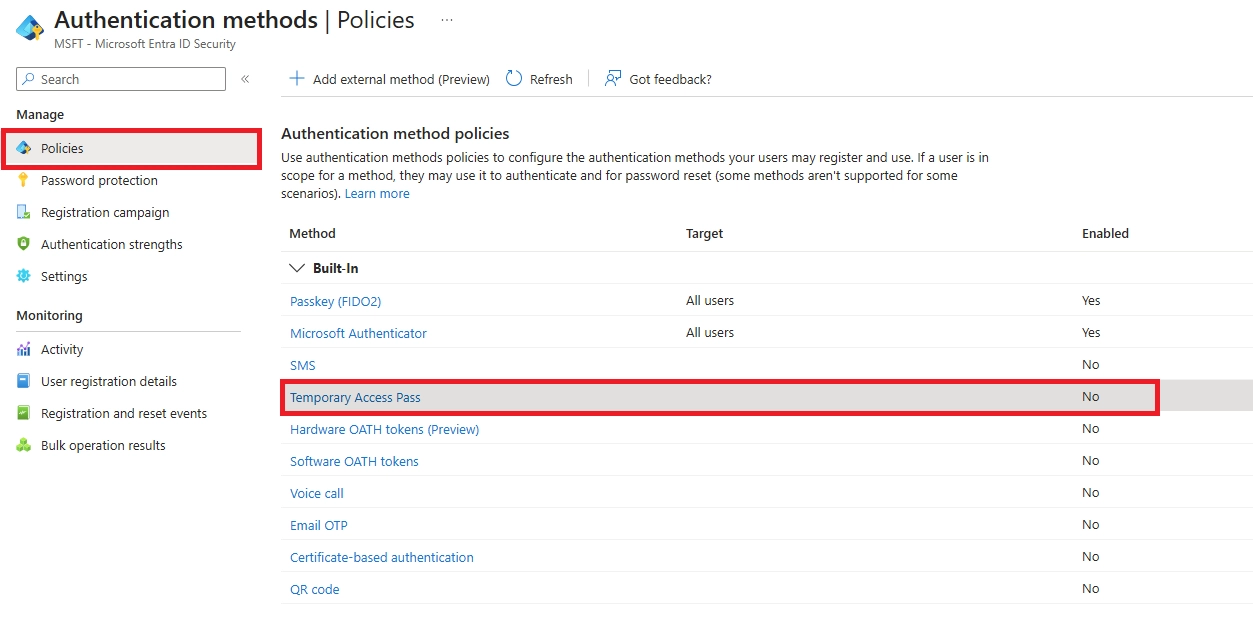
Q: Is passwordless more secure than MFA in Microsoft 365?
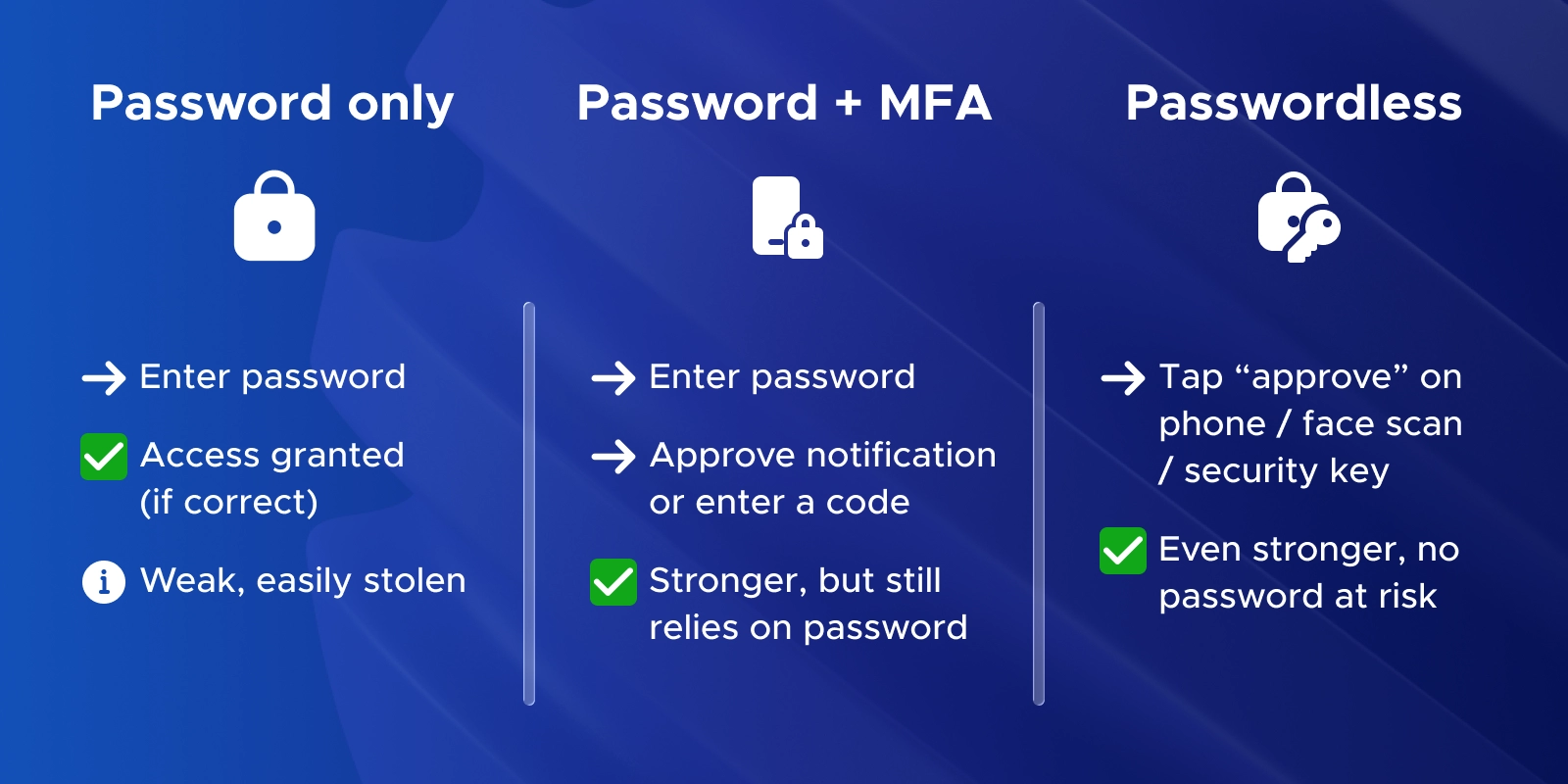
Yes. Passwordless removes passwords completely, so hackers can’t steal them. Devices and biometrics protect your account instead.
Q: Is Microsoft passwordless more secure?
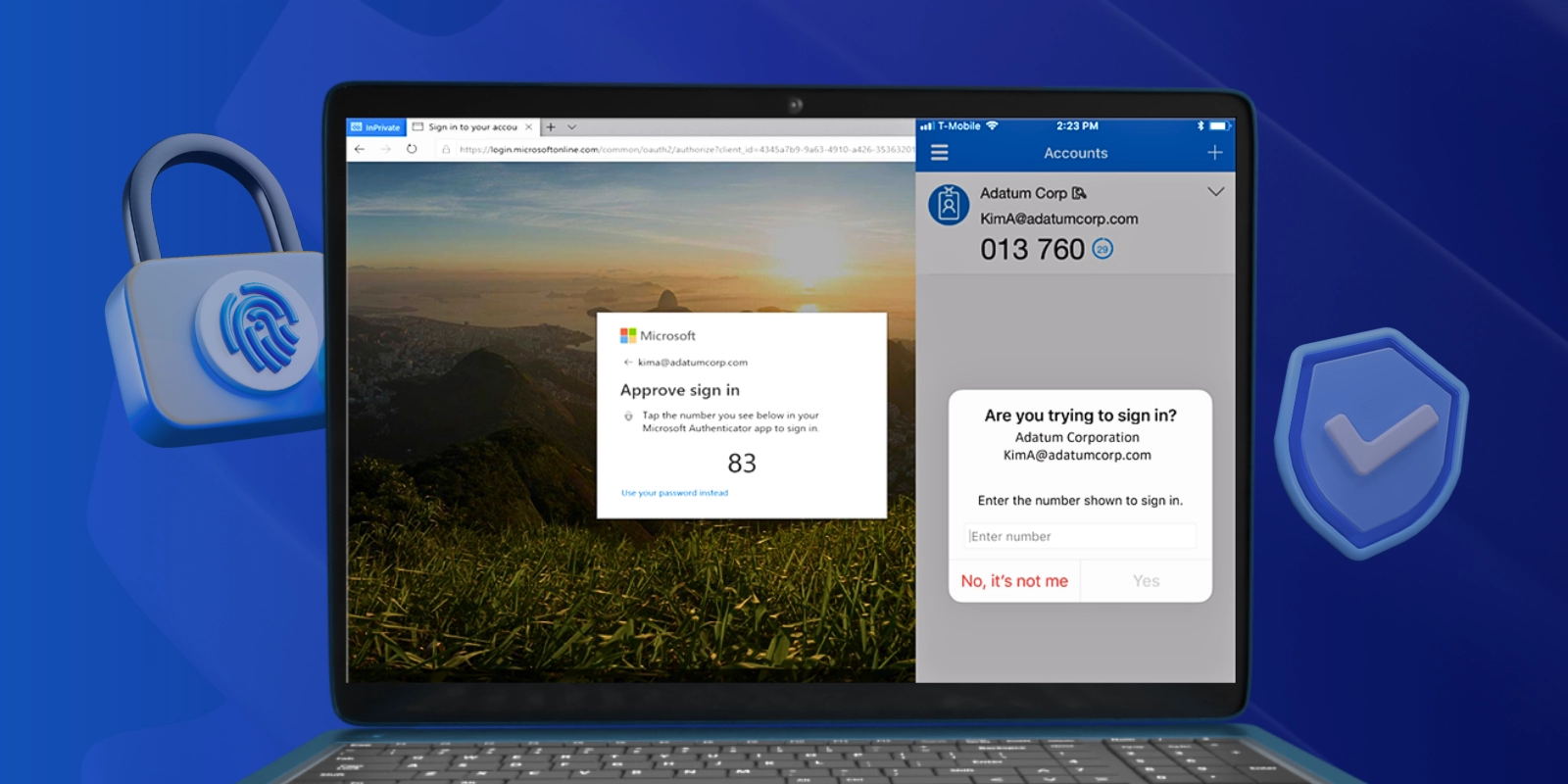
Yes. Microsoft passwordless methods like Authenticator app sign-in, Windows Hello, and FIDO2 keys are phishing-resistant and safer than password+MFA combos that rely on OTPs or SMS.
Q: Can you use MFA and passwordless together in Microsoft 365?
Absolutely. Passwordless itself is a type of MFA. You can run both: MFA for all users, and passwordless for extra security or high-risk accounts.
Q: What is “passwordless MFA” versus regular MFA?
Passwordless MFA meets MFA requirements without needing a password. Regular MFA uses a password plus an additional factor like a code or push notification.
Q: What is the advantage of passwordless authentication over password + MFA?
It’s faster and smoother. Users avoid typing passwords, reduce phishing risk, and login feels like one simple step.
Q: What are the disadvantages of passwordless authentication?
