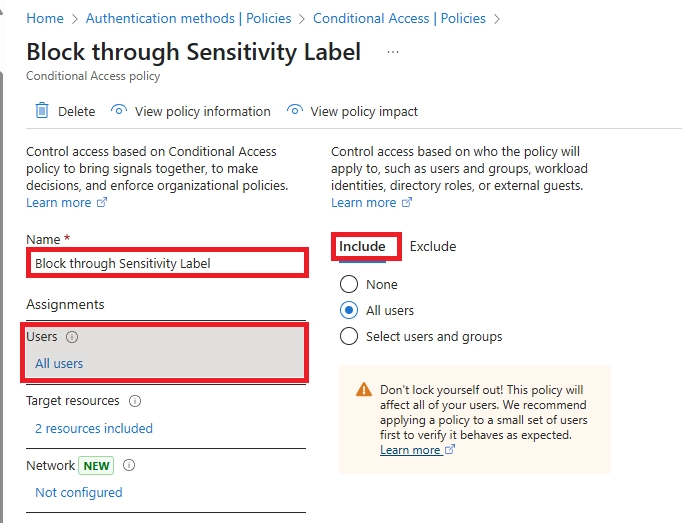
- Does Microsoft 365 block file downloads on mobile by default?
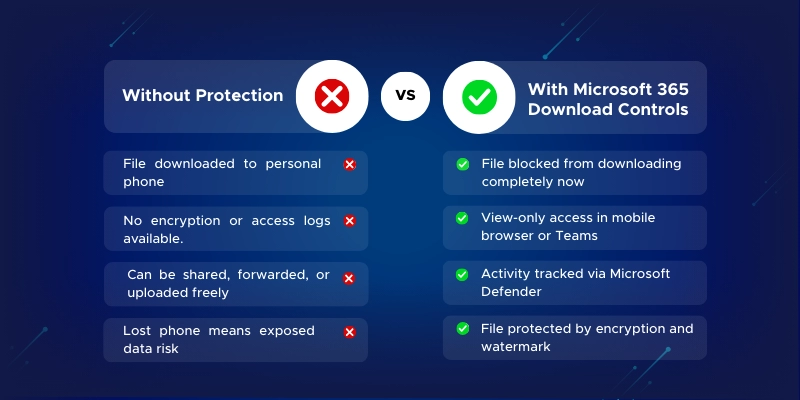
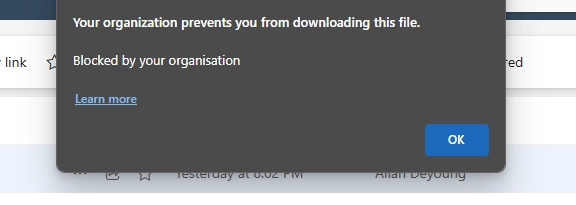
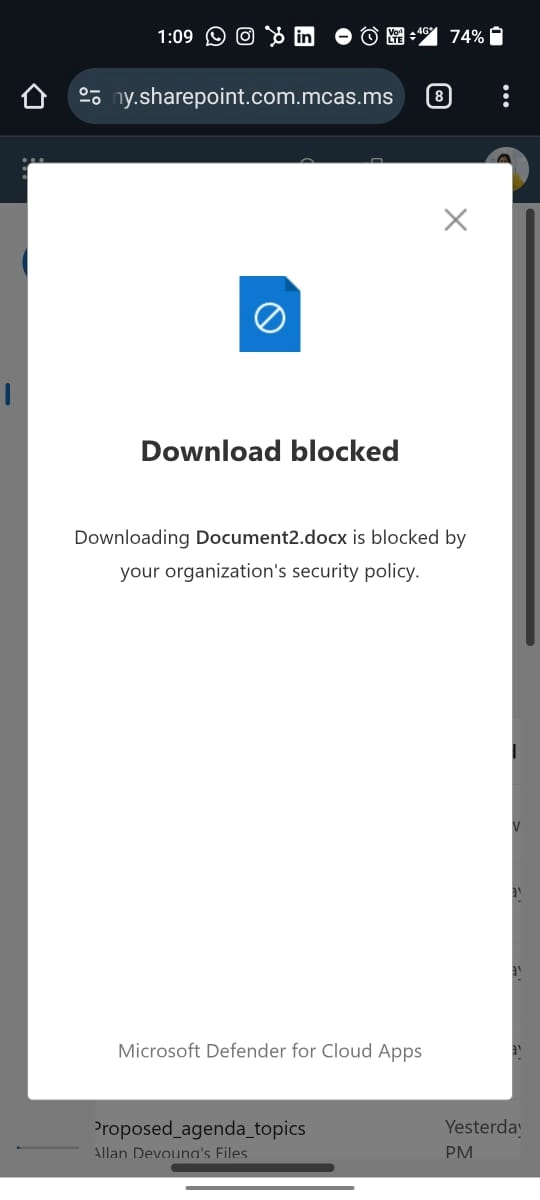
No. By default, Microsoft 365 apps like SharePoint, OneDrive, and Teams allow downloads across all devices, including mobile. To block this, you need to use Conditional Access, Defender for Cloud Apps, and/or Microsoft Purview sensitivity labels to enforce download restrictions.
- How do I stop people from downloading files from OneDrive?
Create a Conditional Access policy that targets OneDrive and applies to unmanaged or non-compliant devices. Combine it with Defender for Cloud Apps to block downloads in real-time. You can also use Purview sensitivity labels to restrict file usage.
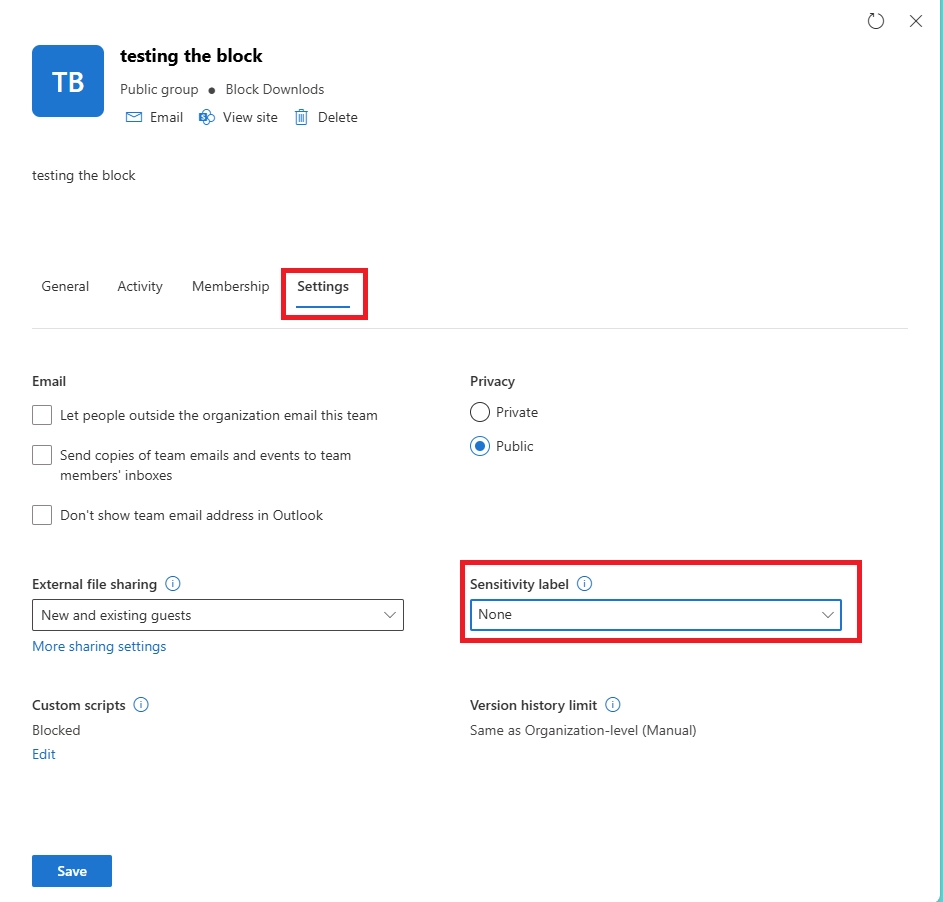
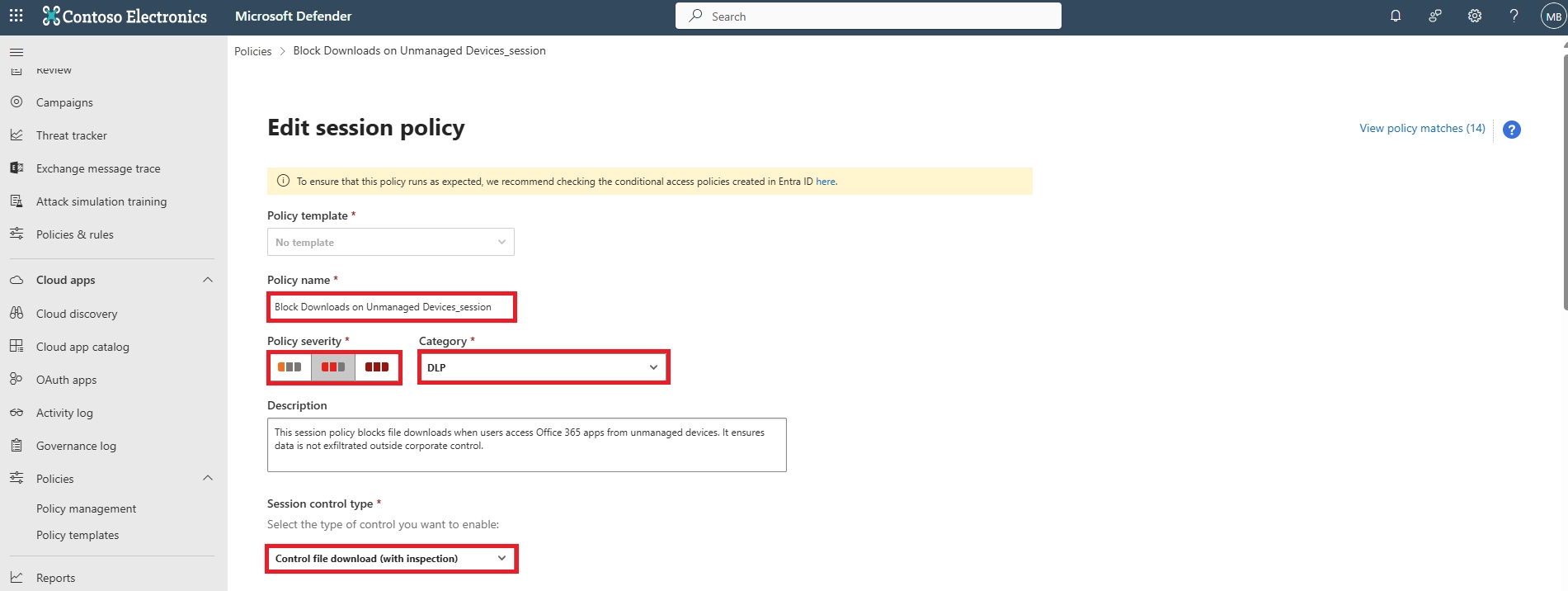
- How can I make a document view-only and not downloadable?
