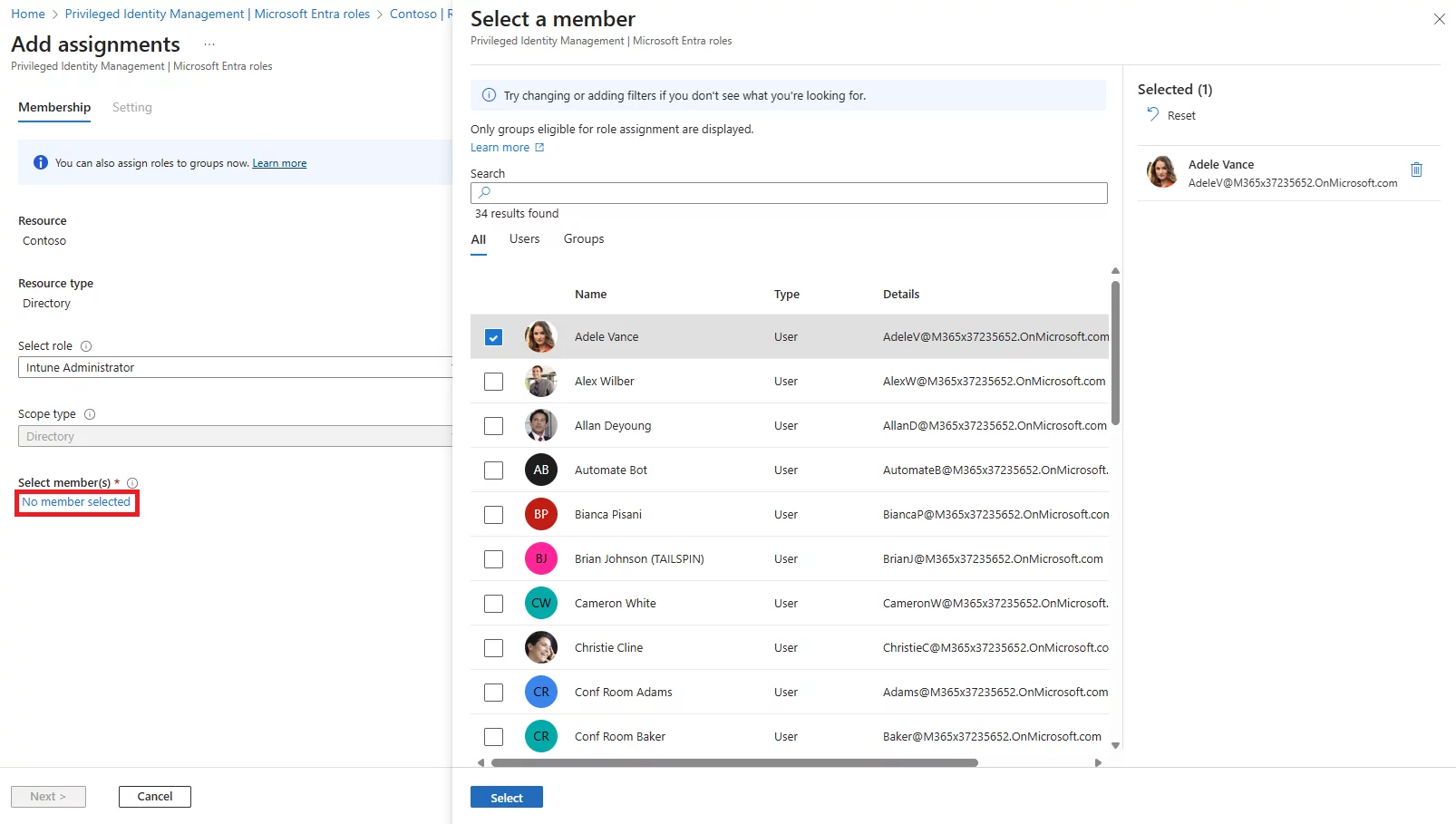
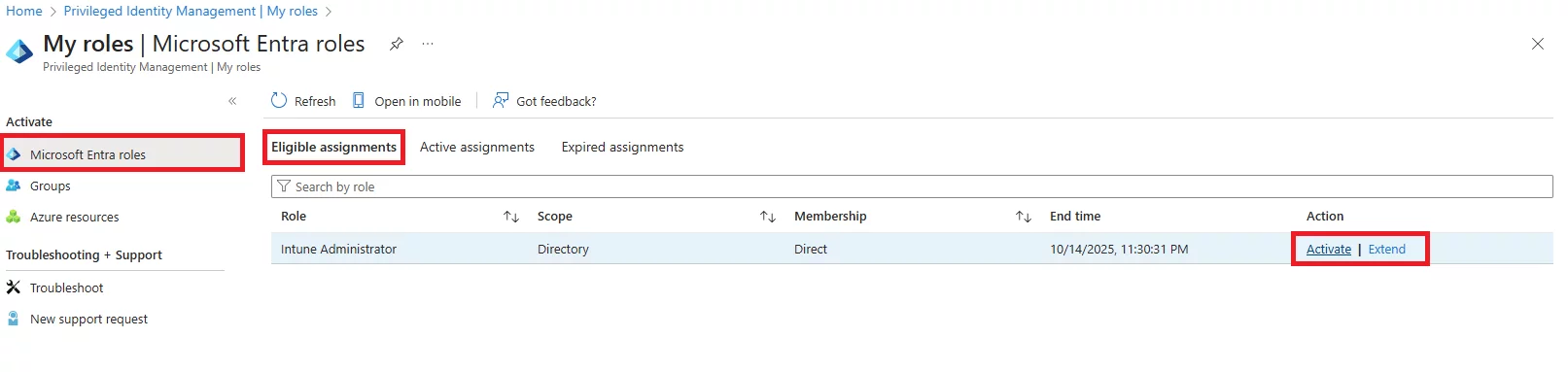
Q: How do users activate an eligible PIM role?
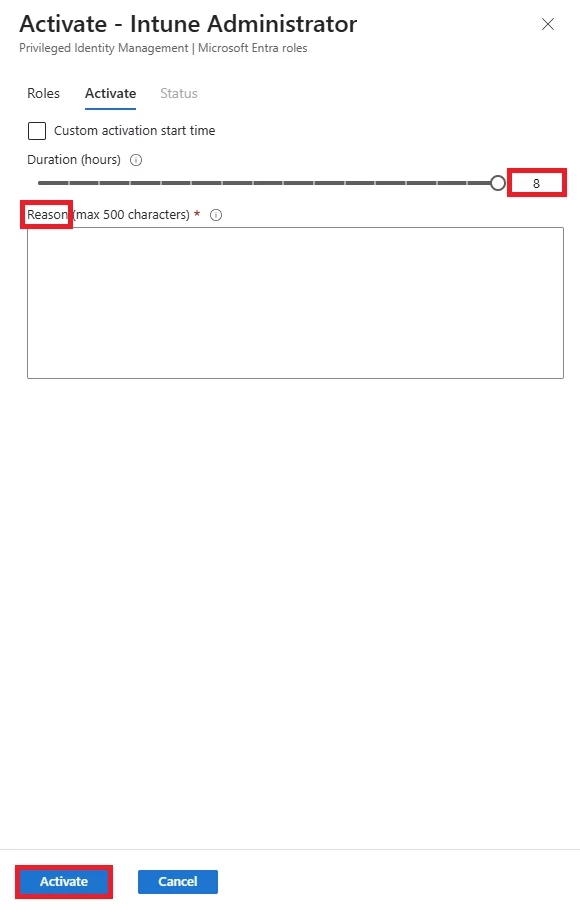
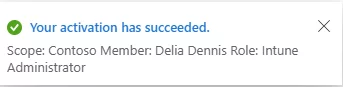
A: Users go to the PIM portal (or Teams/PIM app), select their eligible role, click Activate, and complete any requirements like MFA or providing justification. If approval is required, they wait for it. Once done, the role is active for the set duration (e.g., 1–4 hours).
Q: Can eligible PIM roles expire or be time-bound?
A: Yes. Eligible assignments can have a set expiry date, after which the user loses eligibility. Each activation also expires after a configured duration, after which the user must activate again.
Q: What triggers the activation of an eligible PIM role?
A: Activation is manual. The user must intentionally start it in PIM. Scripts can automate this via PIM API, but it’s always a deliberate action, not automatic.
Q: Are active PIM roles more risky than eligible roles?