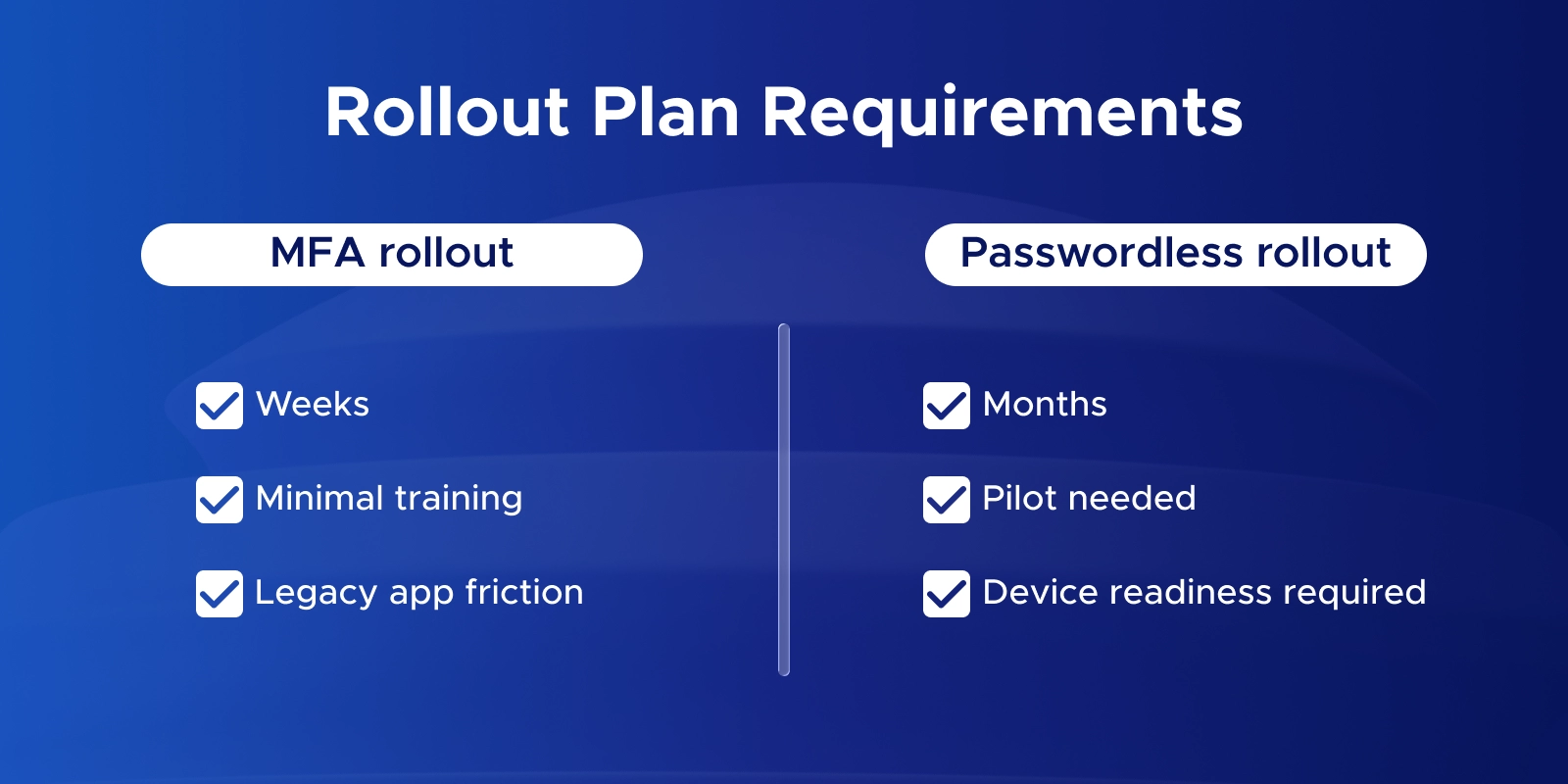
Setup can take time. Users need modern devices, and you must plan for lost devices with backup methods like temporary codes or recovery keys.
Q: What is the difference between passwordless MFA and phishing-resistant MFA?
Passwordless MFA removes passwords but still uses multiple factors. Phishing-resistant MFA emphasizes factors that can’t be stolen or intercepted, like FIDO2 keys or biometric data.
Q: How does passwordless MFA work?
You log in with your device (phone, security key, or PC) and a biometric or PIN. Behind the scenes, it still counts as MFA, but it feels like one step.
Q: What does FIDO2 stand for?