To make a document view-only:
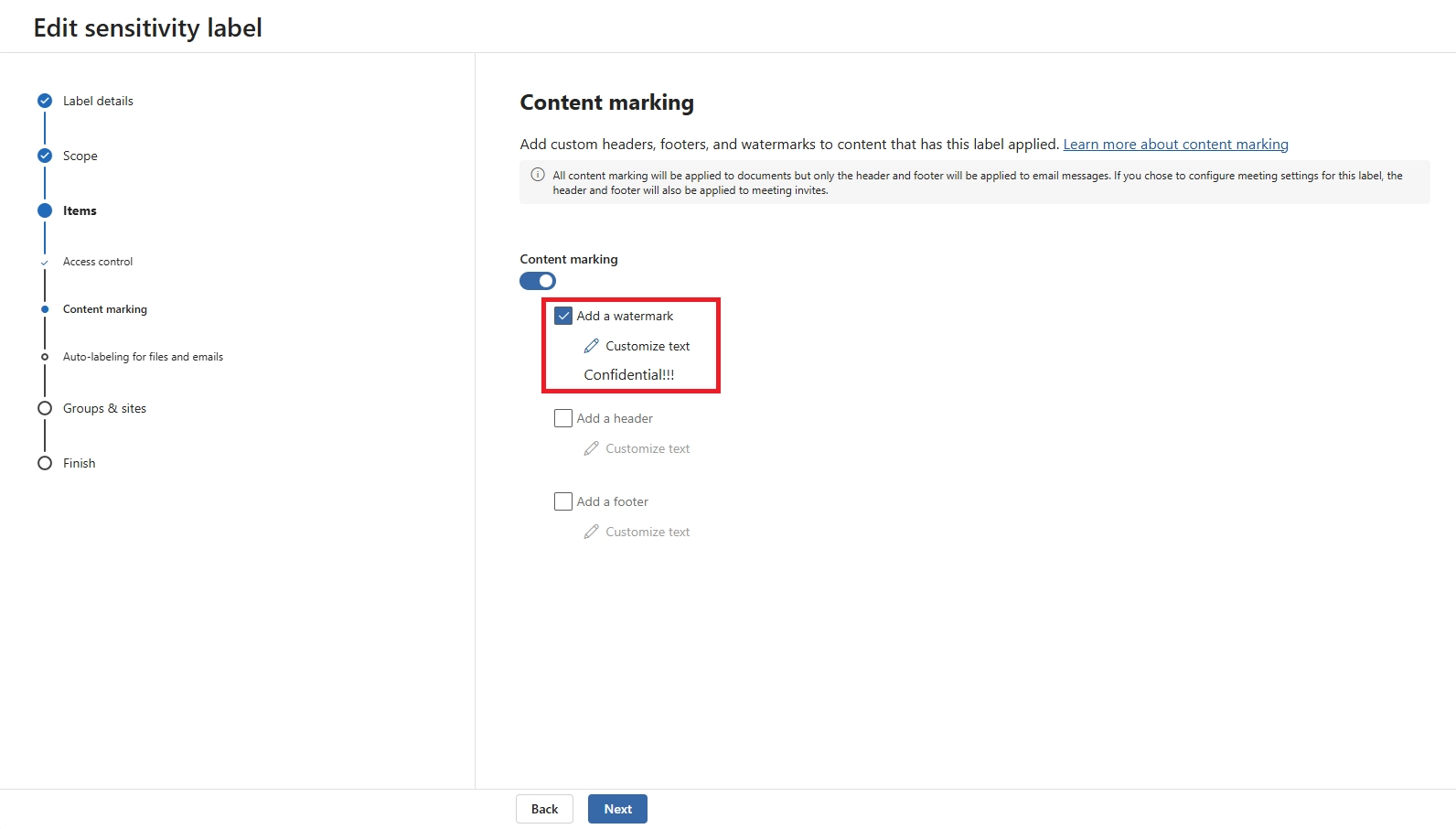
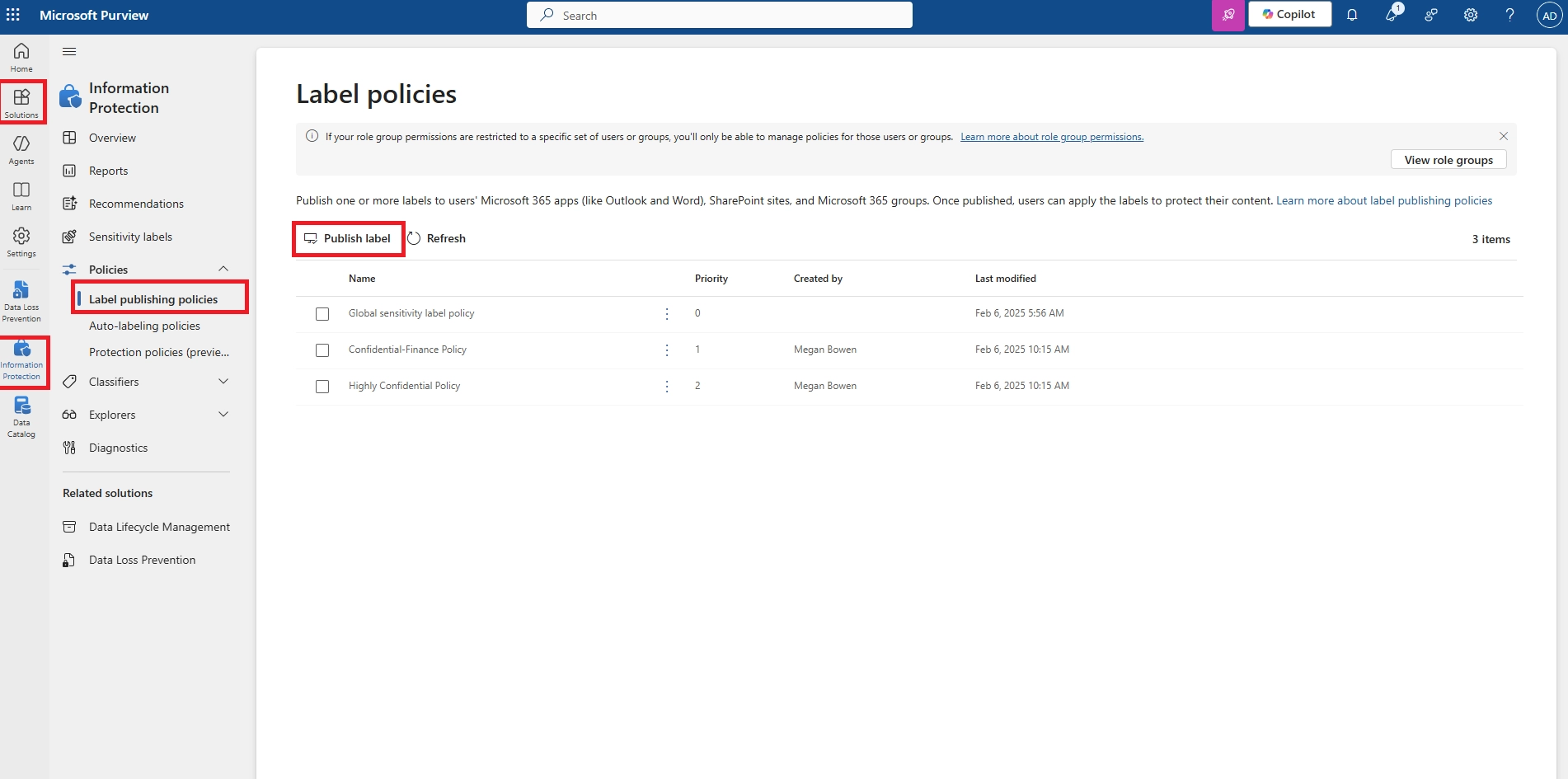
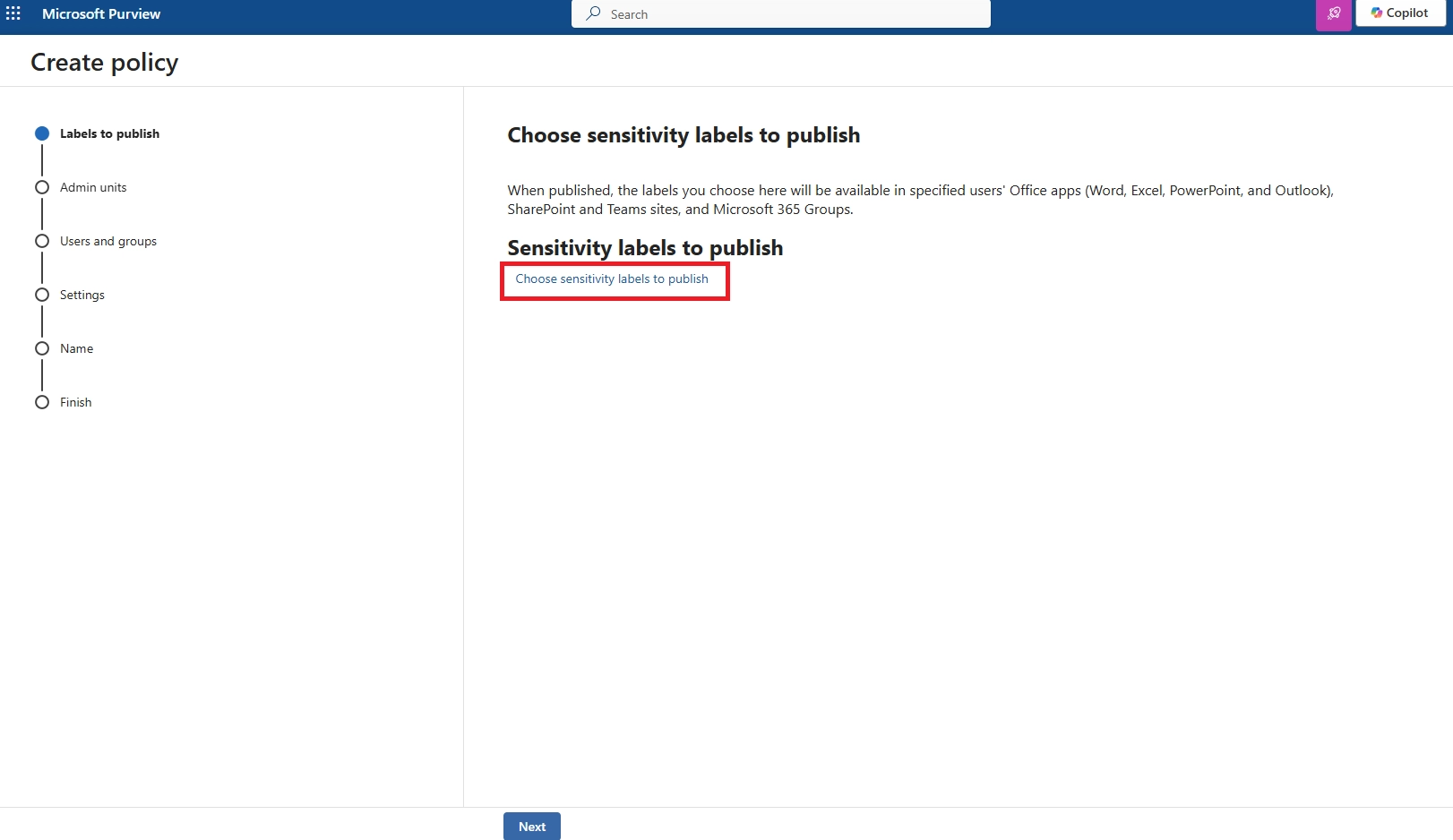
- Apply a Microsoft Purview sensitivity label with “view only” permissions
- Enforce session controls in Defender for Cloud Apps
