Q1: How to enforce app-based push MFA for all users in Microsoft 365?
A: Use Security Defaults for a quick setup (forces all users to register with Authenticator in 14 days) or Conditional Access for granular control. Limit allowed methods to app notifications to enforce push MFA.
Q2: What is app-based push MFA and how do I enable it?
A: It sends a login approval request to the user’s Authenticator app instead of SMS or codes. Enable MFA via Security Defaults or Conditional Access, then guide users to select “Receive notifications for verification” during setup.
Q3: Can I require Authenticator push as the only MFA method?
A: Yes. Use Entra ID Authentication Methods Policy to disable SMS/voice, leaving only Authenticator app options. Combine with Conditional Access to enforce push for all logins.
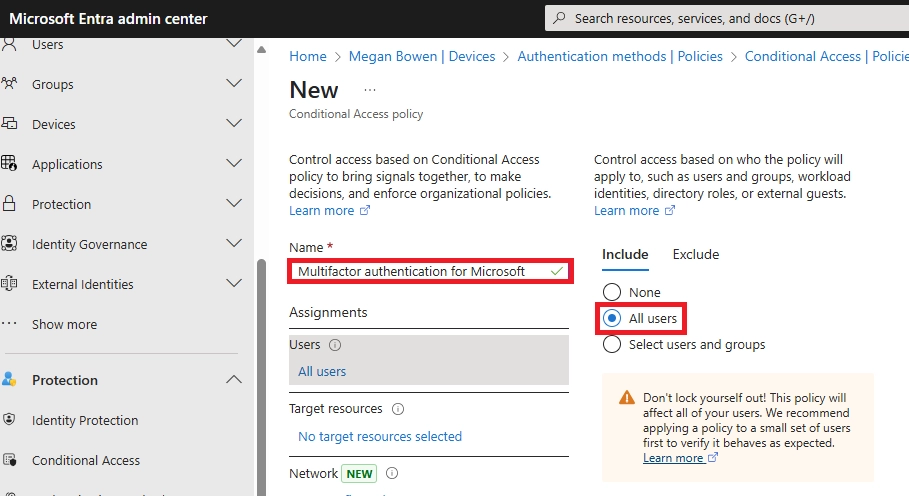
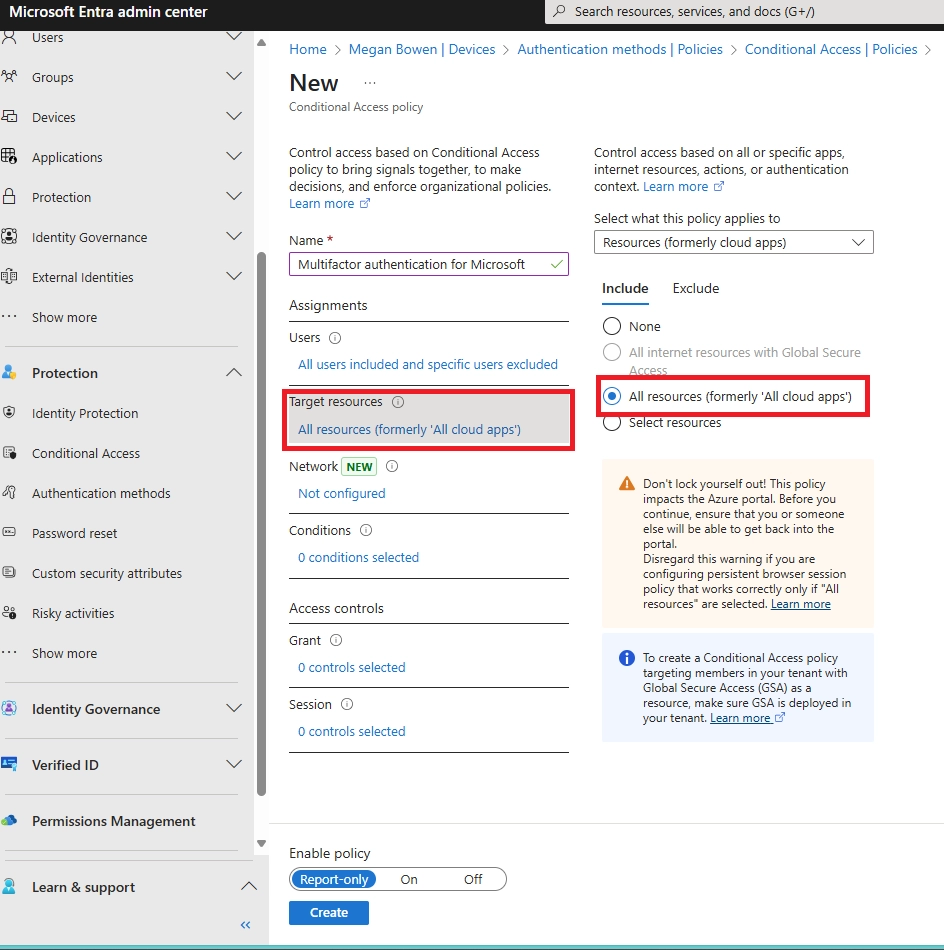
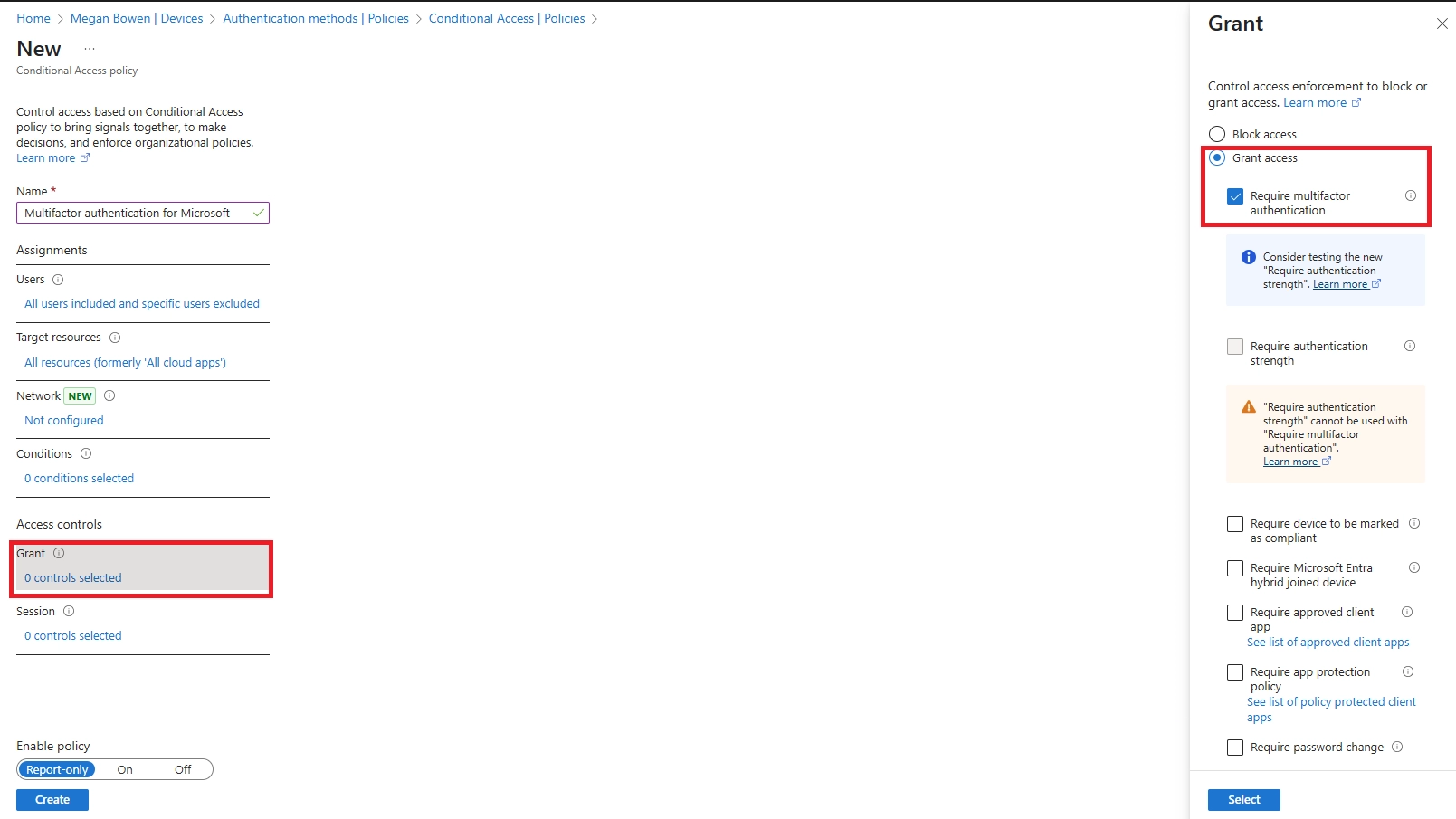
Q4: How do I enforce MFA via app push using Conditional Access?