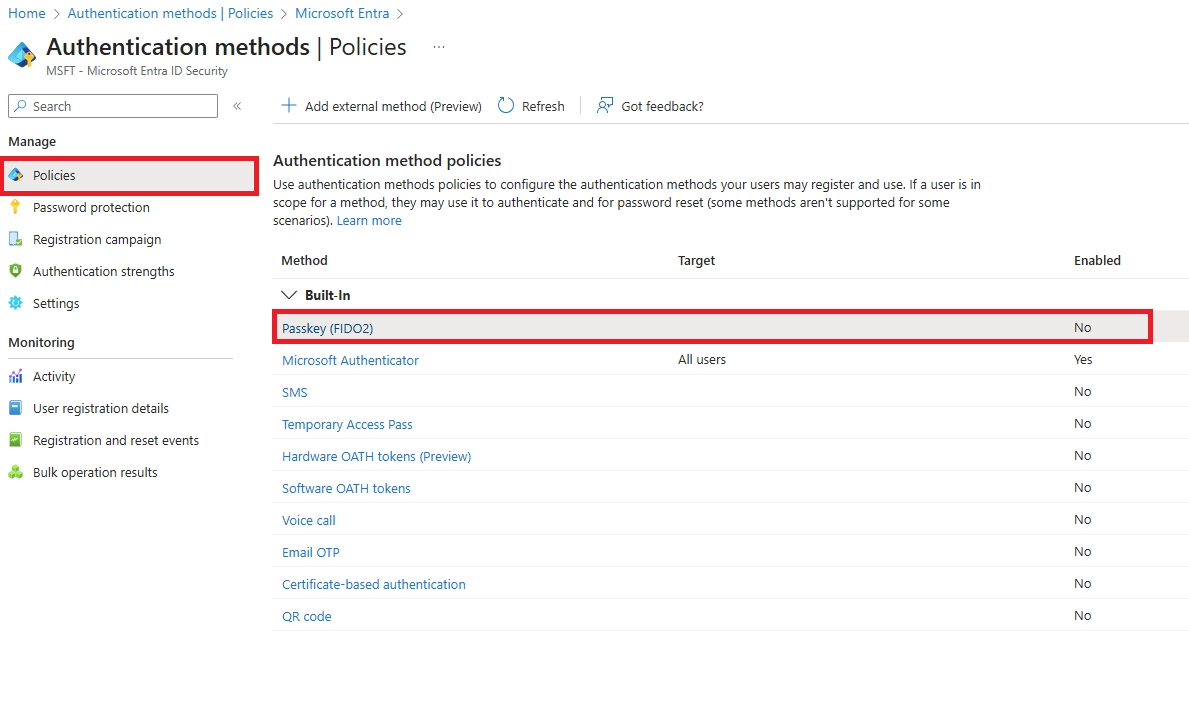
Fast IDentity Online 2. It’s a global standard for passwordless login using cryptography and devices like security keys or built-in fingerprint scanners.
Q: Does one password have MFA?
No. One password is single-factor. MFA requires at least two factors, like password + device, or device + biometric.
Q: What is the main benefit of passwordless authentication?
It’s secure and easy. No passwords to forget, phishing attacks blocked, and users log in faster.
Q: What is a phishing-resistant MFA?
An MFA method that can’t be tricked or intercepted, like FIDO2 keys, Windows Hello biometrics, or Authenticator push notifications.
Q: What is the difference between MFA and phishing?
MFA is a security method with multiple verification steps. Phishing is an attack trying to steal credentials. MFA can block phishing attacks.
Q: What is the most secure type of MFA?
Passwordless methods using FIDO2 keys or biometrics are currently the strongest, because there’s no password to steal or intercept.
Q: When should you choose passwordless over MFA in Microsoft 365?