- Configure Conditional Access to allow only browser access without download privileges
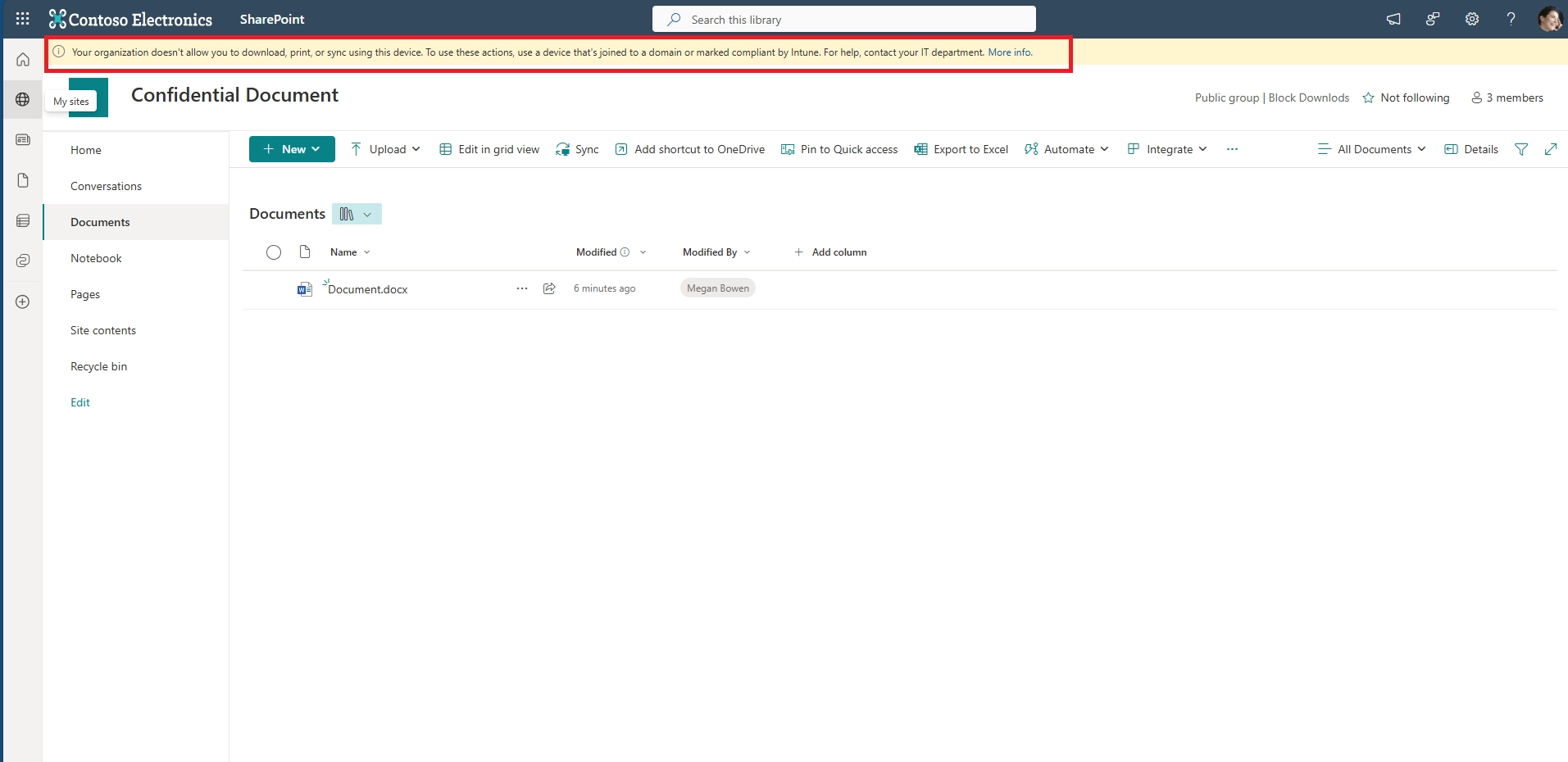
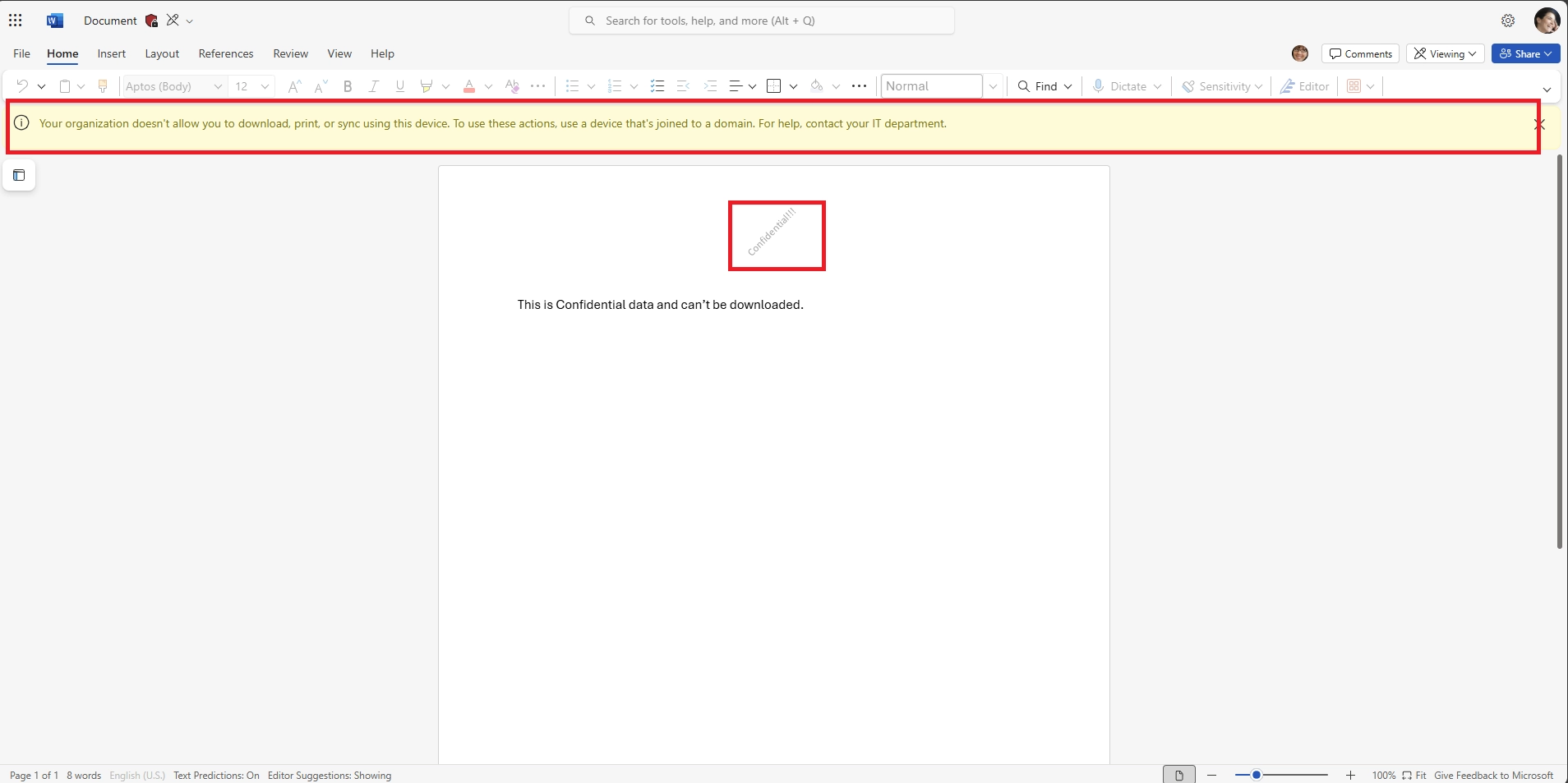
This ensures users can preview the file but cannot download, copy, or print it.