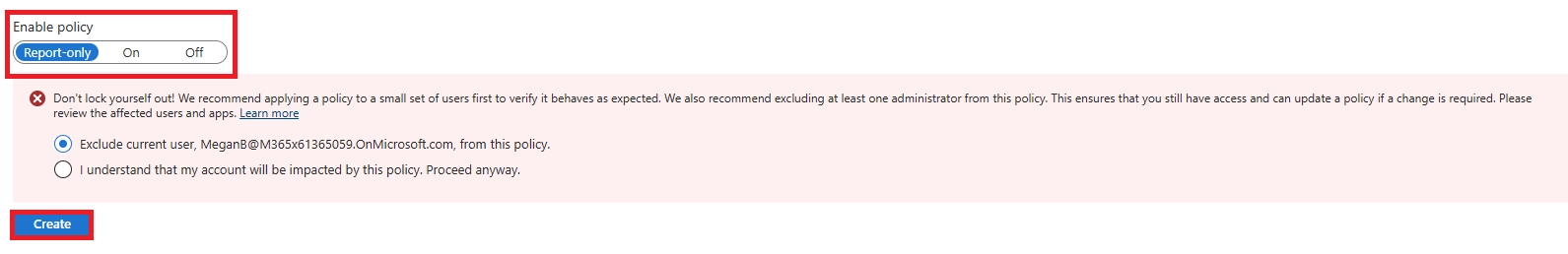
A: Create a Conditional Access policy targeting all users and apps, choose Require MFA, and limit allowed methods to Authenticator app push. Test first in report-only mode, then enable fully.
Q5: Which licensing is needed for app-based push MFA?
A: Basic MFA works with any plan. For Conditional Access, Entra ID Premium P1 is required; for registration campaigns or risk-based policies, Premium P2 is needed.
Q6: How to launch an MFA registration campaign for app push?
A: In Entra ID portal: Identity Protection > MFA Registration Campaign, target all users, and specify Microsoft Authenticator. Users get reminders until registration is complete.
Q7: Users aren’t receiving Authenticator push notifications – what now?
A: Check app installation, notifications enabled, and internet connectivity. Confirm device isn’t restricted (e.g., China). Re-register MFA if needed. Ensure Conditional Access or network rules aren’t blocking notifications.
Q8: Users get too many MFA prompts (fatigue) – any tips?
A: Enable remembered devices, use Conditional Access to only prompt for risky sign-ins, turn on Number Matching to prevent blind approvals, and educate users on expected MFA behavior.