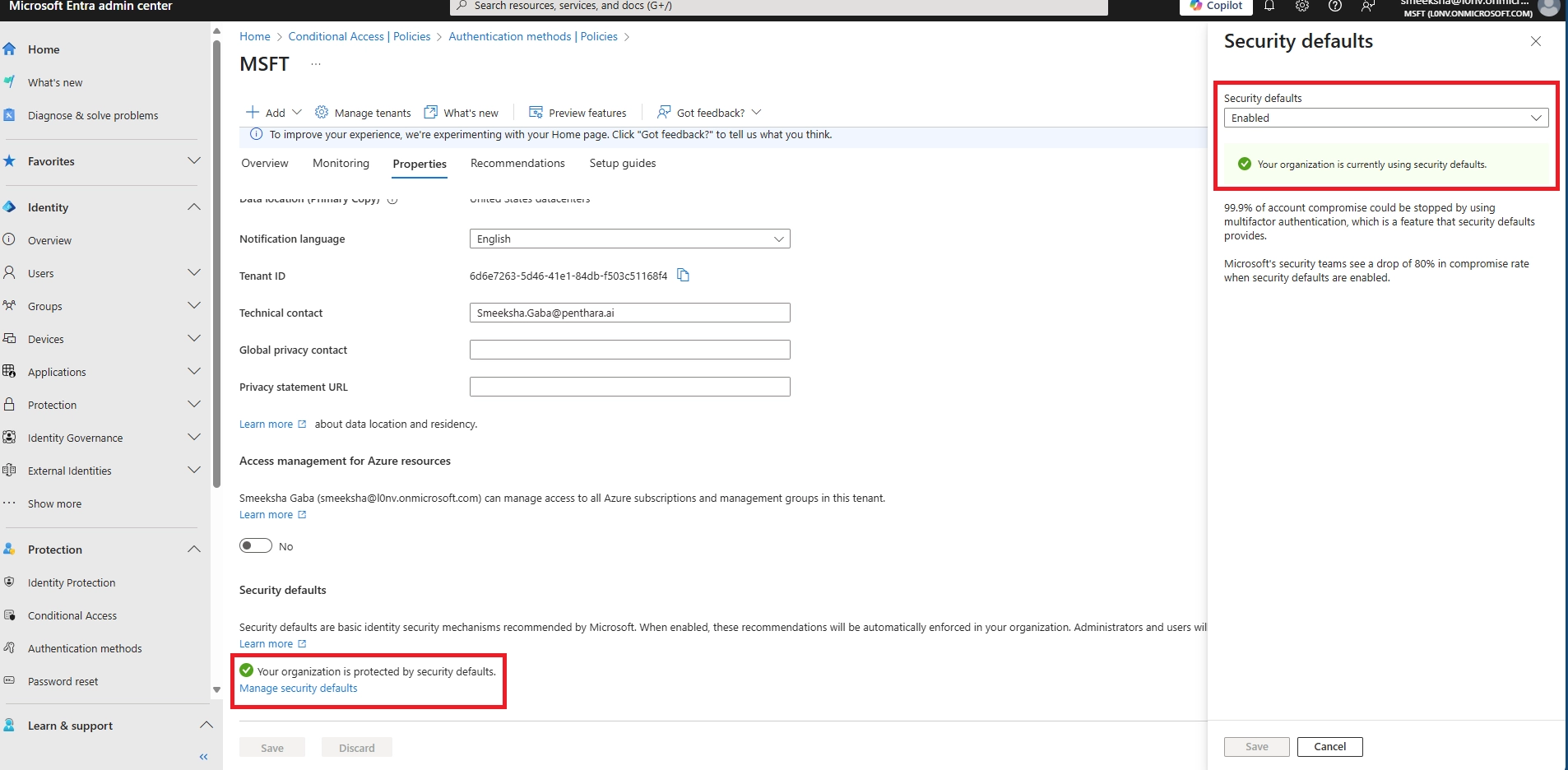
Use MFA immediately for all users. Consider passwordless when devices are modern, phishing is a concern, or high-value accounts need extra protection. Start with a pilot and expand gradually.
Q: Do I still need MFA if I go passwordless?
Yes. Passwordless is a form of MFA. You’re still verifying multiple factors-just without typing a password.
Q: Are passwords going away completely?
Eventually, yes. Microsoft and security experts envision a password-free future, but during transition, some accounts may still require passwords as backup.