- How do I lock a file in Microsoft 365 to prevent changes or downloads?
You can “lock” a file by:
- Setting file permissions to read-only via SharePoint/OneDrive
- Applying a sensitivity label with restricted permissions
- Using IRM (Information Rights Management) in Purview to disable copy, print, and download
This ensures the file cannot be altered or downloaded, even by collaborators.
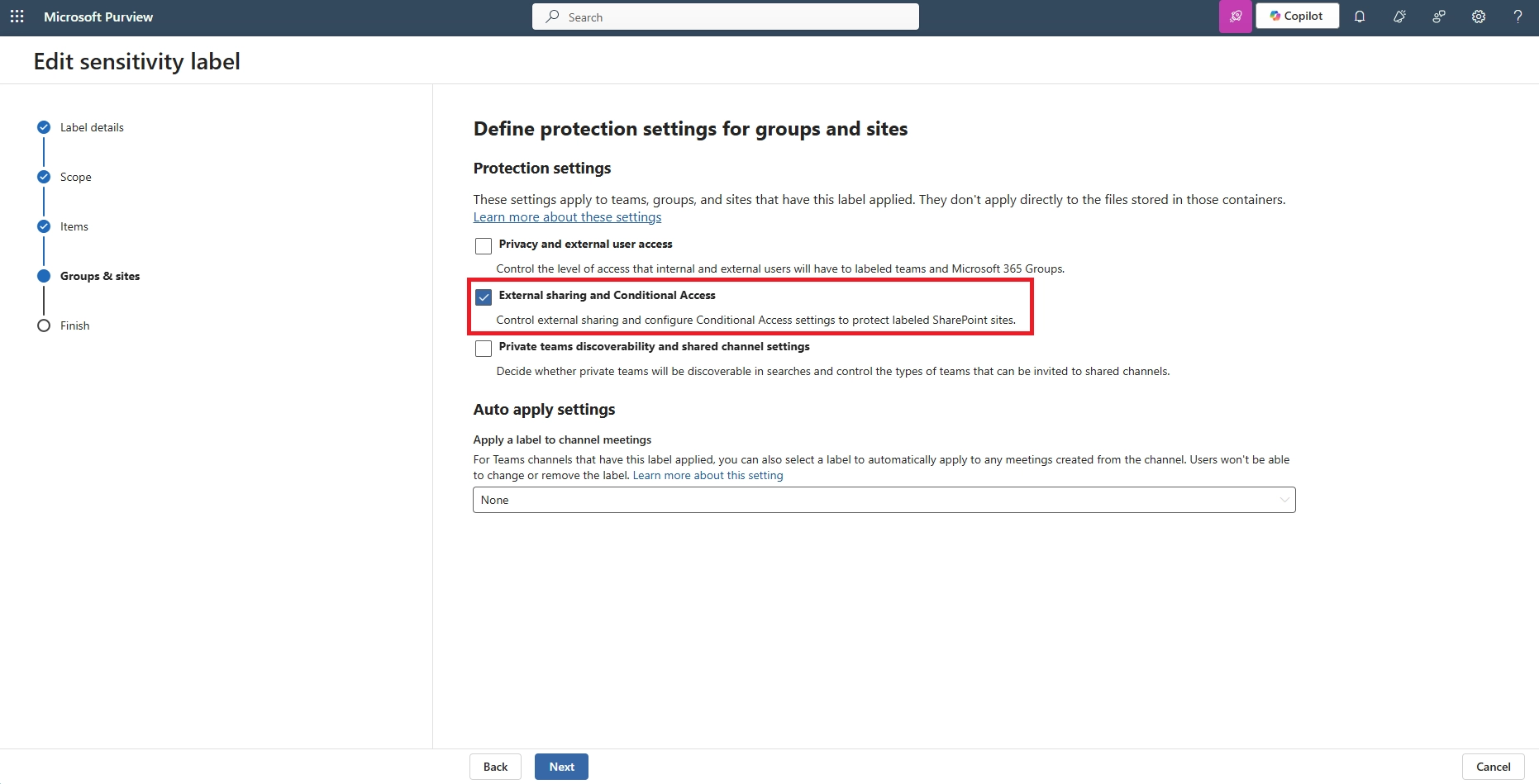
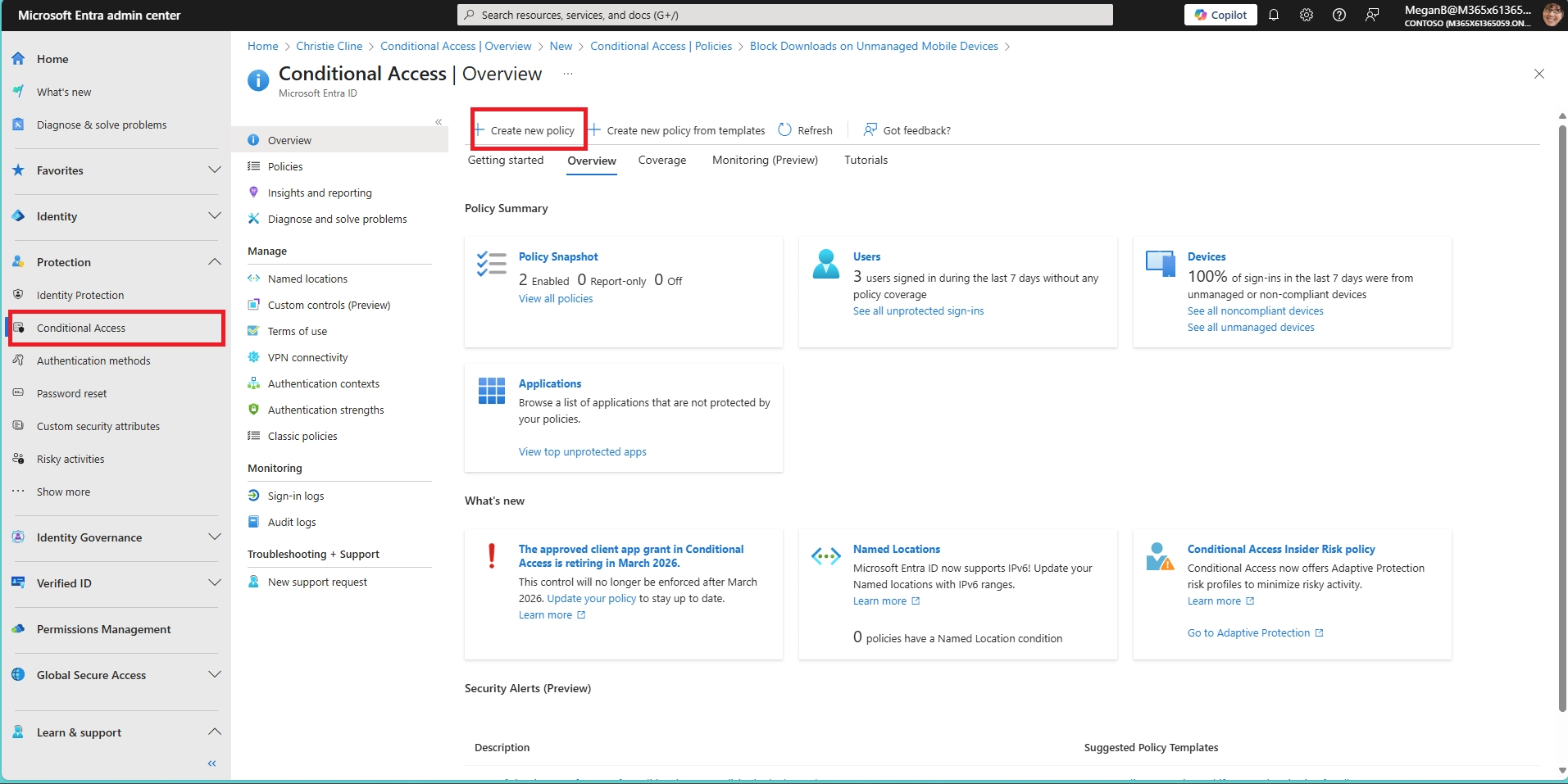
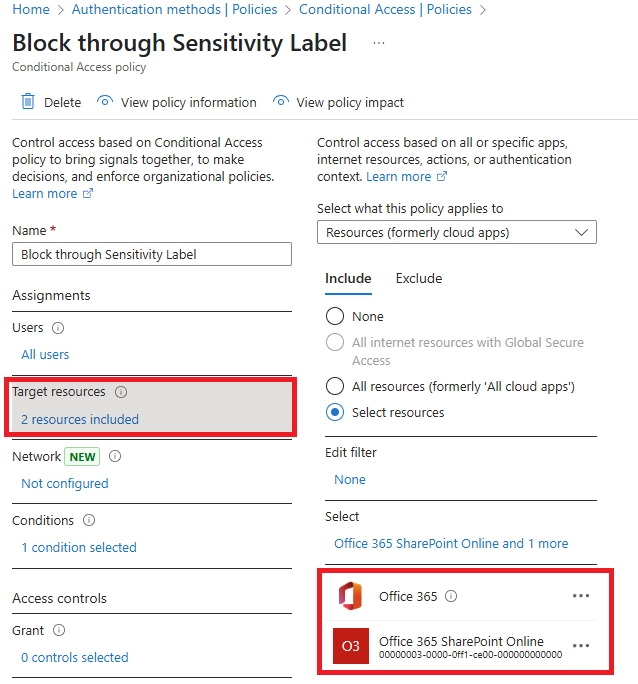
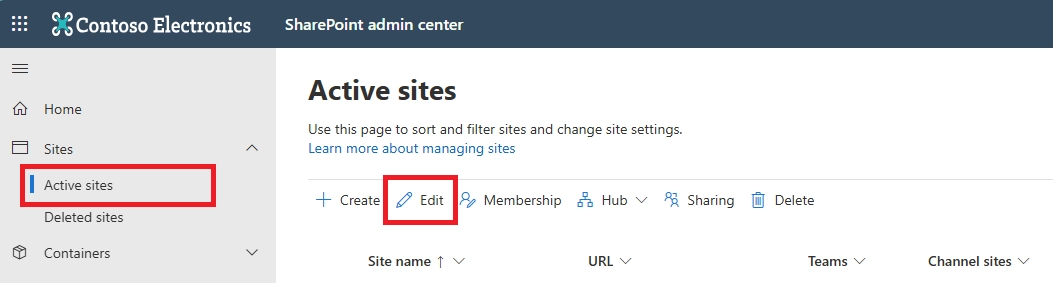
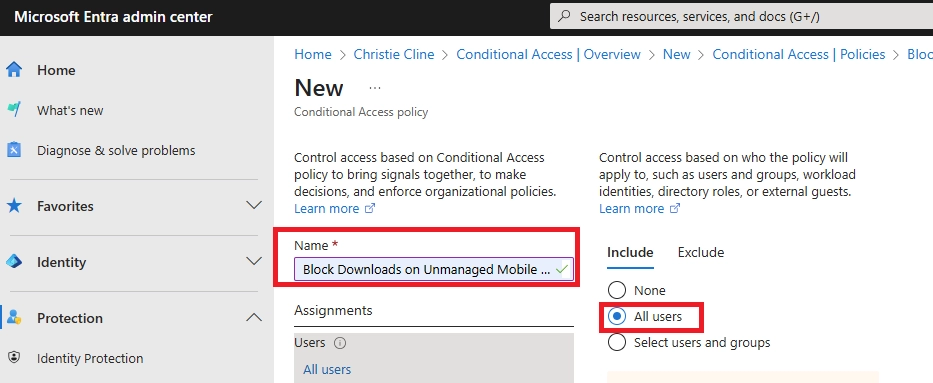
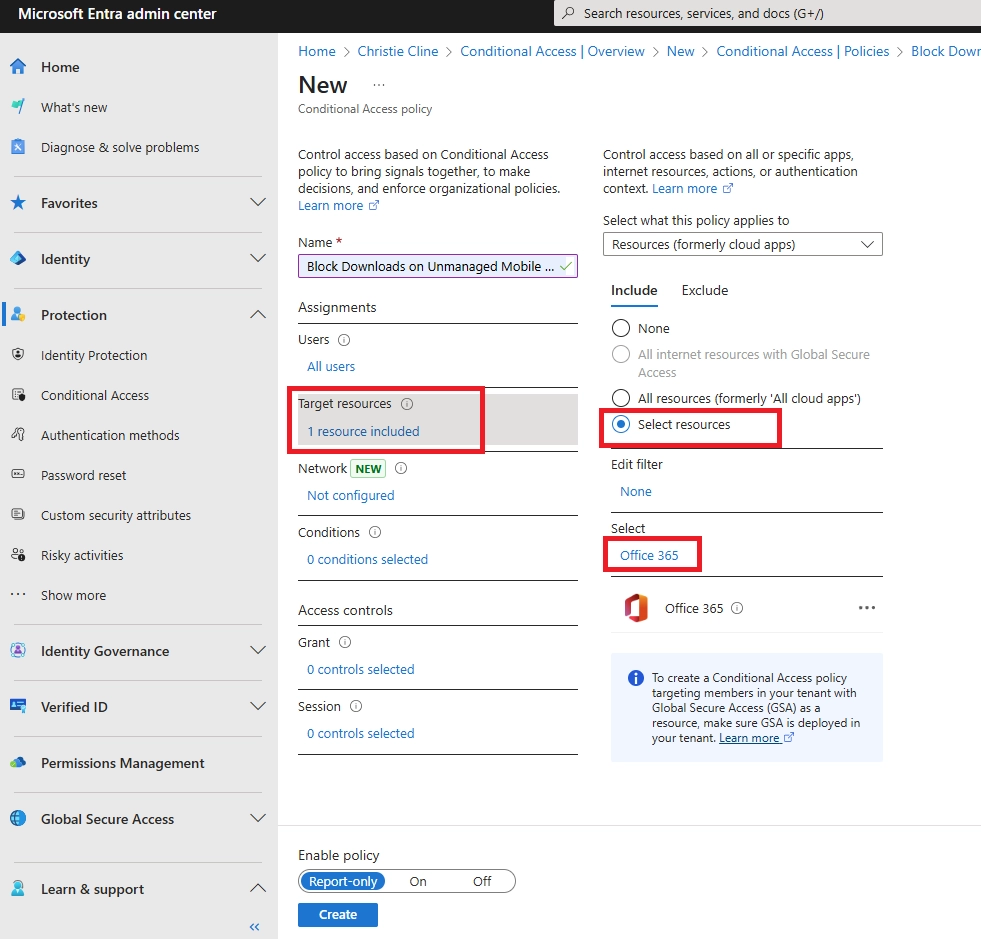
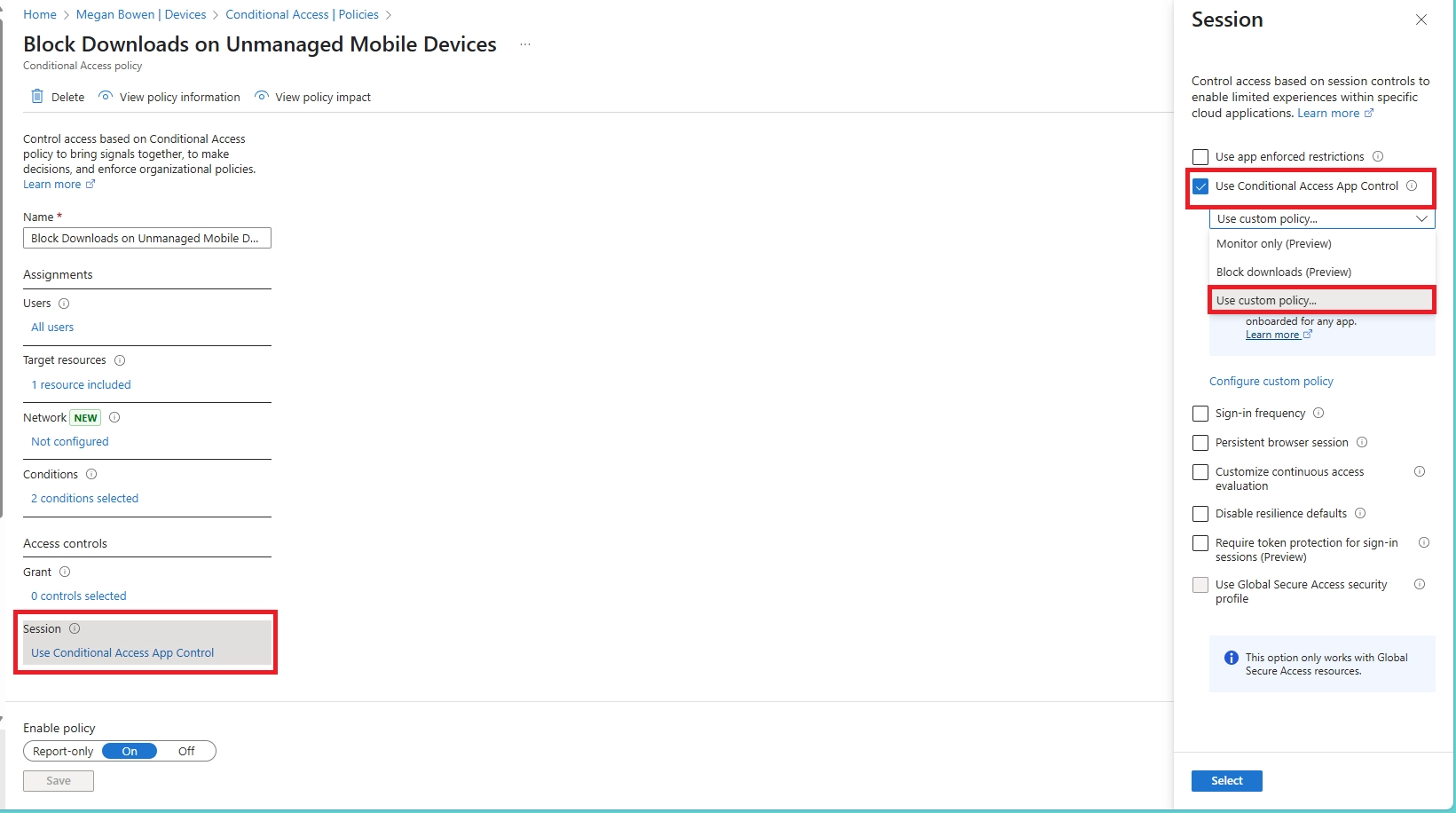
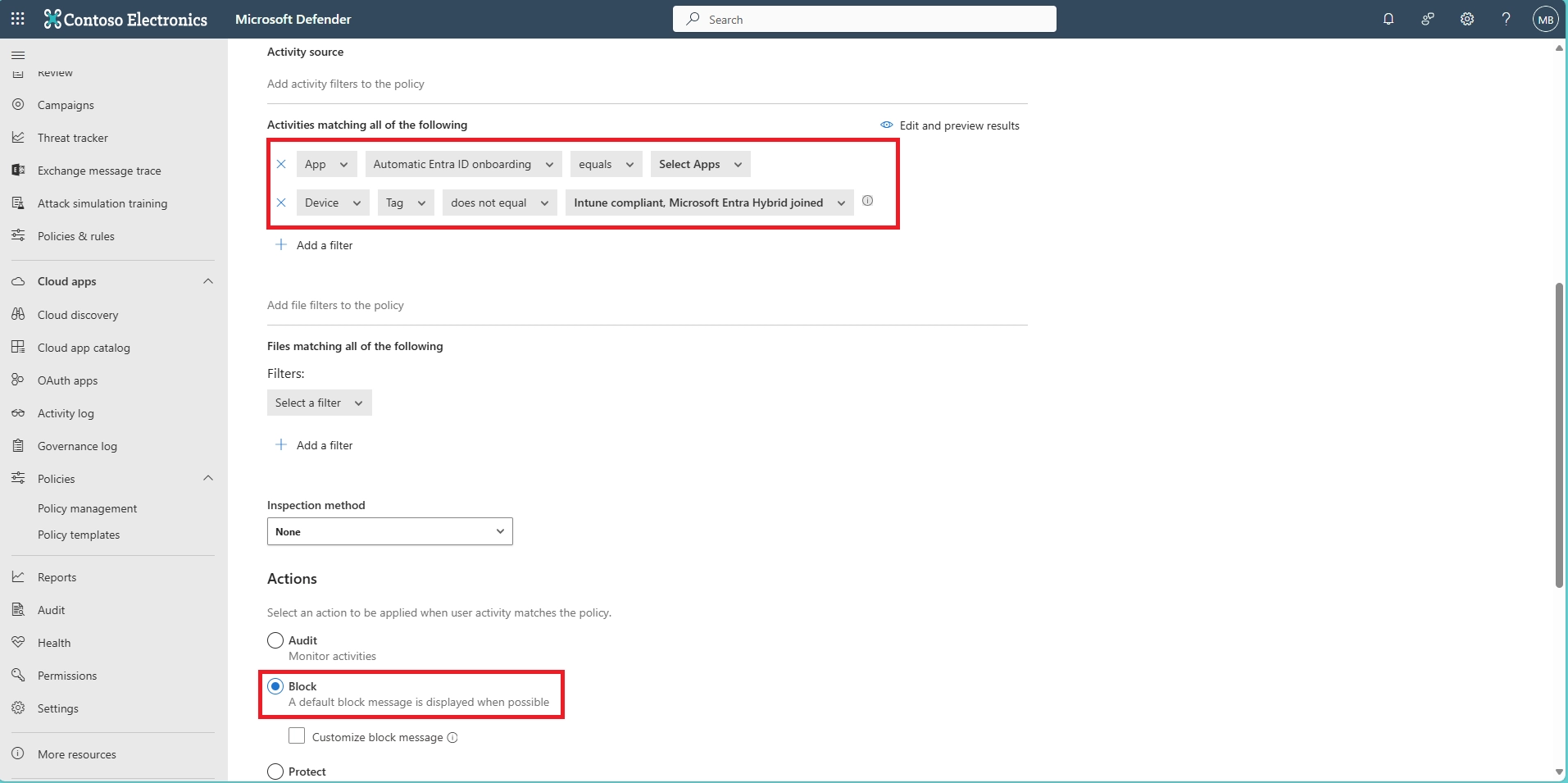
- Can I block downloads in SharePoint Online using Conditional Access?
Yes. In Conditional Access:
- Set SharePoint Online as the cloud app
- Add a condition for unmanaged or mobile devices
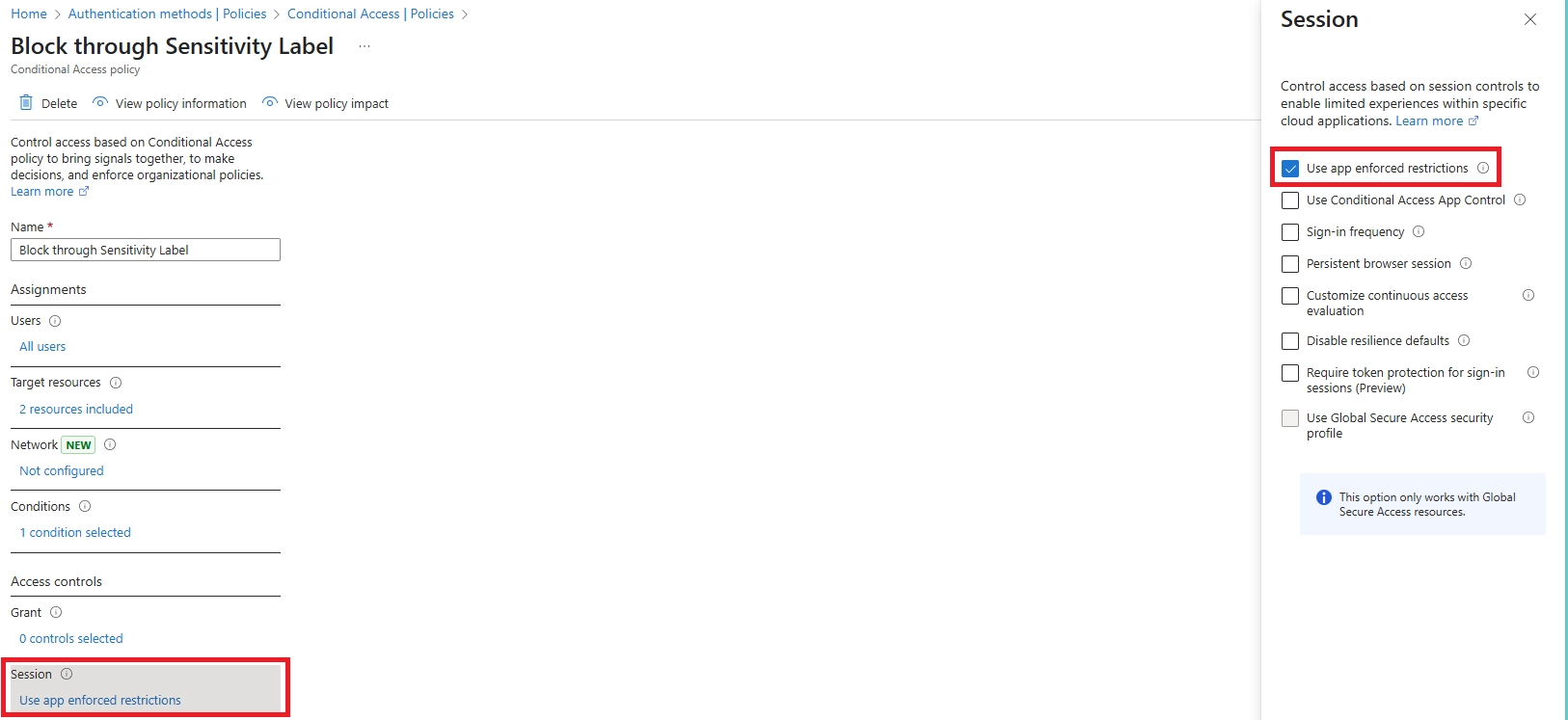
- Use the “Use Conditional Access App Control” option to enable Defender for Cloud Apps session control
Then, configure session control to block downloads, optionally with watermarking.
- How do I stop users from downloading files from my shared folder in OneDrive?