A: Yes. Active roles give standing access, so if compromised, the attacker immediately has permissions. Eligible roles add MFA, approval, and logging, which creates security checkpoints and audit trails.
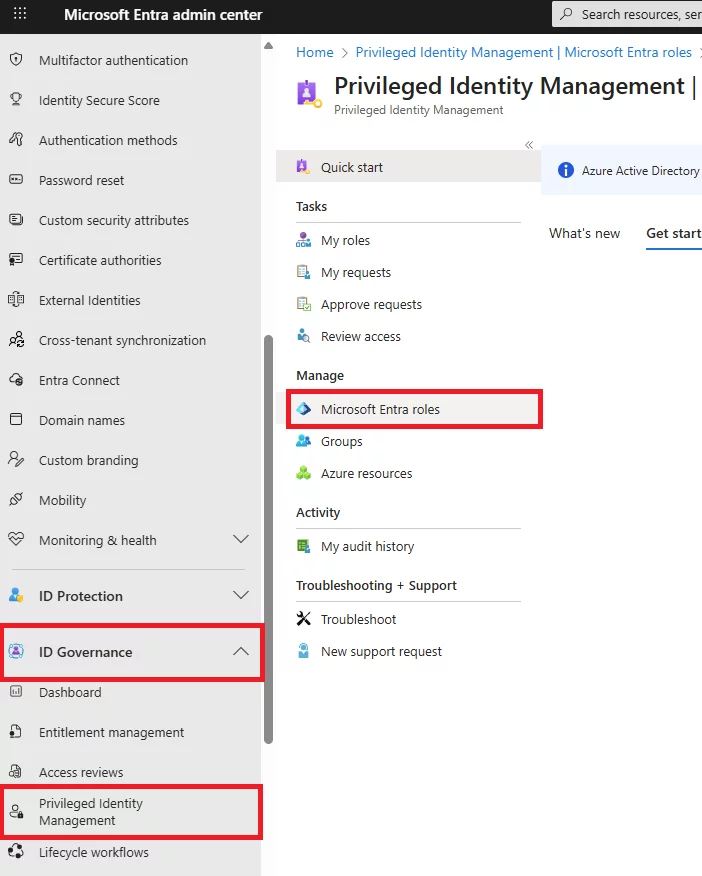
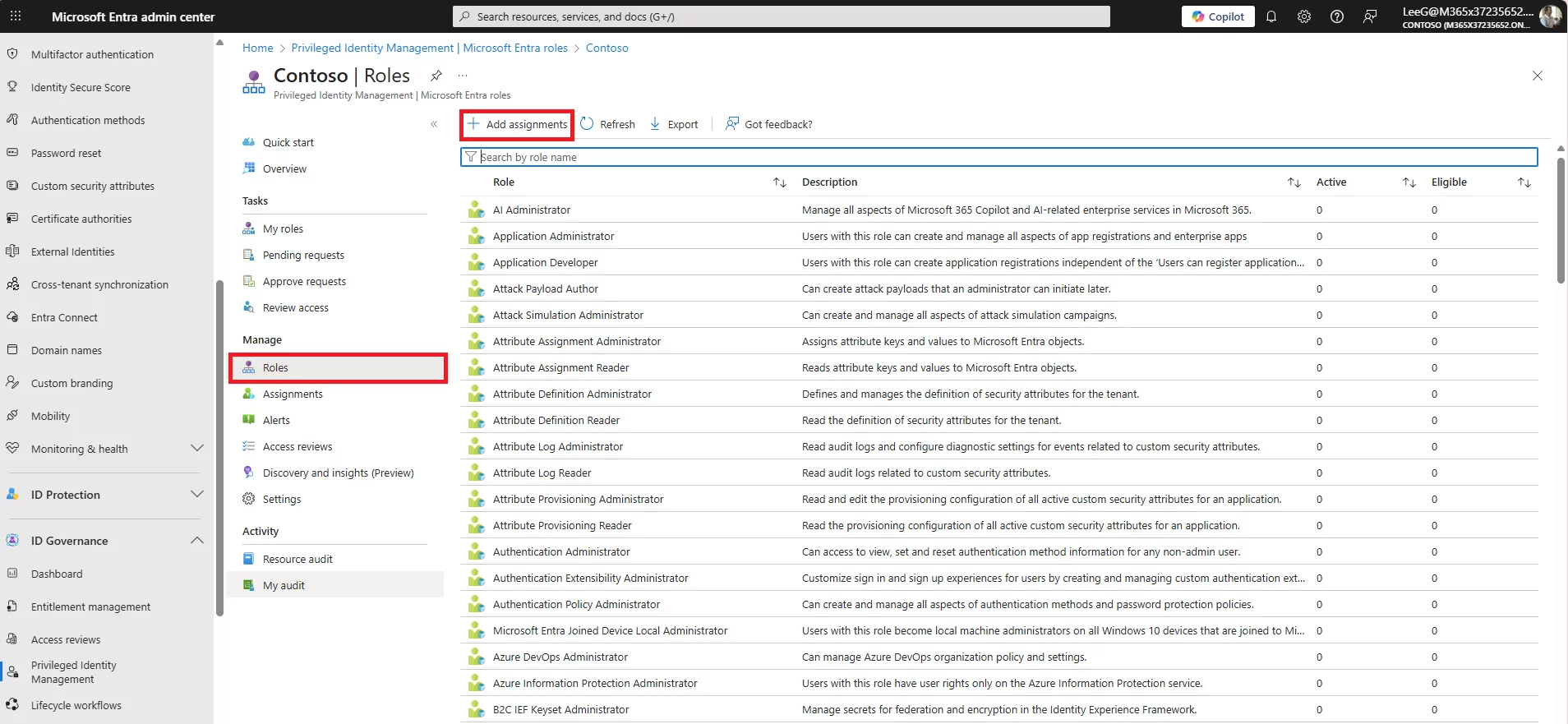
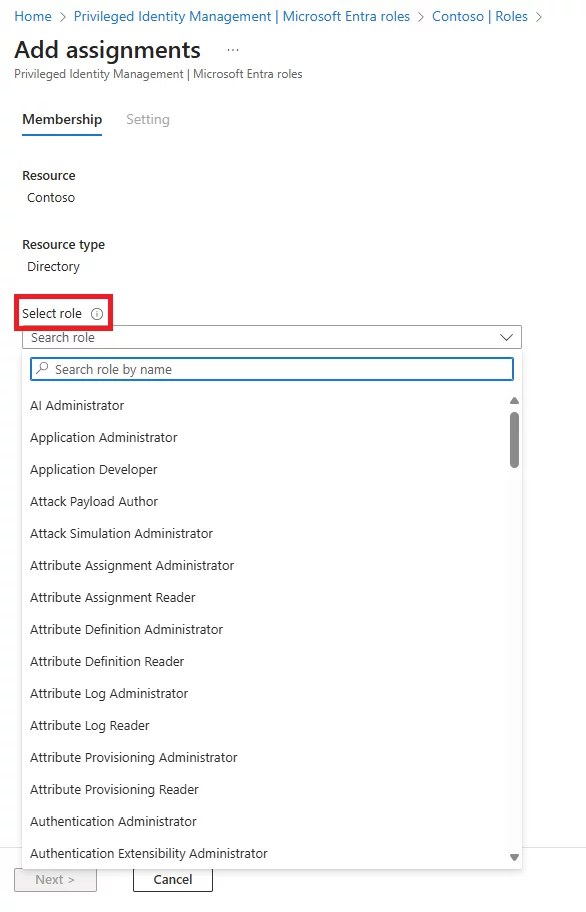
Q: How to activate eligible assignments in Azure?
A: Through the Entra/PIM portal, select your eligible role, click Activate, satisfy any MFA/approval/justification requirements, and the role becomes active for the set duration.
Q: What are the permission levels in Azure?
A: Azure permission levels are defined by roles – e.g., Reader (view-only), Contributor (modify resources), Owner (full access). PIM controls elevated roles within these permissions.
Q: What is the scope type of roles in Entra?
A: Role scope defines where permissions apply: subscription, resource group, or specific resource. Eligible/active assignments inherit the role’s scope.
Q: How are NotActions used in a role definition?
A: NotActions define exceptions to permissions. For example, a role may allow all Contributor actions except deleting VMs. This refines what a role can do.
Q: Why is Add Role Assignment disabled?
A: This usually happens due to missing permissions or scope restrictions. The admin must have a high-enough role at the target scope to assign roles.