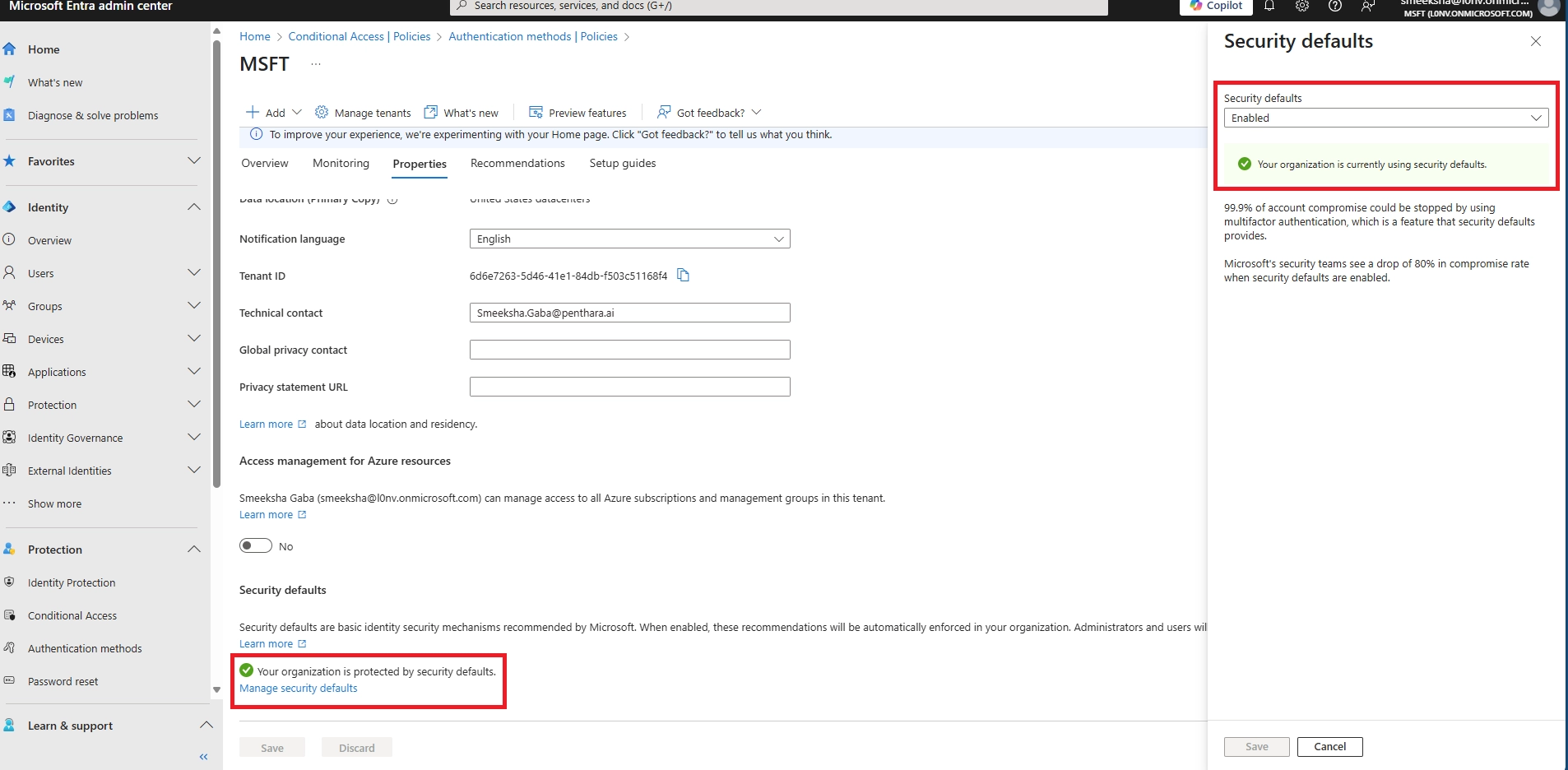
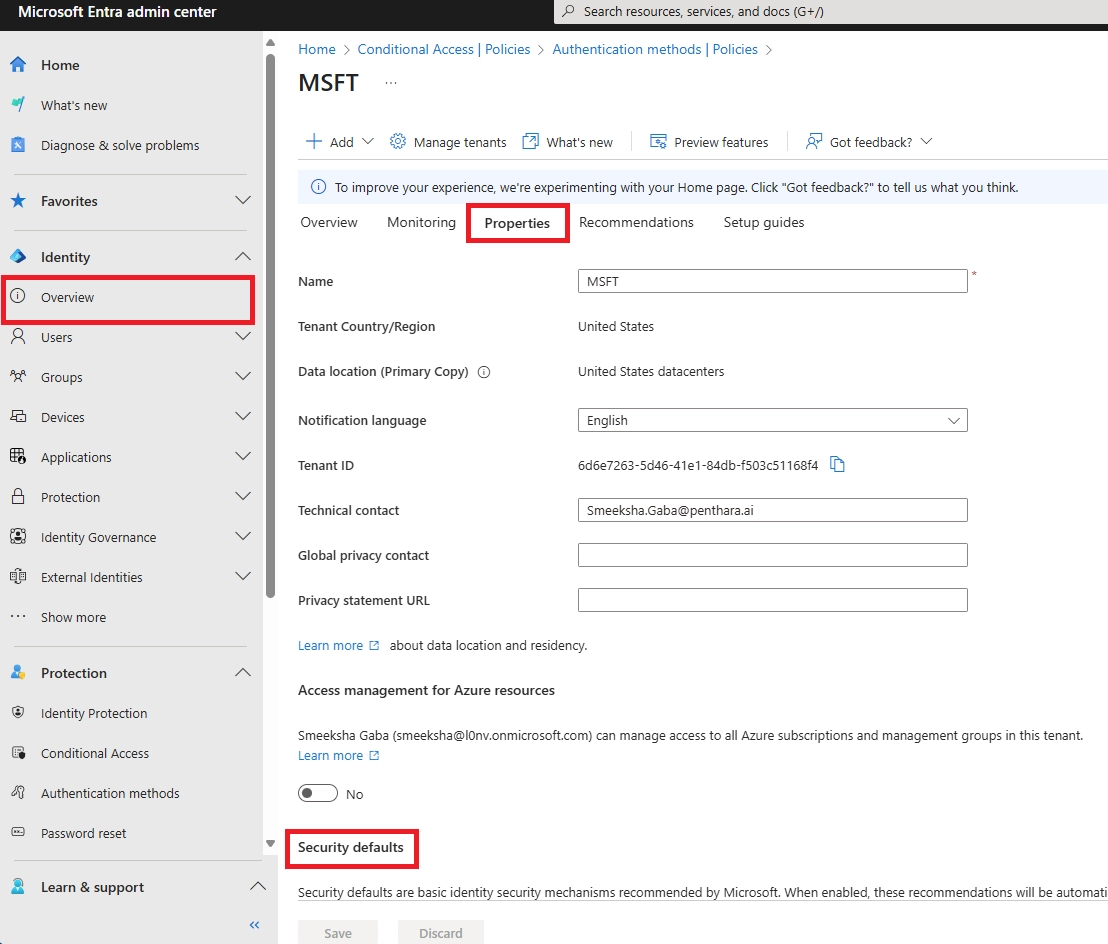
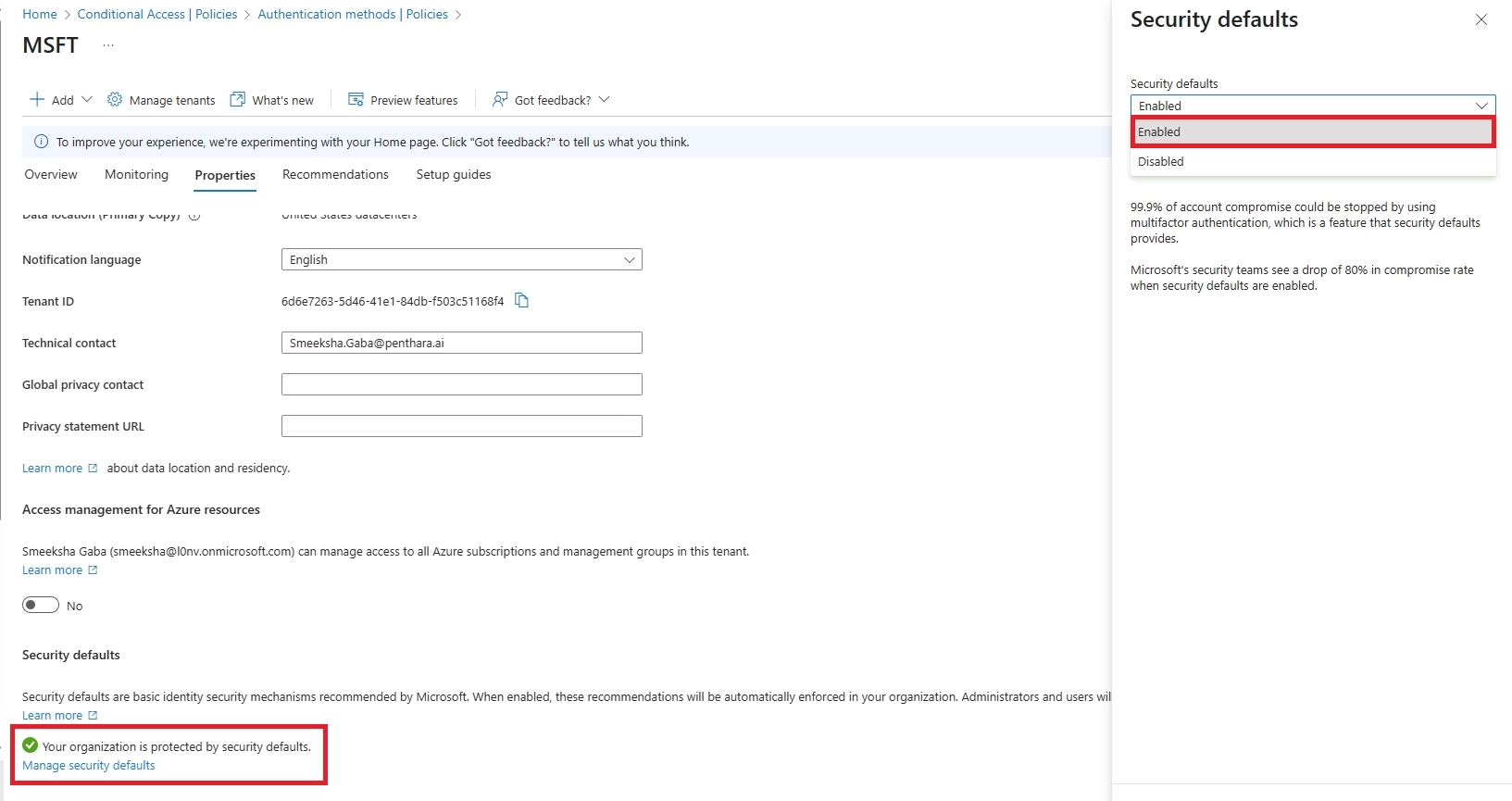
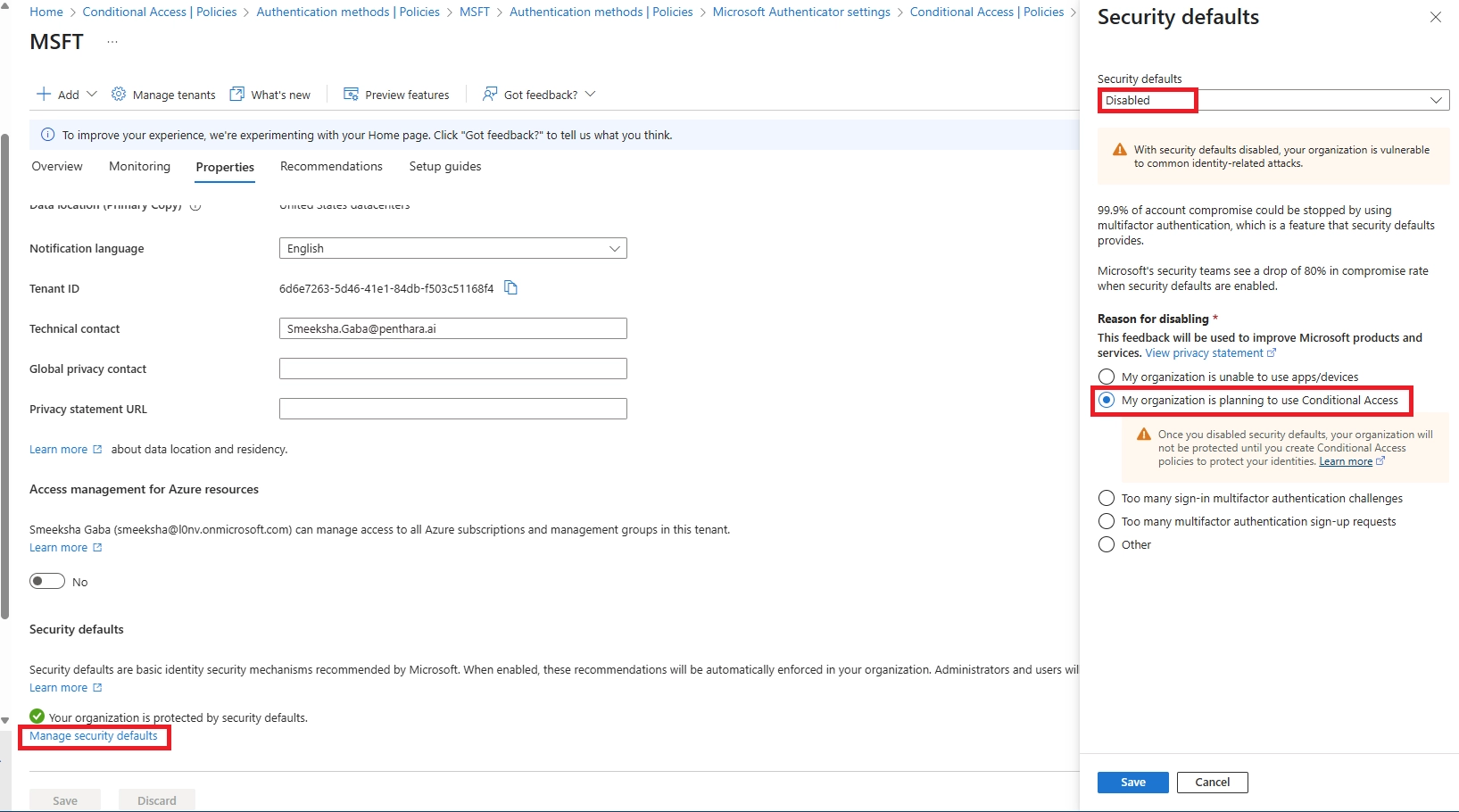
Q9: Can certain users be excluded?
A: Security Defaults: no exclusions. Conditional Access: yes, for break-glass or service accounts only. Never exclude normal users - MFA for all is the goal.
Q10: Does enabling MFA log users out?
A: Not immediately. Users are prompted at next login or token refresh. Notify users to expect login prompts during rollout.
Q11: Users without smartphones – what to do?
A: Use fallback options like hardware tokens or limited SMS for exceptional cases. Educate users on why the app is more secure.
Q12: Some old apps stopped working after MFA – why?
A: Likely legacy authentication. Update apps to support modern auth or use app passwords temporarily. Phase out legacy apps when possible.
Q13: How do I turn on MFA for all users in Office 365 / Teams?
A: Enable Security Defaults or use Conditional Access policies targeting all users. Security Defaults is fastest for small orgs; Conditional Access is better for fine-tuned control.
Q14: How to check if MFA is enabled for all users?
A: Check Entra ID Sign-in logs, Secure Score, or MFA reports in Entra ID. It shows who is compliant and who still needs setup.
Q15: Is MFA mandatory in Microsoft 365?
A: For admins and privileged roles, yes. Microsoft is pushing MFA for all users, and regulations like HIPAA and GDPR increasingly expect it. Security Defaults enforce it by default for new tenants.
Q16: Is Microsoft MFA enabled by default?
A: New tenants: Security Defaults are enabled by default, requiring MFA via the Authenticator app. Existing tenants need manual activation.