When sharing a folder in OneDrive:
- Click “Manage Access” → “People with existing access”
- Choose ‘View only’ and disable “Allow editing”
- For external or unmanaged access, use Conditional Access + Defender for Cloud Apps to block download behavior on browser and mobile
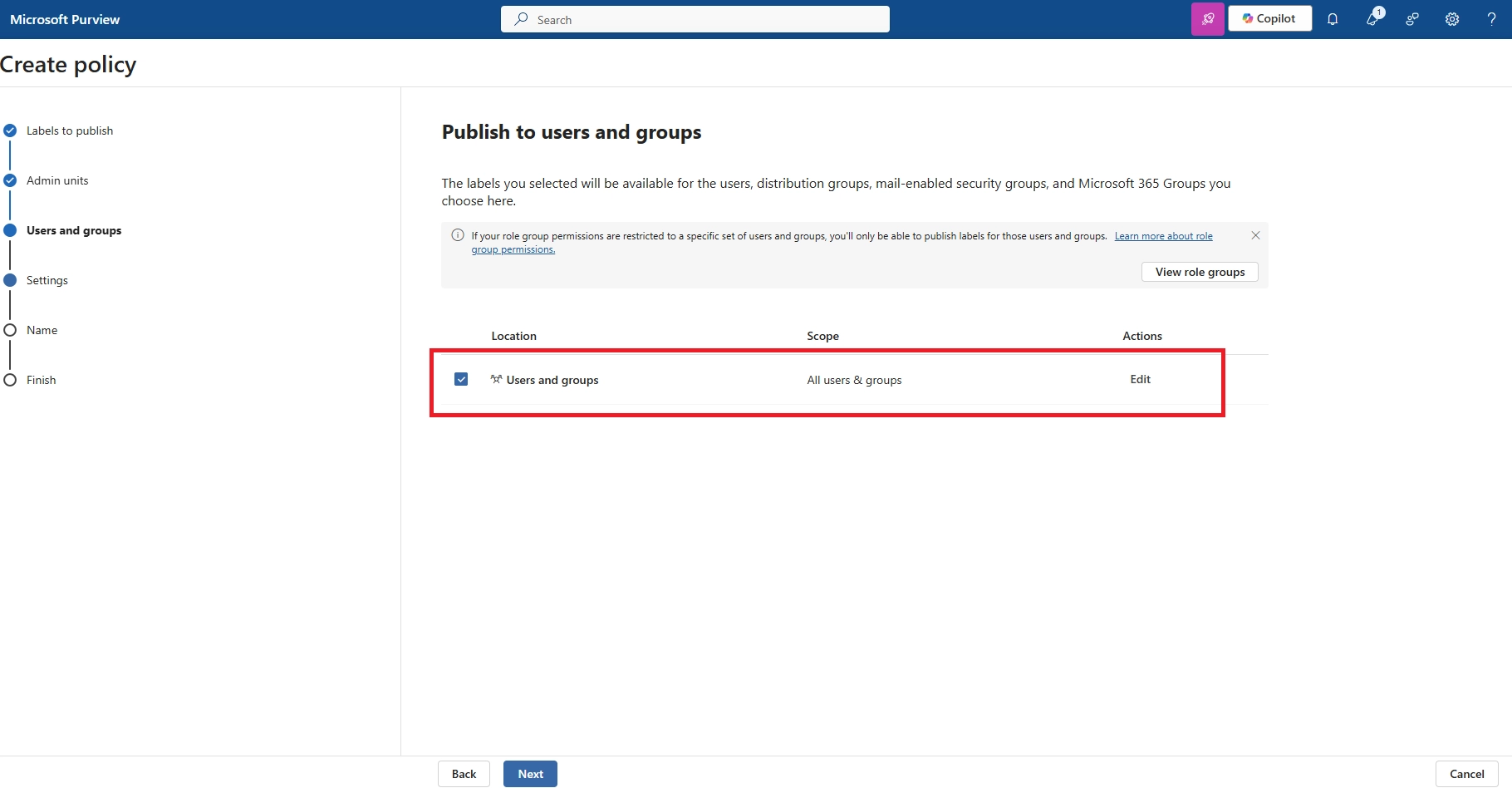
- How do I prevent saving files to OneDrive for specific users?
You can restrict OneDrive access by:
- Blocking license assignment for OneDrive
- Using Intune App Protection Policies to prevent OneDrive use on unmanaged devices
- Applying Conditional Access to block access to OneDrive altogether for certain users or device types
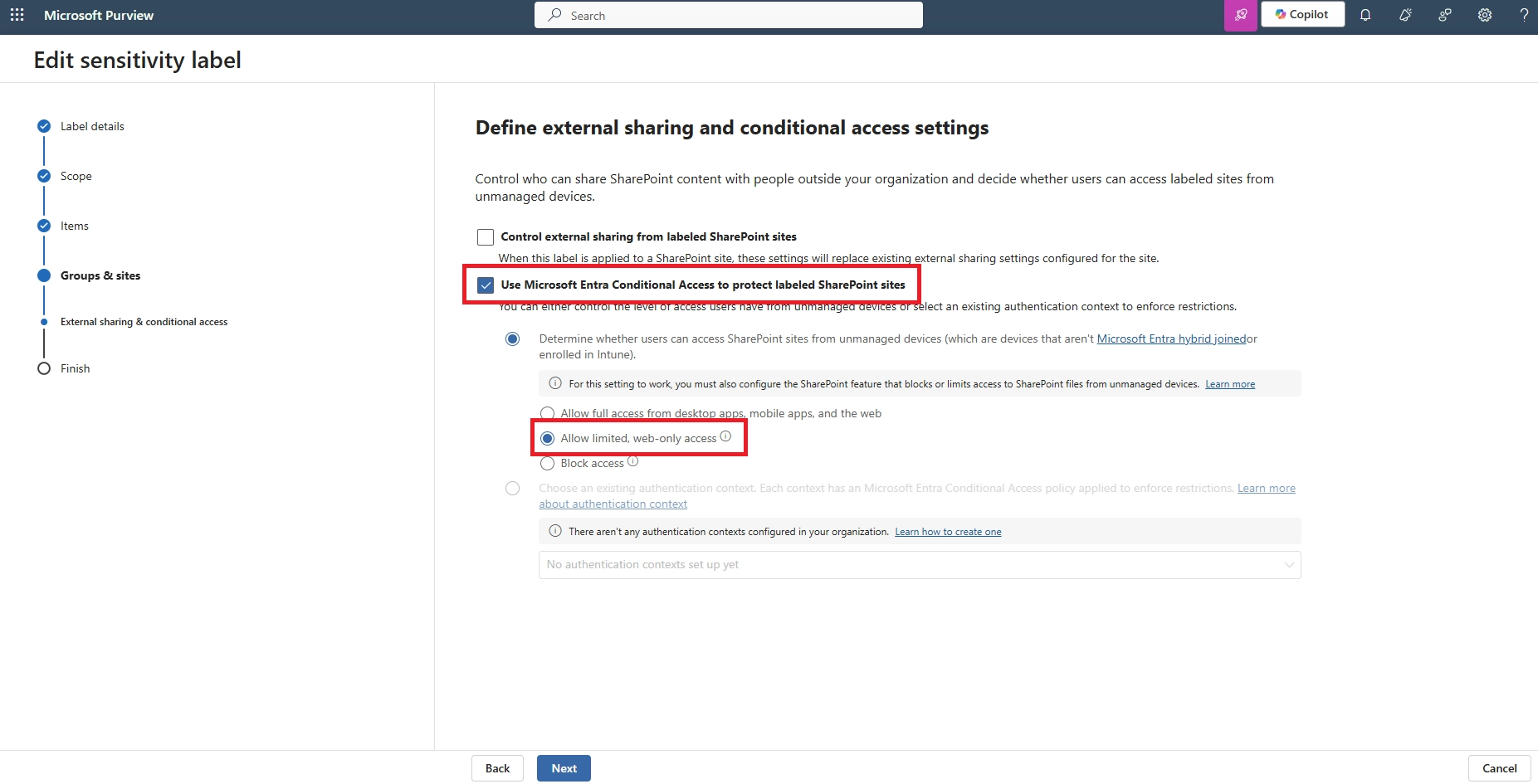
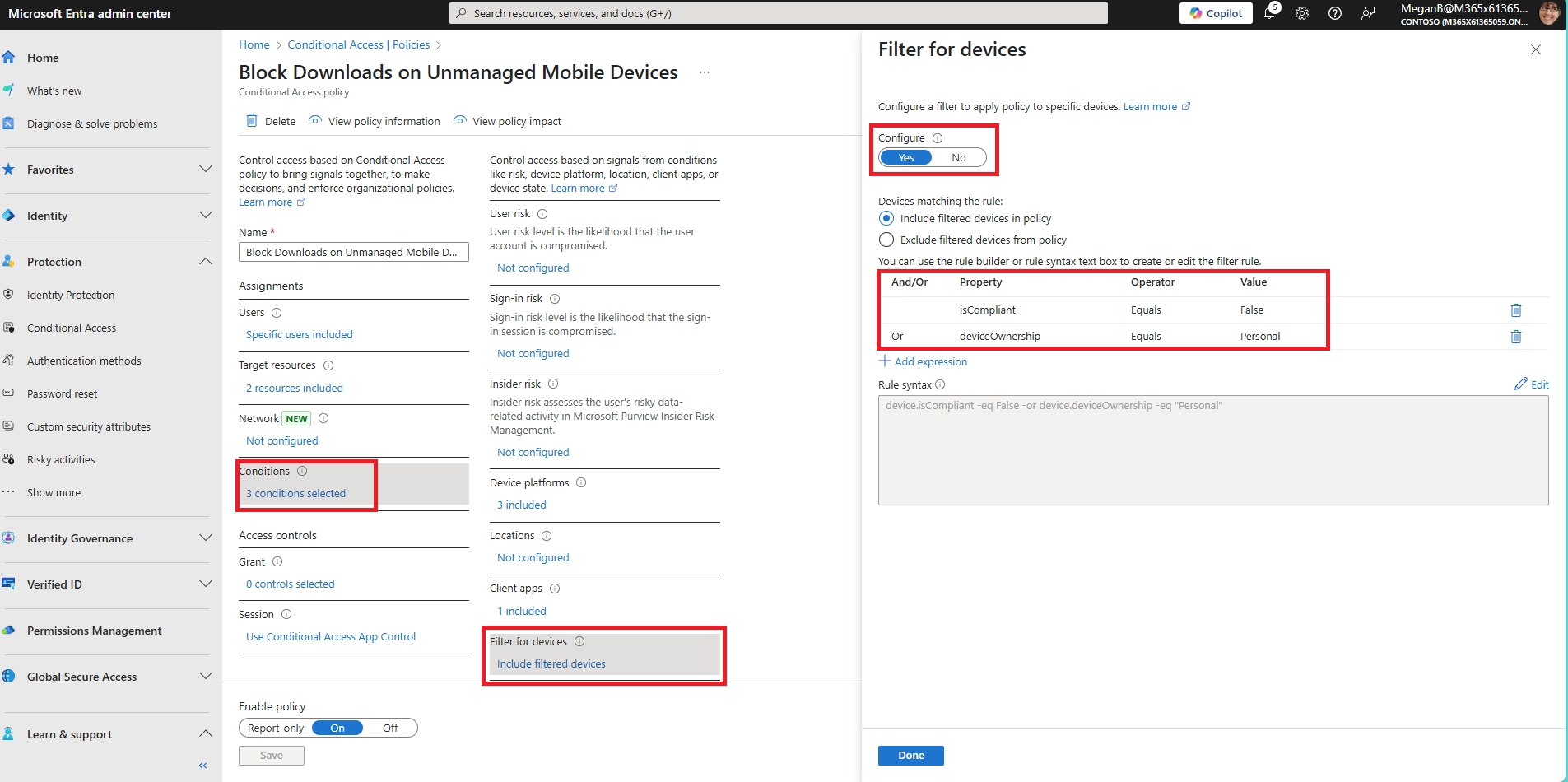
- Can I allow downloads only from managed or compliant mobile devices?
