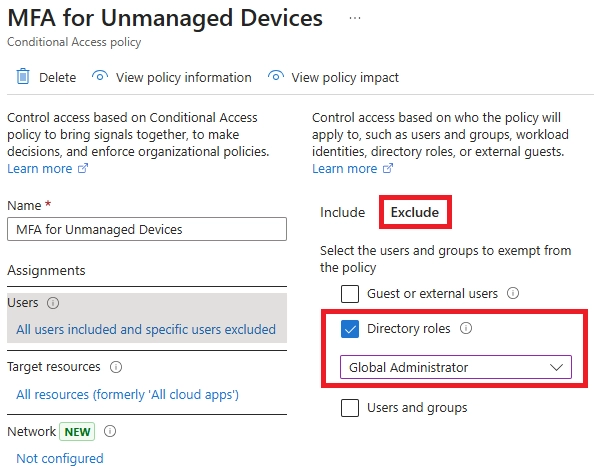
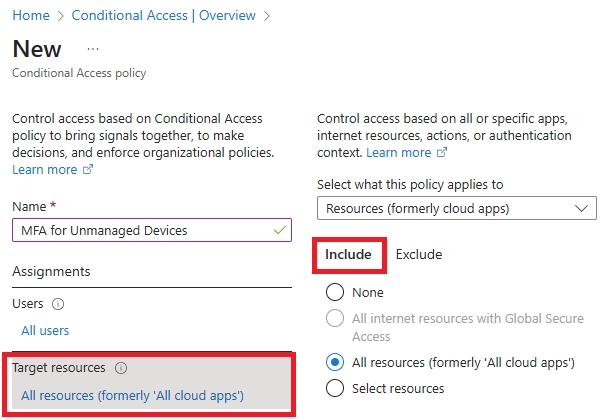
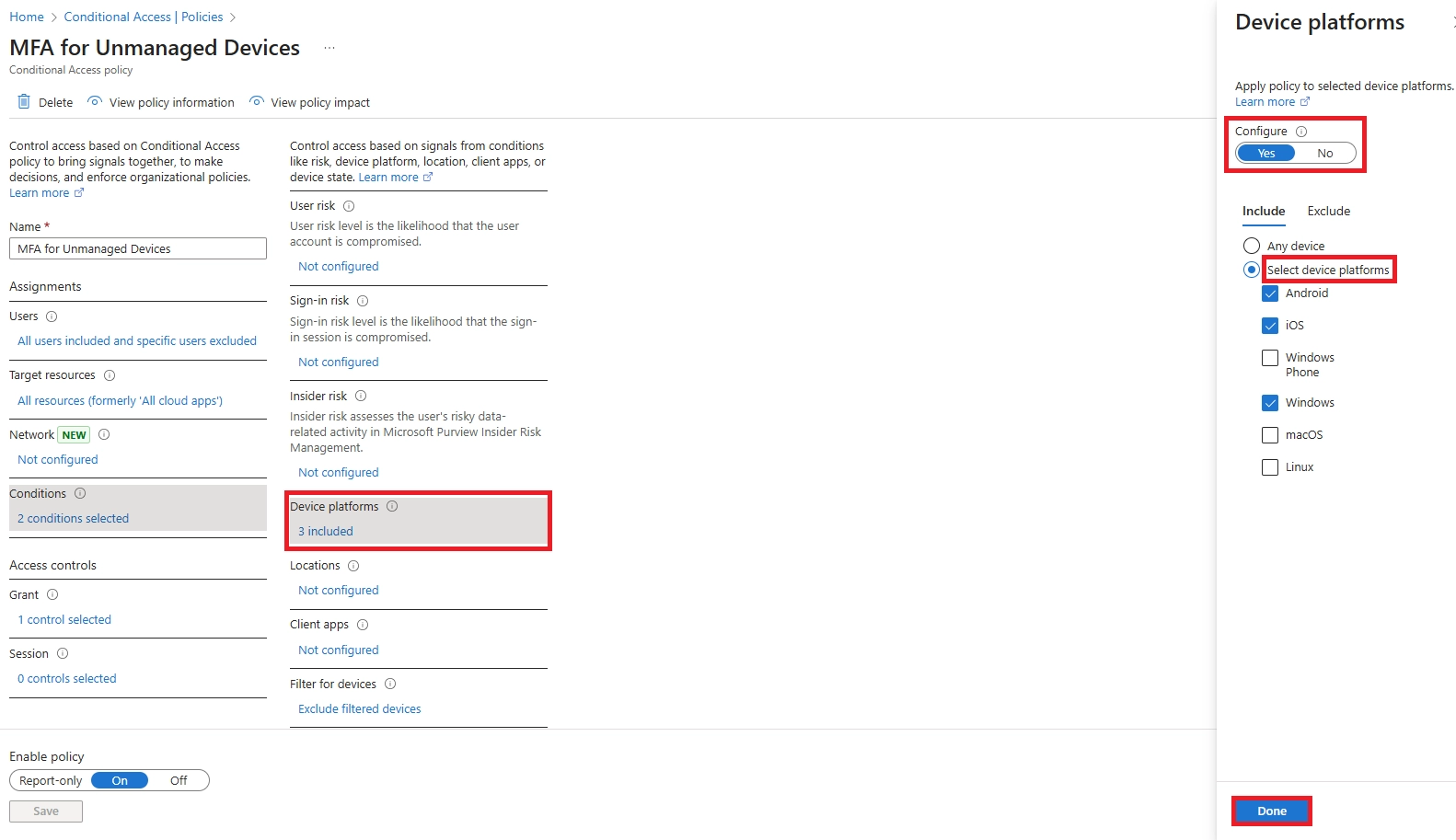
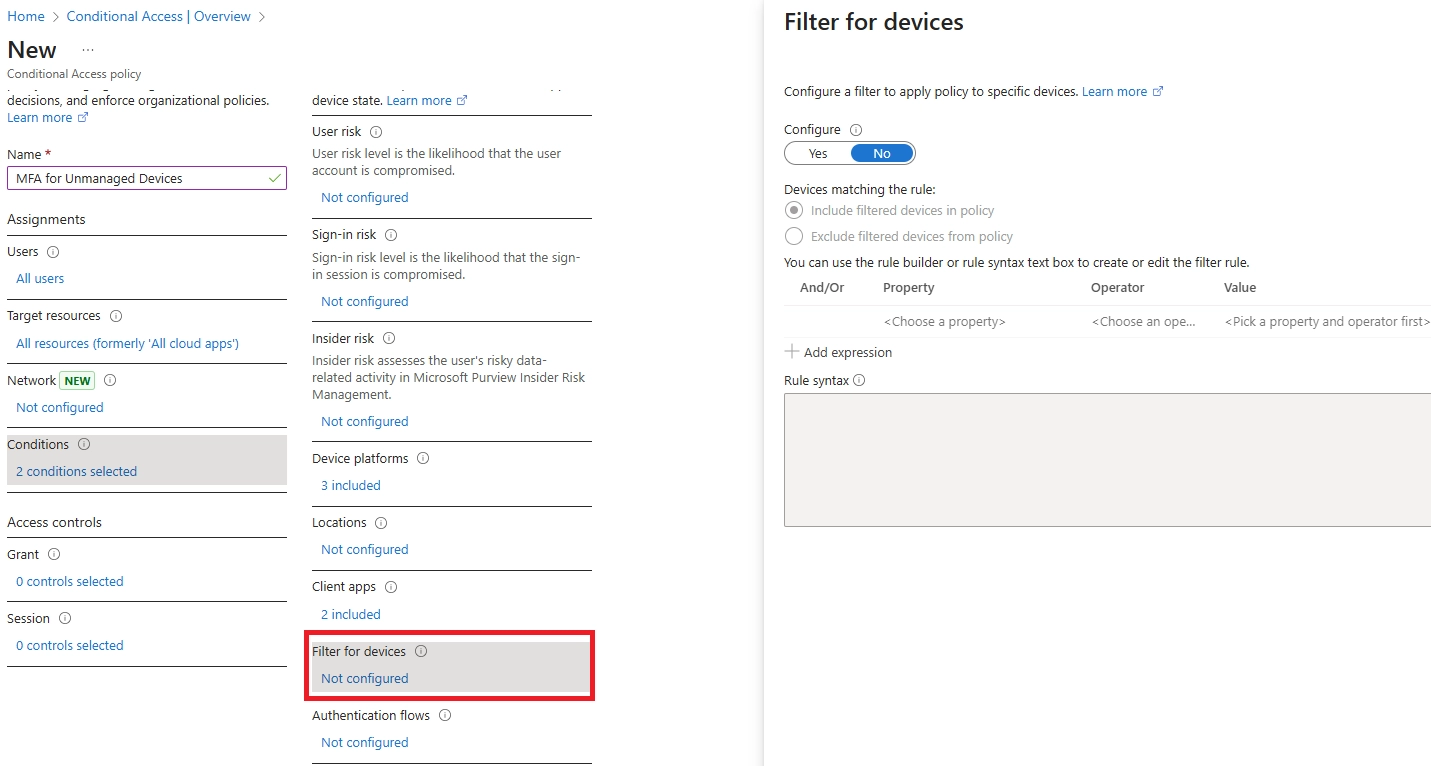
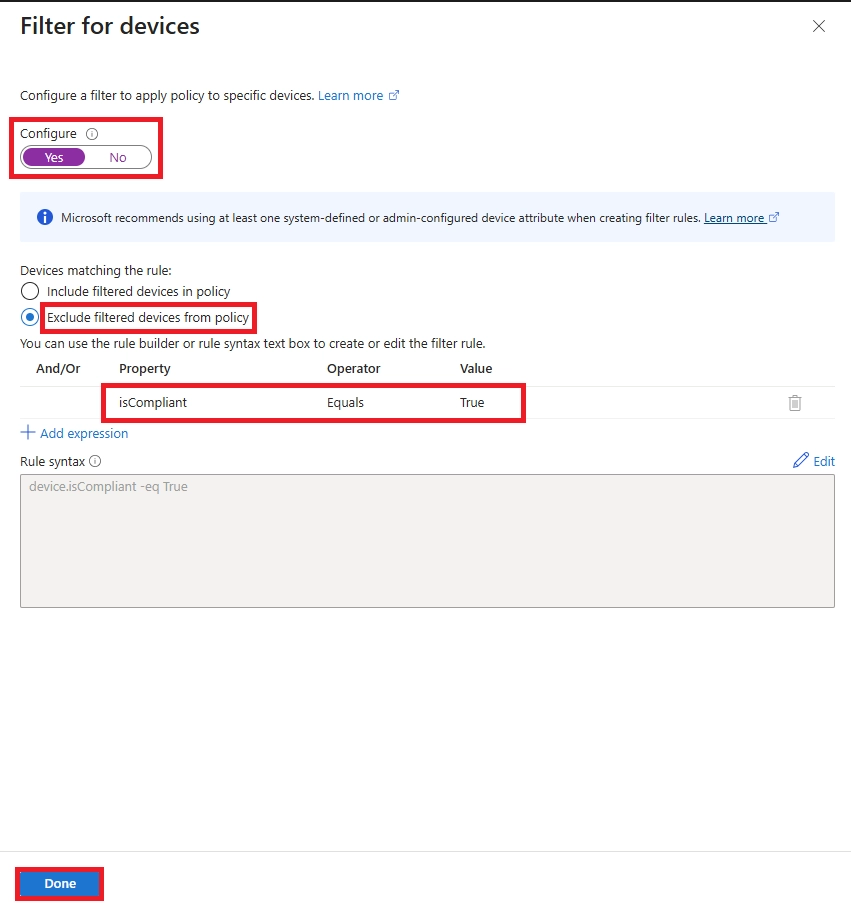
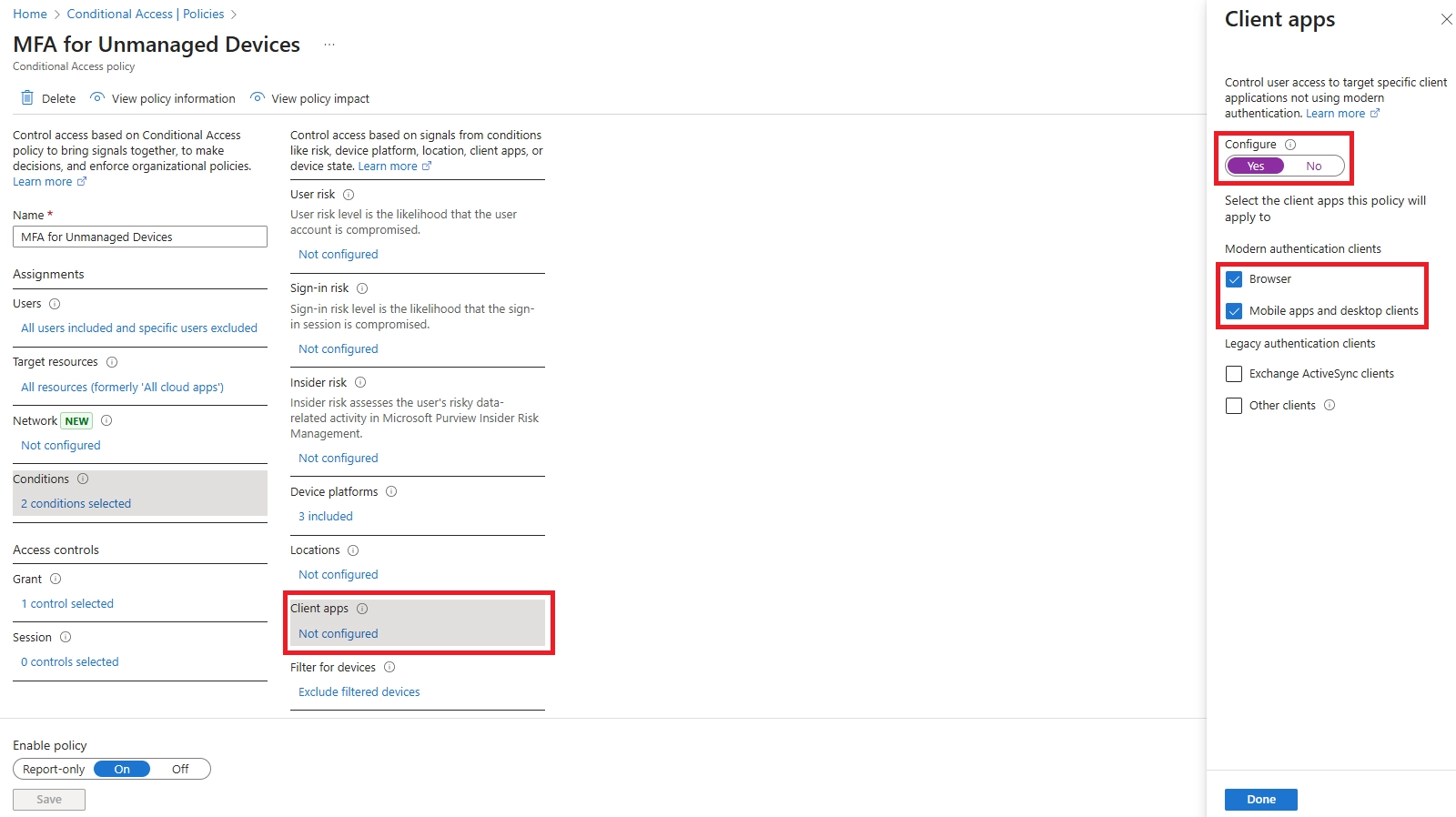
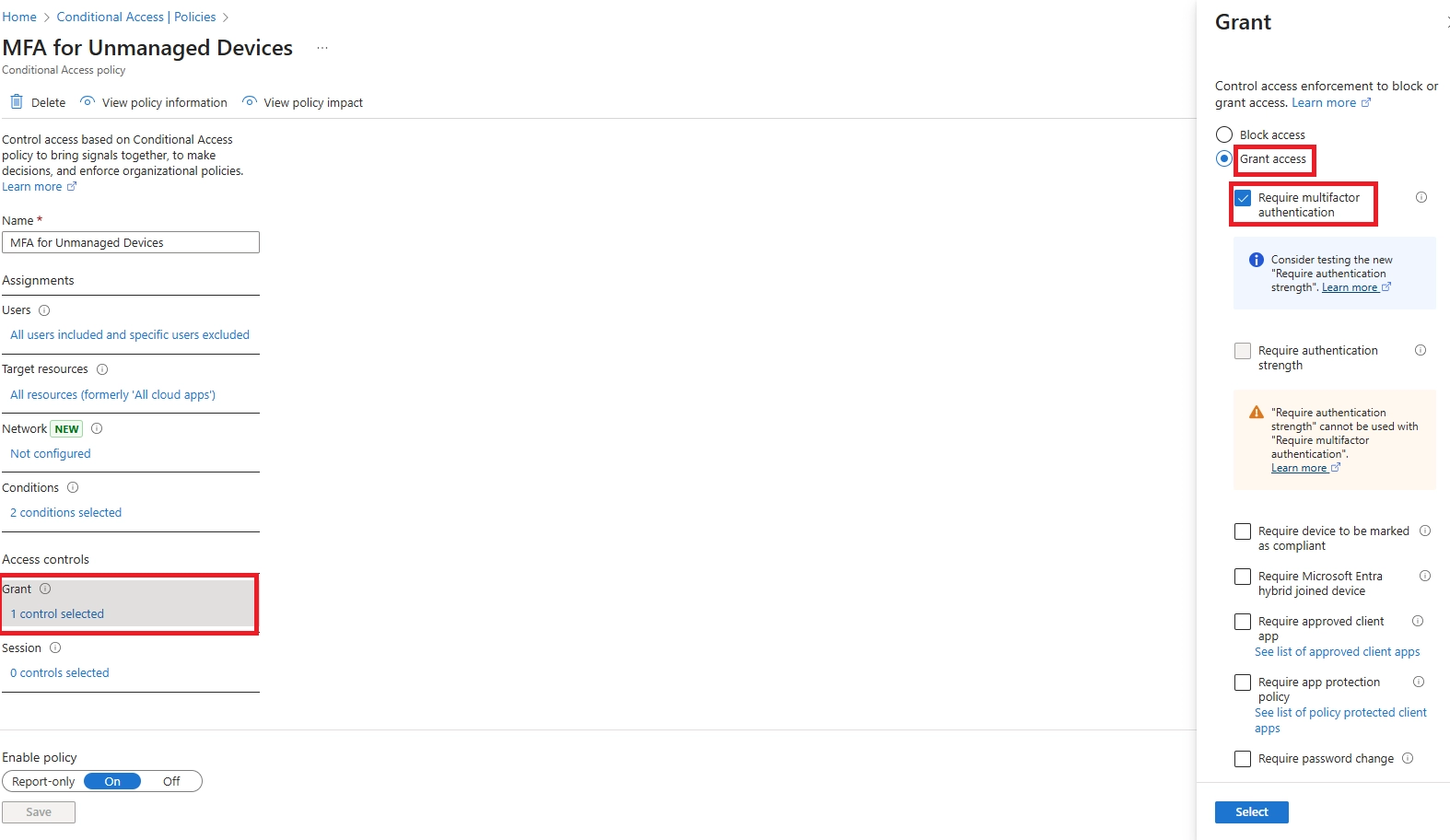