Yes. Conditional Access policies let you require that a device be marked as compliant (via Intune) before allowing downloads. This ensures sensitive content is only downloaded onto secure, company-controlled devices.
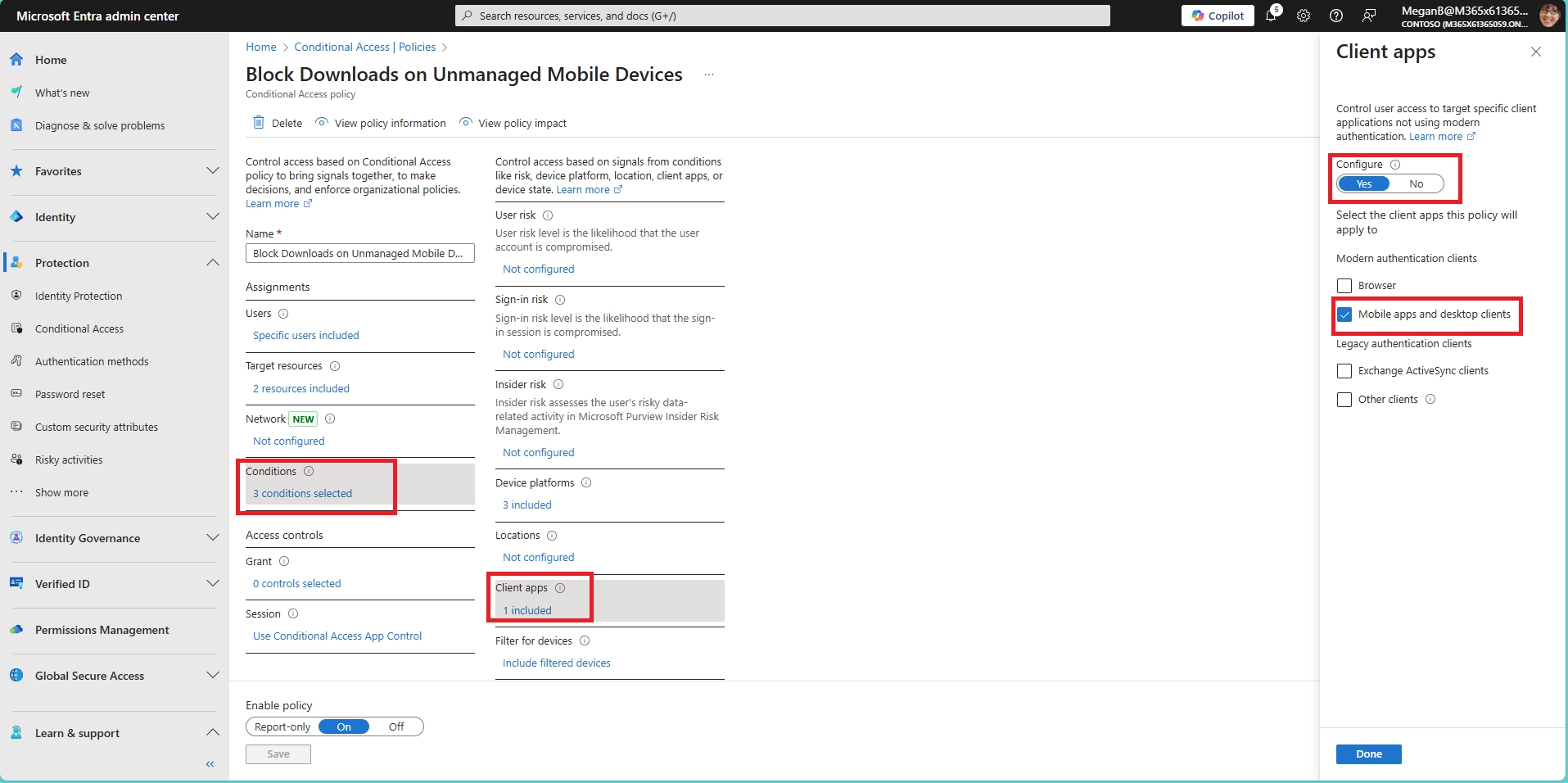
- Will download restrictions apply to desktop users too?
Only if you include desktops in your Conditional Access policy scope. You can target mobile platforms specifically (iOS, Android) while allowing full access on managed desktops or laptops.
- Can I prevent file downloads in Microsoft Teams?
Yes. You can block file downloads in Teams by combining:
- A Conditional Access policy for the Teams app
- Defender for Cloud Apps session control to allow view-only mode
This lets users preview shared documents without downloading them on mobile or unmanaged devices.
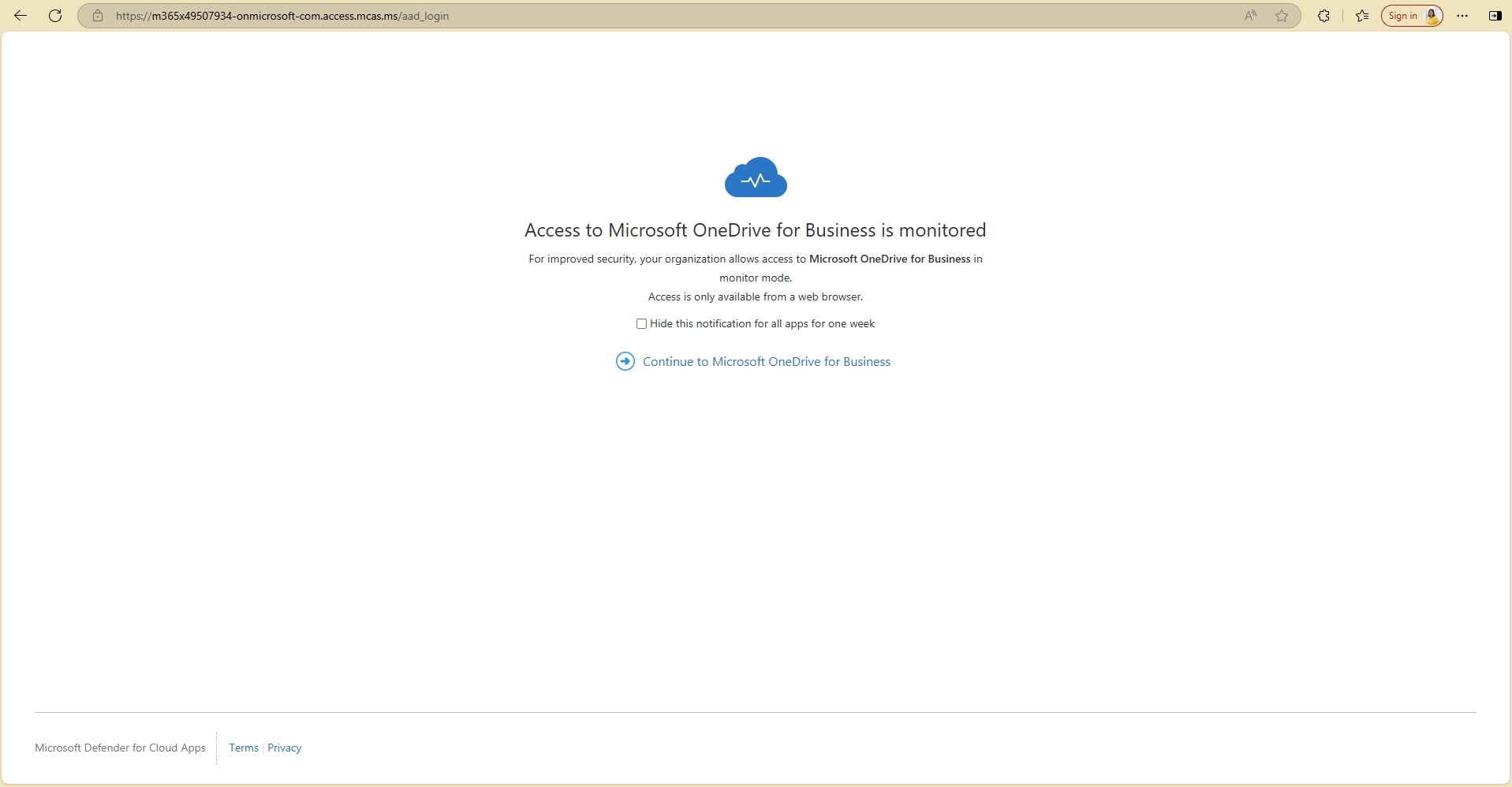
- How do I stop documents from automatically downloading when opened?
To prevent automatic downloads:
- Use Defender for Cloud Apps to enforce session controls
- Force documents to open in the browser view only
- Disable “Always open in desktop app” in SharePoint/OneDrive settings
This ensures files are streamed rather than downloaded by default.
- Can I block screenshots of files on mobile devices?
Partially. Intune App Protection Policies can block screenshots inside Microsoft apps like Word or OneDrive. However, browser-based access cannot prevent screenshots — so combine with watermarking and user awareness training.
- How can I audit or track file download attempts in Microsoft 365?
Use the following tools:
- Microsoft Defender for Cloud Apps for real-time alerts and activity logs
- Microsoft Purview Audit Logs to view file access, location, and download attempts
This helps you detect risky behavior and maintain compliance with internal policies.
- Can I make exceptions for certain users or departments?
Yes. You can define inclusion and exclusion groups in Conditional Access. For example, allow executives or HR users to download files from mobile, while restricting access for all other roles.