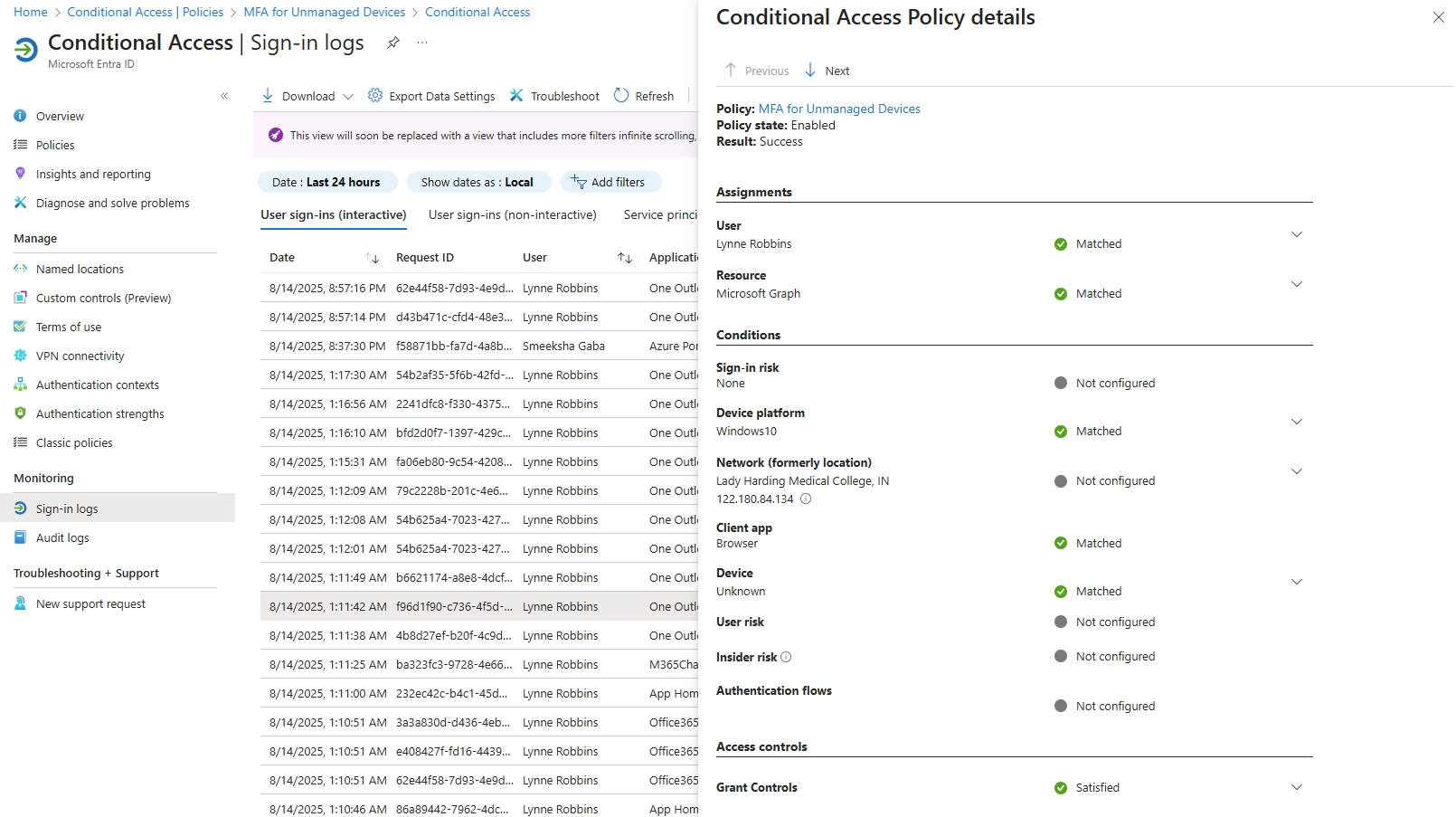
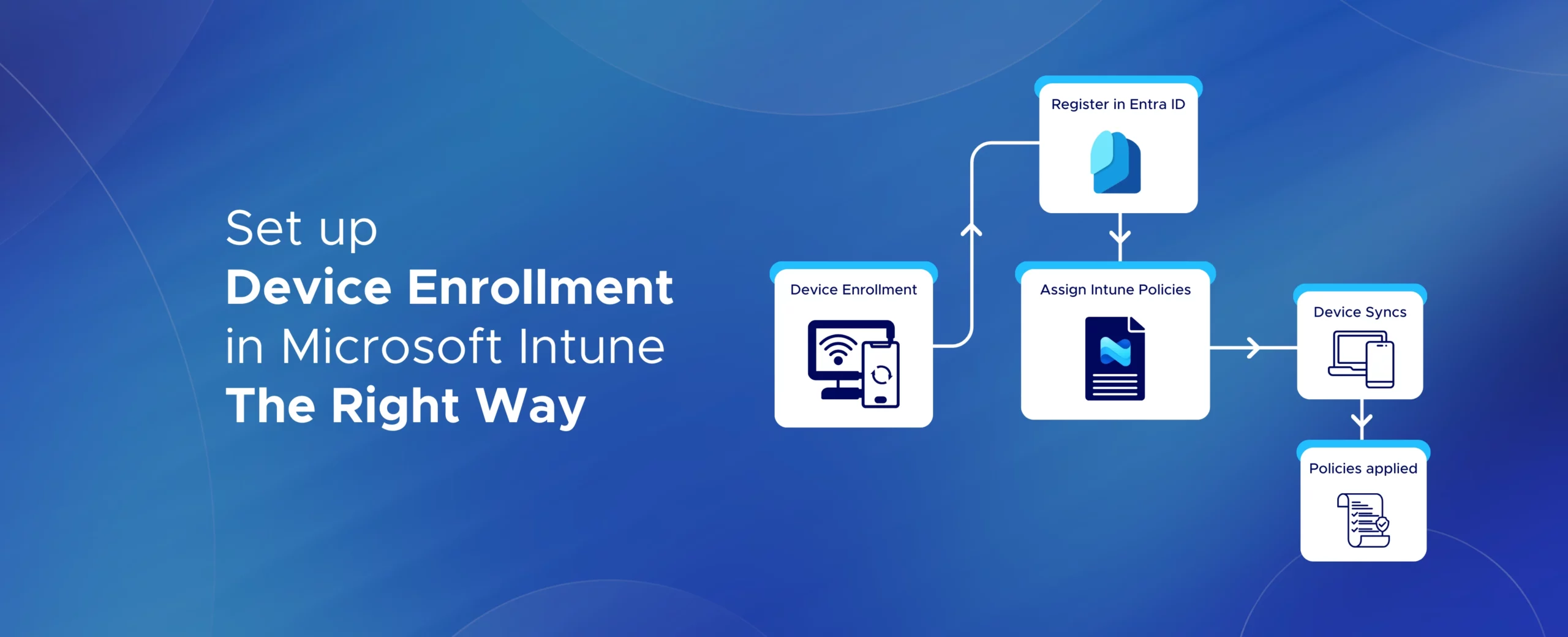
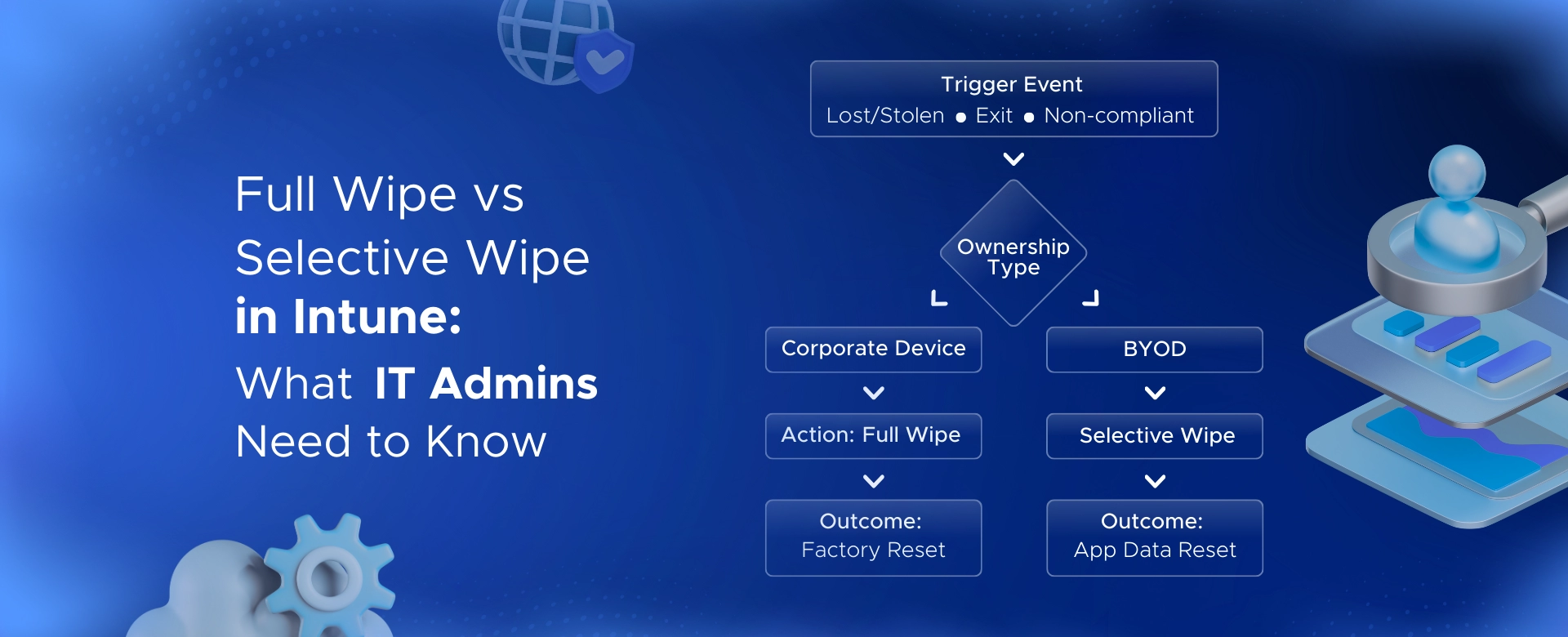
Learn how to set up Microsoft Intune device enrollment, choose the right method for Windows, iOS, Android, and macOS, and avoid common setup mistakes.
Main Menu
Cloud Services
Collaboration and Communication
Security and Compliance
Automation and Development
Digital Workspace
Artificial Intelligence
Overall Microsoft 365 Services
Main Menu
Starfleet Stash App
Asset & Inventory Management App
Penthara Org Chart
- Cloud Services
- Collaboration and Communication
- Security and Compliance
- Automation and Development
- Digital Workspace
- Artificial Intelligence
- Overall Microsoft 365 Services
- Starfleet Stash App
- Asset & Inventory Management App
- Penthara Org Chart